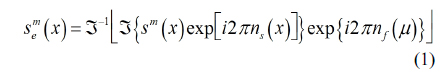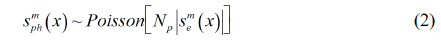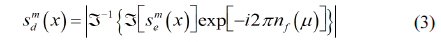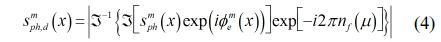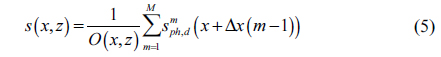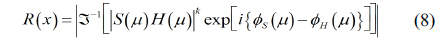In this paper, we propose a nonlinear maximum average correlation height (MACH) filter for information authentication of photon counting double random phase encryption (DRPE). To enhance the security of DRPE, photon counting imaging can be applied because of its sparseness. However, under severely photon-starved conditions, information authentication of DRPE may not be implemented successfully. To visualize the photon counting DRPE, a three-dimensional imaging technique such as integral imaging can be used. In addition, a nonlinear MACH filter can be utilized for helping the information authentication. Therefore, in this paper, we use integral imaging and nonlinear MACH filter to implement the information authentication of photon counting DRPE. To verify our method, we implement optical experiments and computer simulation.
Recently, data encryption techniques have been widely researched [1-11]. Double random phase encryption (DRPE) that is one optical encryption technique has many advantages; easy implementation and high encryption speed [5]. DRPE uses two independent random phase masks, which follow the statistical distribution such as Uniform distribution with support [0, 1] to encrypt the primary data. For decryption, it uses one random phase mask used in the encryption stage as the key information. Thus, if this key information is revealed, the security is destroyed. To enhance the security level of DRPE, a photon counting imaging technique has been applied [6, 7] that follows a Poisson distribution. Due to its sparseness for image sensing, attackers cannot recognize the decrypted data successfully. However, under severely photon-starved conditions, the primary data cannot be decrypted with the key information correctly. Therefore, to visualize and authenticate the primary information, three-dimensional (3D) imaging techniques such as integral imaging [12] and correlation filters [13, 14] can be utilized. In integral imaging, multiple images with different perspectives can be used for 3D reconstruction. In this paper, we use integral imaging and nonlinear maximum average correlation height (MACH) filter to obtain more accuracy of information authentication for optical encryption compared with a nonlinear correlation filter.
The paper is organized as follows. We present 3D photon counting DRPE concept and information authentication using nonlinear MACH filter in Section II. Then, we show the experimental results for proving our proposed method in Section III. Finally, we conclude our method with a summary in Section IV.
II. INFORMATION AUTHENTICATION OF 3D PHOTON COUNTING DRPE USING NONLINEAR MACH FILTER
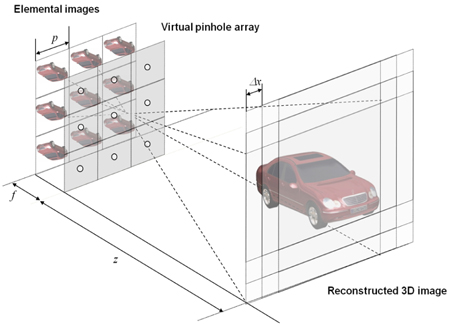
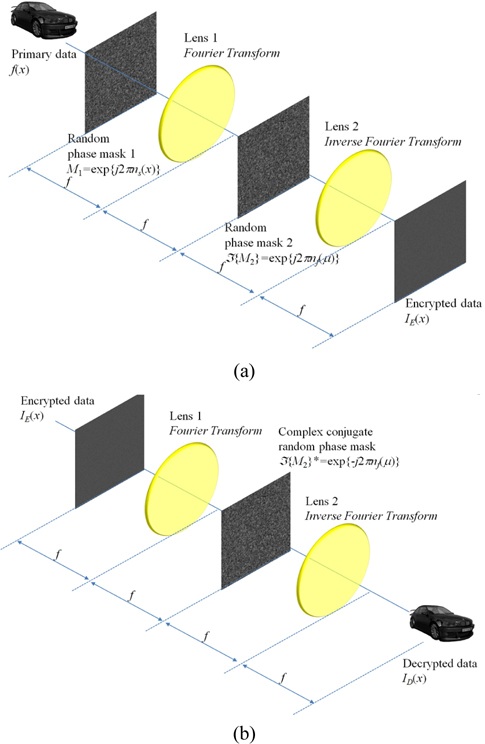
In photon counting DRPE, the decrypted data may not be authenticated well. To improve the information authentication, a 3D integral imaging technique can be applied because it uses multiple data to reconstruct 3D data as shown in Fig. 1. Therefore, this technique can be applied to DRPE as shown in Fig. 2. In this paper, for simple computation, we use one-dimensional notation only. The encryption process of DRPE can be described by the following:
where
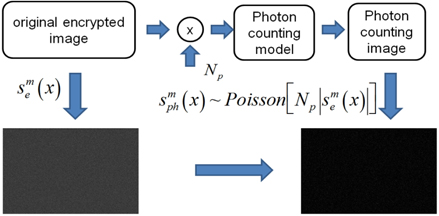
Now, we have the encrypted data for the primary data. To enhance the security level, we can apply the photon counting imaging technique to the amplitude component of the encrypted data. In general, the photon counting imaging technique can be utilized for detecting the information of objects in low light level environments. Its characteristic seems to be sparse detection. Thus, using sparse detection of the photon counting imaging technique, we can enhance the security level of optical encryption. Photon counting detection can be modeled by statistical distribution such as Poisson distribution since events of photons occur rarely in unit time and space [15]. Figure 3 illustrates the concept of photon counting detection using a statistical distribution. To extract photons from the original scene, Poisson random generation with the expected number of photons
where
where
where
where
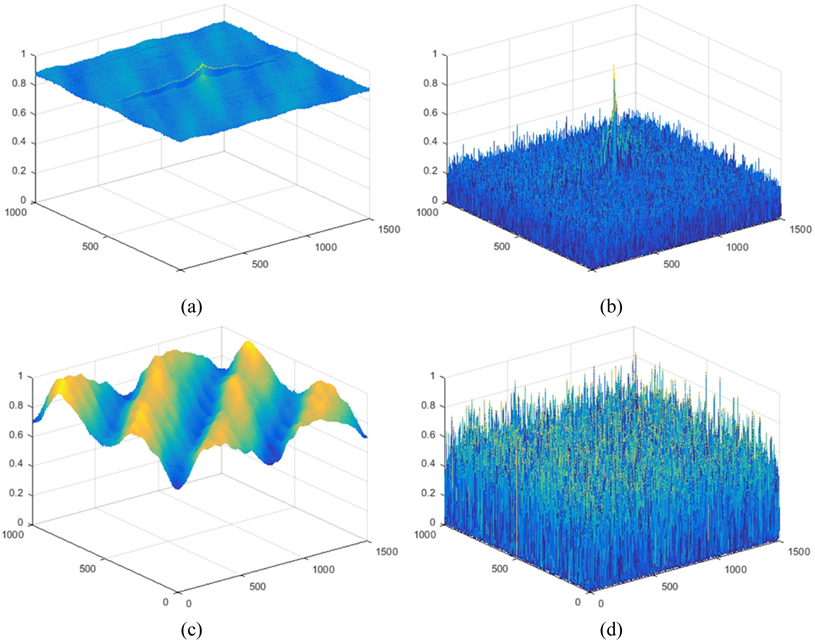
To authenticate the information, we need one particular filter design algorithm known as Maximum Average Correlation Height (MACH) filter [14], which has been found to be robust over a broad range of conditions such as variations in the object’s scale, its orientation, background clutter and noise. This filter uses many reconstructed 3D images at different reconstruction depths as the training data as shown in Fig. 4. In the Fourier domain, the MACH filter is given by the following:
where
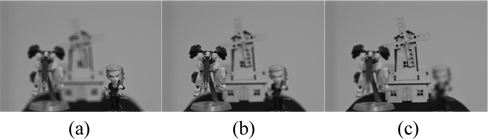
Using Eq. (1) with primary image as shown in Fig. 5(a), the conventional encrypted image can be generated as shown in Fig. 5(b). The resolution of primary image is 1350(H)×1350(V) pixels. To obtain multiple 2D images with different perspectives, synthetic aperture integral imaging (SAII) is used. The camera array consists of 10(H)×10(V) cameras. The focal length of the camera is 50 mm. The distance between cameras is 2 mm. Perfectly decrypted image that is the same as Fig. 5(a) can be obtained using Eq. (3). Figure 5(c) shows a photon counting encrypted image using Eq. (2). We can notice that the pixel sparse exists in the image by adjusting
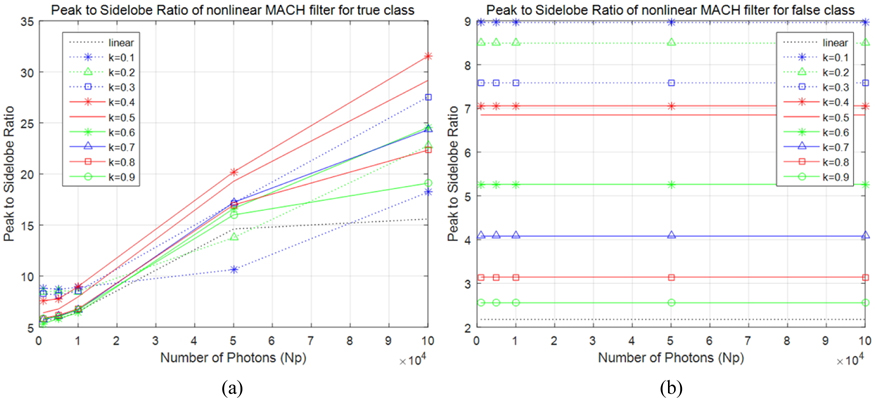
We have presented information authentication of 3D photon counting DRPE using a nonlinear MACH filter. In conventional DRPE, since the number of photons is sufficient for recognition, when attackers know the key information, the encrypted data can be decrypted easily. To avoid this attack, photon-limited DRPE can be utilized but the decrypted data may not be recognized well due to lack of photons. Thus, for information authentication, a nonlinear correlation filter may be used to enhance the recognition rate. However, in severely photon-starved conditions, nonlinear correlation filter may not obtain the better results. In addition, for 3D encrypted data, this correlation filter cannot recognize the information well because it is for 2D data. On the other hand, MACH filter can have the better performance for 3D data because it uses much training data with different depth information. In addition, to improve the information authentication, a nonlinear MACH filter can be used. Therefore, adjusting parameters of MACH filter and nonlinear coefficient