With the development of cloud computing environments, several JavaScript encryption libraries have been suggested for encrypting data in a Web browser [1-5]. JavaScript cryptography is used in mashups to provide secure crossorigin messaging by using fragment identifiers [6]. Furthermore, Mozilla Firefox extensions are written in JavaScript. Further, Adobe Air and Mozilla Prism are full-fledged environments for developing desktop applications in variants of JavaScript. The most popular encryption method is AES [7]. The block cipher is designed for an 8-bit processor. Even though thousands of works provide high performance on processors with a large word size, many high-performance block ciphers that are a considerably more favorable choice for cloud computing environments that need thousands of encryptions within a second have been developed.
In 2013, the low-power encryption algorithm (LEA) was proposed by the Attached Institute of ETRI [8]. This algorithm has software-friendly architecture, and efficient implementation results on a wide range of computational devices from high-end machines, such as personal computers, to low-end microprocessors have been reported in previous papers [8,9]. In this paper, we present LEA implementations on cloud computing, including JavaScript and ASM JavaScript. This result can contribute to widening the usage of the LEA block cipher, particularly in the field of cloud computing.
The rest of this paper is organized as follows: in Section II, we briefly discuss the basic specifications of LEA and target platforms. In Section III, we present the novel implementation techniques. In Section IV, we evaluate the performance of the proposed methods in terms of clock cycles and compare the results with those reported in related works. Finally, Section V concludes this paper.
LEA is a block cipher with a 128-bit block. The key size is 128, 192, and 256 bits. The number of rounds is 24, 28, and 32 for 128-, 192- and 256-bit keys, respectively. The process consists of key scheduling, encryption, and decryption. The following subsection presents the notations of the key scheduling and encryption operations.
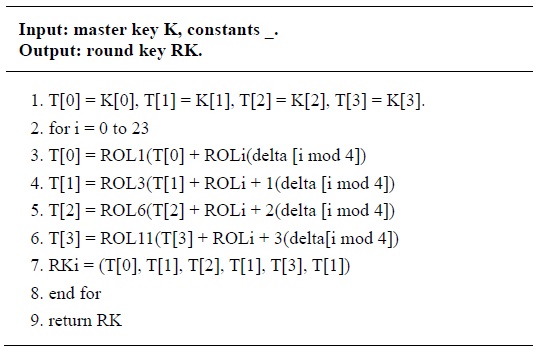
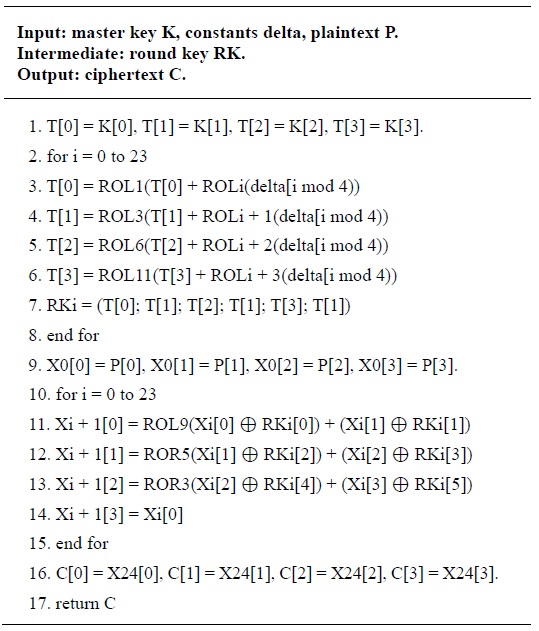
Key scheduling generates a sequence of round keys RKi as follows: it uses several constants for generating round keys, which are defined as delta[8] = {0xc3efe9db, 0x44626b02, 0x79e27c8a, 0x78df30ec, 0x715ea49e, 0xc785da0a, 0xe04ef22a, 0xe5c40957}. The detailed key scheduling process for 128-bit keys is presented in Table 1.
[Table 1.] Key schedule for LEA
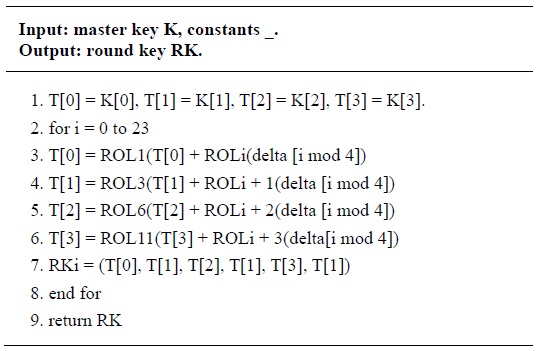
Key schedule for LEA
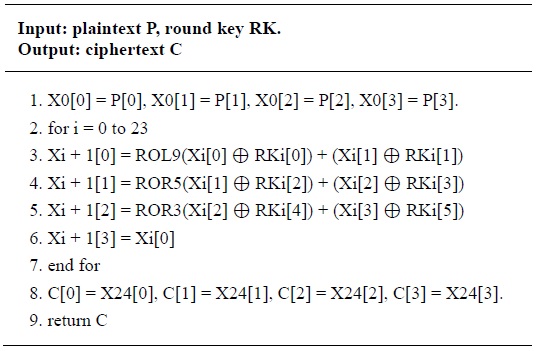
The LEA encryption procedure consists of 24 rounds for 128-bit keys, 28 rounds for 192-bit keys, and 32 rounds for 256-bit keys. For 24, 28, and 32 rounds, it encrypts a 128-bit plaintext P = (P[0], P[1], P[2], P[3]) generating a 128-bit ciphertext C = (C[0], C[1], C[2], C[3]) with 128-, 192-, and 256-bit keys. We omit the description of the decryption procedure because it is simply considered the inverse of the encryption procedure. The detailed encryption process for 128-bit keys is described in Table 2.
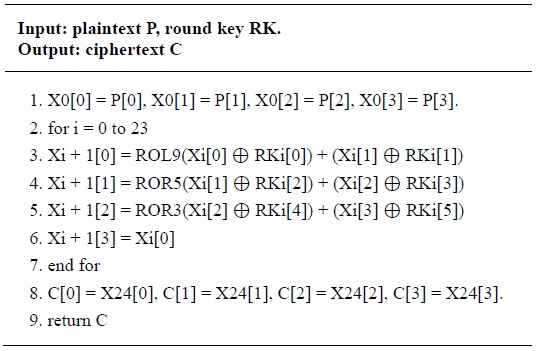
Encryption for LEA
>
A. Target Platform: Cloud Platforms
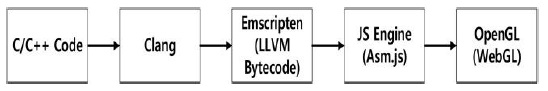
In some applications, client-side encryption is needed before data are uploaded to a server cloud. Since the web browser is becoming the universal tool for interacting with remote servers, it is natural to ask whether existing browsers can perform encryption without installing additional clientside software. In [10], a small, fast AES implementation in JavaScript for a browser has been studied. These researchers used various lookup table approaches and native x86 code for the implementation. Furthermore, they presented several comparison reports on different browsers and ciphers. However, there are no LEA results on cloud computing environments; therefore, in this paper, we provide detailed results for various environments. Programs written in JavaScript and asm.js are compared. Between them, native C-based JavaScript shows higher performance under all circumstances. By using asm.js, we can compile all former C/C++ applications into JavaScript with the support of Mozilla’s Emscripten project. Emscripten takes in C/C++ code, passes it through LLVM, and converts the LLVMgenerated bytecode into JavaScript, also known as asm.js, which is a subset of JavaScript. If the compiled asm.js code is doing some rendering, then it is most likely being handled by WebGL. Thus, the entire pipeline is technically making use of JavaScript. The detailed process is depicted in Fig. 1. This type of JavaScript highly optimizes the source code and shows higher performance than ordinary JavaScript.
>
B. Implementation of LEA Block Cipher
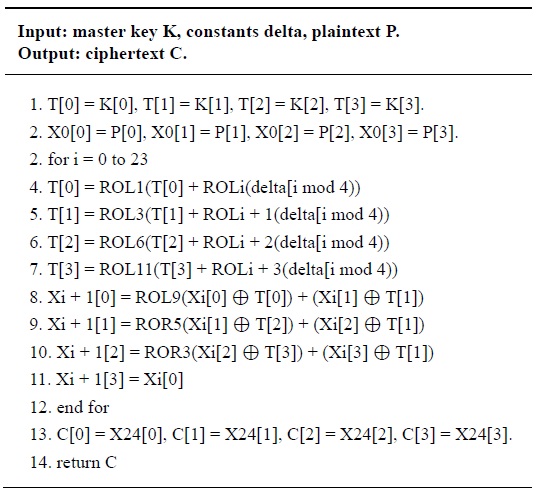
Block cipher consists of key scheduling and encryption operations. Key scheduling generates round keys that can be precomputed offline. After round key computation, the keys are used for the encryption. There are two main approaches to establish block cipher computations. First, an on-the-fly method generates a round key on the spot and then, directly encrypts plaintext with these round key pairs. The main benefits of the method are that storage for the round key is not needed and the source code size is reduced by rolling the encryption and key scheduling within the short length of the program. The algorithm for the on-the-fly method is presented in Table 3.
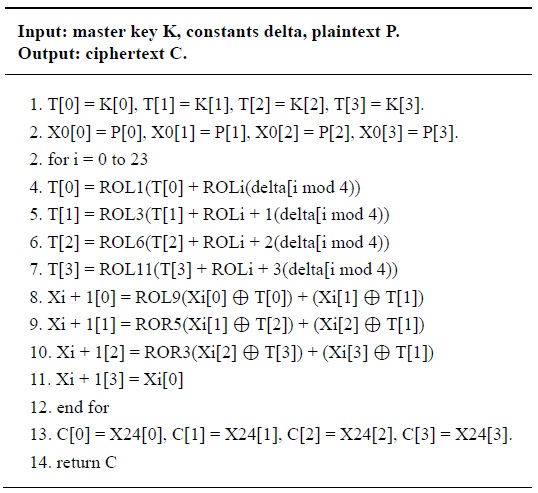
On-the-fly method
Second, a separated computation mode literally executes the key scheduling and encryption processes separately. The round keys are extracted and then, stored into temporal buffers of a certain size. Then, these values are simply loaded and used during the encryption or decryption processes. The advantage of this method is that by eliminating the key generation process, a fast computation time is obtained. The algorithm for the separated mode is presented in Table 4. In this paper, we focused on fast implementation, because cloud computing environments need high-speed performance and the platforms have sufficient capacity to retain round keys and source codes.
[Table 4.] Separated computation method
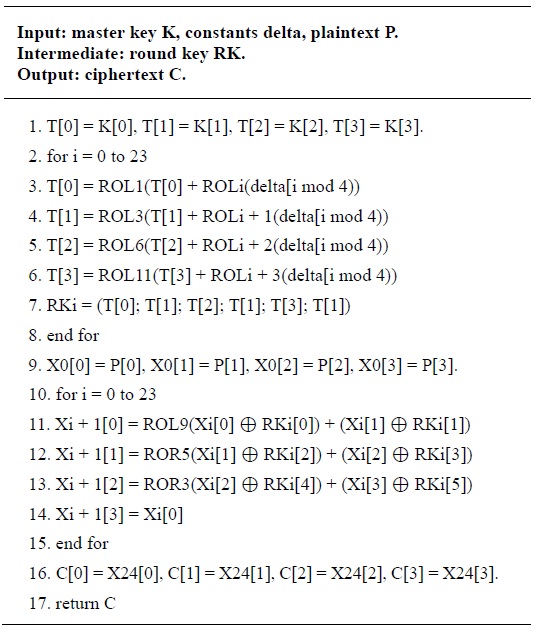
Separated computation method
From the viewpoint of programming, JavaScript is an abstract form of a high-level language that enables users to write programs easily and reduce logical errors. For the LEA implementation, we established basic ARX operations in the Java language because these are basic components of LEA. The variables are explicitly defined in a 32-bit format. manually implemented the unsigned int data type. In Table 5, However, in JavaScript, there is no unsigned int type, so we unsigned int rotation is realized in JavaScript. JavaScript provides unsigned int right shift (>>>) but not left shift (<<). To convert the signed int into the unsigned int type, we executed an unsigned int right shift by zero. The detailed descriptions are given in Table 6. For the addition and bitwise exclusive-or, basic arithmetic and logical operations, such as + and ^ were exploited.
[Table 5.] Rotation method on JavaScript

Rotation method on JavaScript
[Table 6.] Comparison results of JavaScript on desktop
Comparison results of JavaScript on desktop
We tried to unroll the LEA encryption process. The looped process usually presents a small program size but slow performance due to the computation of loop handling. However, we found strange results, which were contradictory to our general knowledge. A detailed discussion of these results is presented in the evaluation section. The program was also executed in a separated form; therefore, first, we conducted key scheduling and constructed whole round key pairs, and then, we conducted encryptions with the round keys. For a higher optimal implementation, we compiled the C/C++ implementation using Emscripten to output JavaScript. This method generates JavaScript from the native C language; therefore, compared with JavaScript, the program is highly optimized. However, the original JavaScript implementation works on various servers and platforms without code modifications, unlike C-based coding.
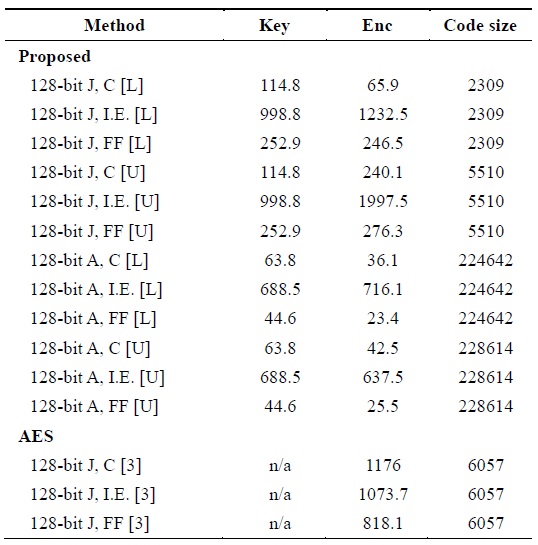
We evaluated the performance of the proposed method on Intel Core i7-3770 powered by 3.4 GHz with 8-GB RAM. We used 64-bit Windows 7 as the operating system, and JavaScript 1.5 and Emscripten 1.12.0 as the development tool and compiler, respectively. The target browsers were Chrome 33.0.1750.154m, Internet Explorer 10, and Firefox 27.0.1. We analyzed performance by measuring the time taken in milliseconds with getUTCMilliseconds() in terms of the browser, language, and loop/unroll modes, and have presented the results in Table 6. For browsers, significant differences were observed. Internet Explorer showed the slowest performance among browsers. The performance of Chrome was faster than that of Firefox with JavaScript but was slower than that with asm.js. Between JavaScript and asm.js, JavaScript was slower than asm.js by about 41%– 90.5%. This implies that irrespective of the web browser, asm.js had better performance but required a considerably large amount of source code and an Emscipten environment.
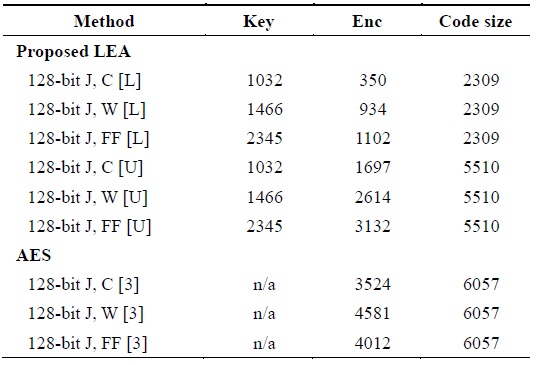
For achieving further improvements, we implemented unrolled and looped versions for LEA and tested both versions in both languages. Strangely, JavaScript always exhibited poorer performance in the case of the unrolled version. We assumed that JavaScript was operated over a virtual machine for wide computability. When the virtual machine launched the program, a long program would generate additional overhead. This would lead to performance degradation from our perspective. Compared with the previous AES implementation, LEA exhibited an improved performance of 94.3% and 69.8% in the case of JavaScript with Chrome and Firefox, respectively, that of 96.9%, 33.3%, and 97.1% in the case of asm.js with Chrome, Internet Explorer, and Firefox, respectively. Only JavaScript with Internet Explorer exhibited 14.8% degradation in performance.
In order to show the compatibility of JavaScript, we measured performance even on a cellphone. The target device was Samsung Galaxy S3 supporting Cortex-A9 and 1.4-GHz quad core with 1-GB RAM. The operating system was Android 4.3. We executed our programs over Mobile Chrome 34.0.1847, Webkit 4.3, and Firefox 28.0.1. The detailed results are presented in Table 7. Among the three browsers, Chrome showed the best performance. We think that Google has highly optimized Chrome to operate over the Android platform. Further, the basic browser of Android, Webkit, showed the second best performance. Finally, Firefox ranked last.
[Table 7.] Comparison results of JavaScript on mobile platform
Comparison results of JavaScript on mobile platform
In this paper, we implemented the LEA algorithm in JavaScript languages. In order to provide efficient implementations, we tried to use JavaScript and ASM JavaScript.
Furthermore, various browsers including Firefox, Internet Explorer, and Chrome were considered. In this study, we also explored the trade-off between code size and speed in cloud computing environments. In the future, we intend to focus on authenticated encryption with the proposed method in various cloud computing environments.