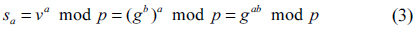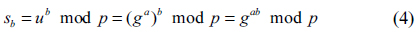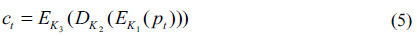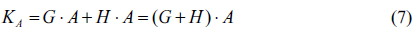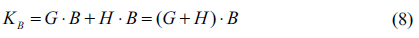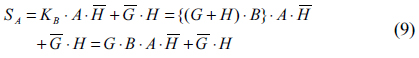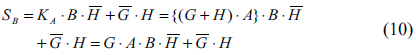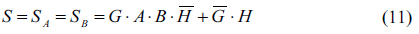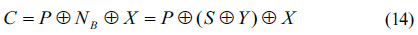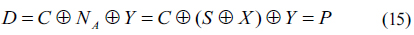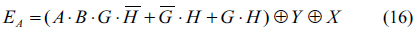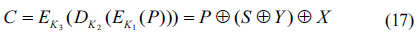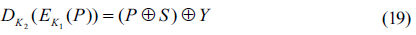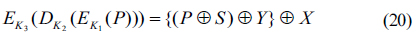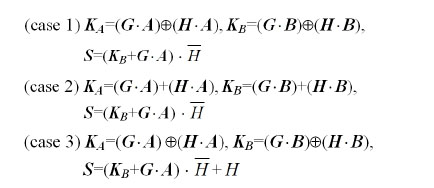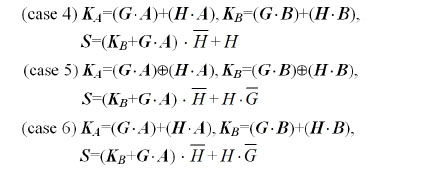With the rapid development of communication networks, there have been strong demands for information security, thus this trend brings a continuing search for more secure encryption algorithms. But, digital information of the public network tends to be not secure against unauthorized attack because of the fast development of computers. For the purpose of protecting information against hacking, various cryptographic algorithms have been introduced. A simple method to enhance the security strength is to increase the key length. Another method is to use an algorithm having multiple security keys, for example double keys or triple keys, in the cryptosystem. In order to meet these conditions, thus advanced algorithms such as D-H (Diffie-Hellman) secret key sharing [1], 3DES (triple Data Encryption Standard) [2] and asymmetric RSA public key cryptography [3] were introduced to enhance security strength. However, the electronic cryptosystem is slow and requires much time to compute the encryption procedure for the long key length and huge amount of data. On the contrary the optical cryptosystem has advantages of fast signal processing and vast data handling due to the inherent 2-D signal processing capability of optics and thus the parallelism achievable with optical signal processing. Another advantage of an optical cryptosystem is the potential for a large key length, rendering brute force attacks almost impossible. For these reasons, there has been a growing interest in optical cryptographic systems and several optical encryption techniques have been proposed in recent years [4-13]. Also, an optical XOR logic-based encryption has been introduced as one of these effective encryption algorithms [14-16].
In order to establish a secure cryptosystem, the most important thing is that the encryption key must not be known to unauthorized persons and the key must be hard to break by attacks. The symmetric private key algorithm such as DES has a risk that attackers may cryptanalyze the symmetric key because this type of cryptosystem has only one key. To solve this problem, asymmetric cryptography such as the D-H algorithm was introduced. In this algorithm, two users unknown to each other can set up a public key and share a secret key by their public key exchange cryptography. However, this shared secret key can be disclosed by “meet in the middle” attack because this shared secret key is used to encrypt messages by applying symmetric cryptography. So as to realize higher level of security, an advanced algorithm such as 3DES or asymmetric RSA public key cryptography was introduced as a means of solving this problem, which uses double key encryption technique. In our previous studies on the optical cryptosystem, a triple DES algorithm was proposed in an optical way based on dual XOR logic operation [17] and an optically modified D-H key exchange protocol was reported recently [18].
In this paper, an asymmetrical cryptosystem combined with D-H secret key sharing and triple DES and its optical implementation are proposed. Also, numerical simulation and performance analysis are discussed. The objective of this paper is to analyze how secure the proposed cryptosystem is and how efficient the proposed optical implementation is. Section II is organized as three parts. The first and second parts overview the D-H secret key sharing algorithm and the triple DES algorithm. In the third part, the proposed asymmetric cryptosystem combined with D-H secret key sharing and 3DES is explained. Section III describes the optical implementation of the proposed asymmetric cryptosystem. In Section IV, numerical simulation proves the feasibility of the optical system and performance analysis is described by showing results of the decryption error rate according to possible attacks inferred by the open public keys. Finally, the conclusions are briefly summarized in Section V.
2.1. Diffie-Hellman Secret Key Sharing Algorithm
In 1976, Diffie and Hellman introduced a secret key sharing algorithm, which is focused on exchanging cryptographic secret keys. The D-H secret key sharing algorithm is a method for two users to exchange a shared secret key over a public network without any prior secrets between them. They can encrypt private messages into cipher messages by using this symmetric shared key. The D-H secret key sharing algorithm is as follows.
Let the users be named Alice and Bob. First, they agree on two prime numbers
Now, both Alice and Bob compute their shared secret keys
Alice and Bob can now use their shared secret key
In the case of optics, it is very difficult for the D-H key method to be implemented by optical means due to two main reasons. The first one is that there is no proper method to perform modulo arithmetic by optical techniques. The second is that it is hard to represent a prime number on an optical device properly. In spite of these difficulties, we proposed an optical D-H secret key sharing method by modifying the conventional D-H key secret key sharing protocol [18]. In the proposed method, modulo arithmetic was mathematically replaced by an XOR logic operation. Therefore, the XOR logic-based encryption operation which is regarded as a kind of modulo two addition could be implemented simply by an optically realizable system. Specifically, the XOR-only encryption scheme is perfectly secure if and only if the key data is perfectly random and never reused.
The DES was the first symmetric block cipher protocol which was first issued as a standard in 1977 by the American National Standard Institute (ANSI). It encrypts plain text data in 64-bit blocks by using a 56-bit secret key. DES has been one of the most successful and widely used secret key cryptographic systems. However, ever since DES was released for public cryptosystems, some cryptographers have argued that the security strength of DES would not be sufficient in present days due to its short key length. In order to overcome this problem, many efforts were made to enhance DES. Recently, Triple DES (3DES) has been adopted as a temporary standard and is incorporated in several international standards. 3DES is the name now most often given one popular form of multiple DES applications and is known as Encrypt-Decrypt-Encrypt (EDE) and TDEA (Triple Data Encryption Algorithm). In general usage, 3DES algorithms use three independent security keys. This means that cryptanalysis requires triple computational efforts compared to DES. However, most 3DES algorithms use two independent security keys by using the third encryption key the same as the first encryption key. This option provides also more security than simply DES encrypting twice, because it protects against “meet in the middle” attacks. To acquire the maximum security in the 3DES algorithm, each key is assigned to a different authority so that the decryption cannot be performed. The resultant 3DES cipher text is much harder to break. The 3DES algorithm is as follows.
Assume that 3DES uses three independent keys as
Eq. (5) represents DES encryption of plain text (
About optical implementation of 3DES, we suggested a modified 3DES algorithm based on XOR logic operations [17]. In the proposed method, a triple encryption using double keys was used in a special way so as to avoid the key sharing of the double encryption with two keys.
2.3. Proposed Asymmetric Cryptosystem Combined with D-H Secret Key Sharing and 3DES
In the D-H secret sharing cryptosystem, there is a possibility that the shared secret key may be disclosed by “meet in the middle” attacks. But, the 3DES algorithm is very robust against these “meet in the middle” attacks. If we hide the shared secret key information by encrypting that key and make double encryption of the shared secret key, then more enhanced security strength will be acquired although attackers know the open public keys. With this idea, we propose an asymmetric cryptosystem combined with D-H secret key sharing and 3DES, and we also suggest an optical implementation of the proposed method by applying the logic-based optical processing such as AND, OR and XOR operations. The asymmetric cryptographic algorithm proposed in this paper can be described as follows.
1. Alice and Bob agree on and make two public numbers
2. Alice chooses two distinct random numbers
3. Similarly, Bob chooses two distinct random numbers
4. Alice computes a shared secret key by some logic operations of Bob’s first open public key
5. Similarly, Bob computes a shared secret key by some logic operations of Alice’s first open public key
6. Now both Alice and Bob have the same shared secret key, namely
7. Alice computes her second public key
8. Similarly, Bob computes his second public key
9. Alice encrypts a plain text
10. Bob decrypts a cipher text
As shown in Eq. (11), the shared secret key is composed of multiple logical encryptions by two public random numbers
From Eq. (16), it is very important to understand the level of security in the proposed cryptosystem. The encryption key consists of six different random numbers, where these random numbers make a combination result by AND, OR and XOR logic operations. Even if we know the public keys
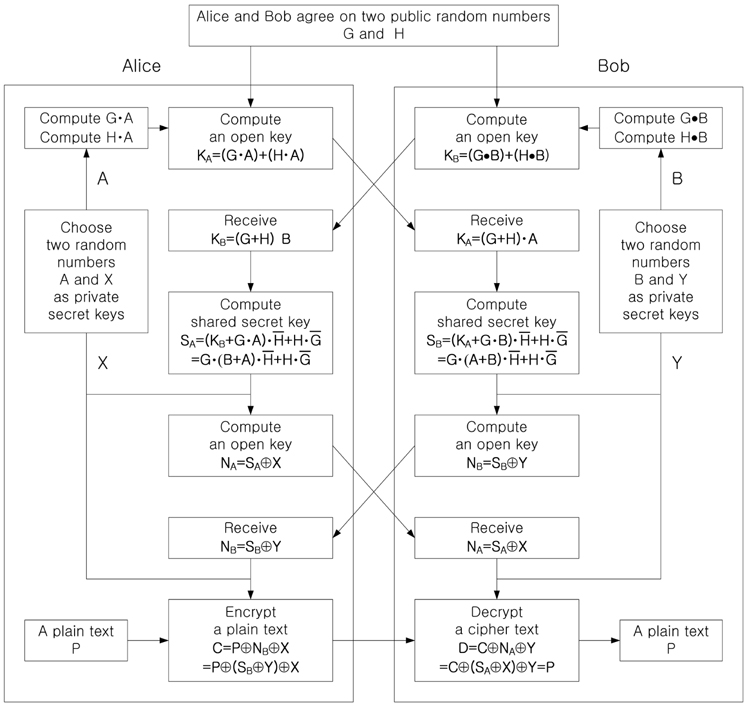
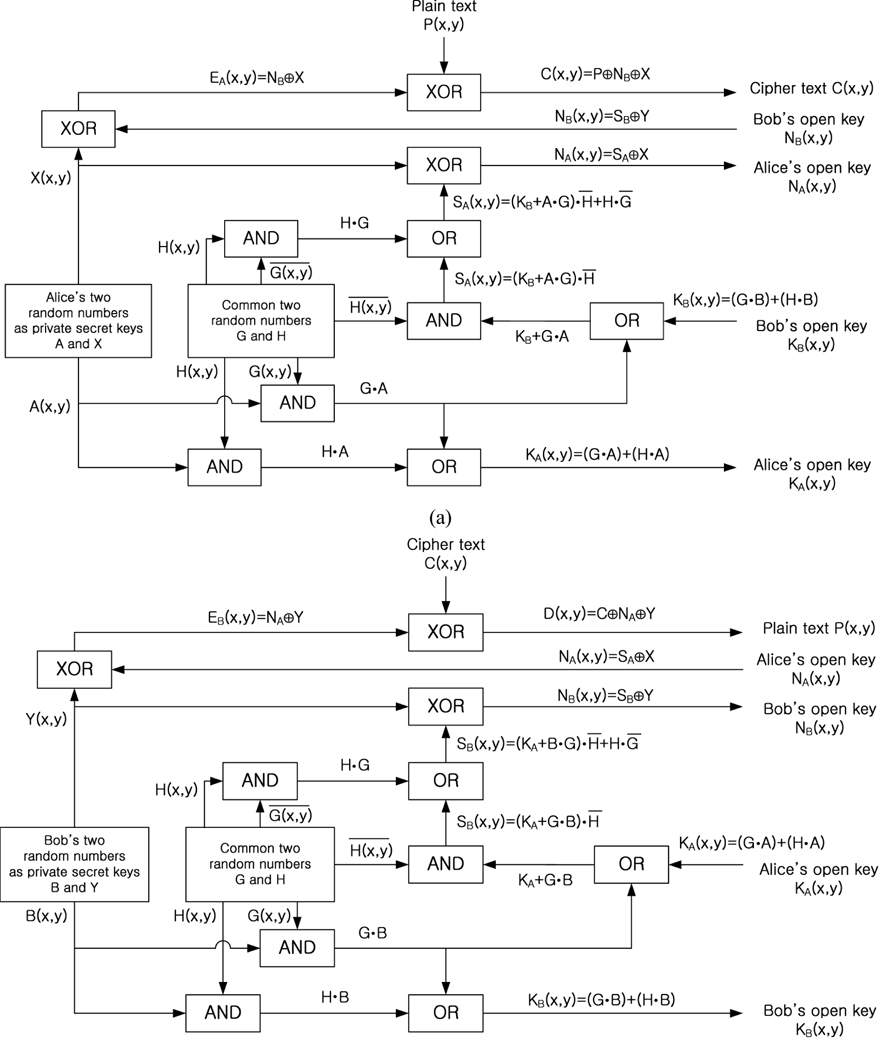
Figure 1 shows the procedure of the proposed asymmetric cryptosystem combined with D-H secret key sharing protocol and 3DES by using logic-based processing, and Fig. 2 shows the flow charts for the proposed cryptography method. As shown in Fig. 1 and Fig. 2, assume that Alice and Bob agree on two random numbers
In this paper, the proposed asymmetrical cryptosystem uses the concept of 3DES algorithm. According to Eqs. (5) and (14) in the proposed method, a cipher text is given by
From Eq. (17), encryption and decryption processes of 3DES can be explained as
Here, encryption and decryption functions are substituted by XOR logic function and three independent keys are as
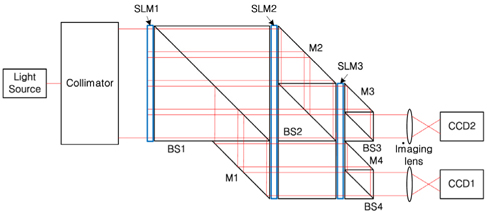
The main idea of the proposed cryptosystem is to perform a more secure asymmetrical cryptographic system which transmits the encrypted public keys and the cipher text. This cryptographic algorithm is accomplished by combination of D-H secret key sharing and 3DES with triple keys. Referring to the block diagram shown in Fig. 1, the optical asymmetric cryptosystem is proposed with optical components such as mirror (M), beam splitter (BS), lenses, spatial light modulator (SLM) and charge coupled device (CCD). Figure 3 shows the optical schematic for implementing the proposed asymmetric cryptosystem, which is based on the dual free-space interconnected AND, OR and XOR logic operations for binary data. In this configuration, the optical setup contains four Mach-Zehnder type interferometers in order to generate the first public key and a shared secret key simultaneously, and this optical schematic can be used to generate the second public key and the cipher text simultaneously too. Also, this setup can be used for the decryption process. A collimated light is divided into two light paths and we combine these divided lights into one light path by four beam splitters BS1, BS2, BS3 and BS4. As for displaying data inputs, this architecture is composed of three SLMs. When the light continuously passes two SLMs in series, optical AND logic operation is obtained by inner production pixel by pixel. On the other hand, the combining beam splitter performs the optical OR logic operation by adding two lights in parallel. As a result, the integration of these processes is equivalent to the optical XOR logic operation obtained by the combination of two logic ANDs and one logic OR. Finally, two CCDs are used for recording the resultant lights.
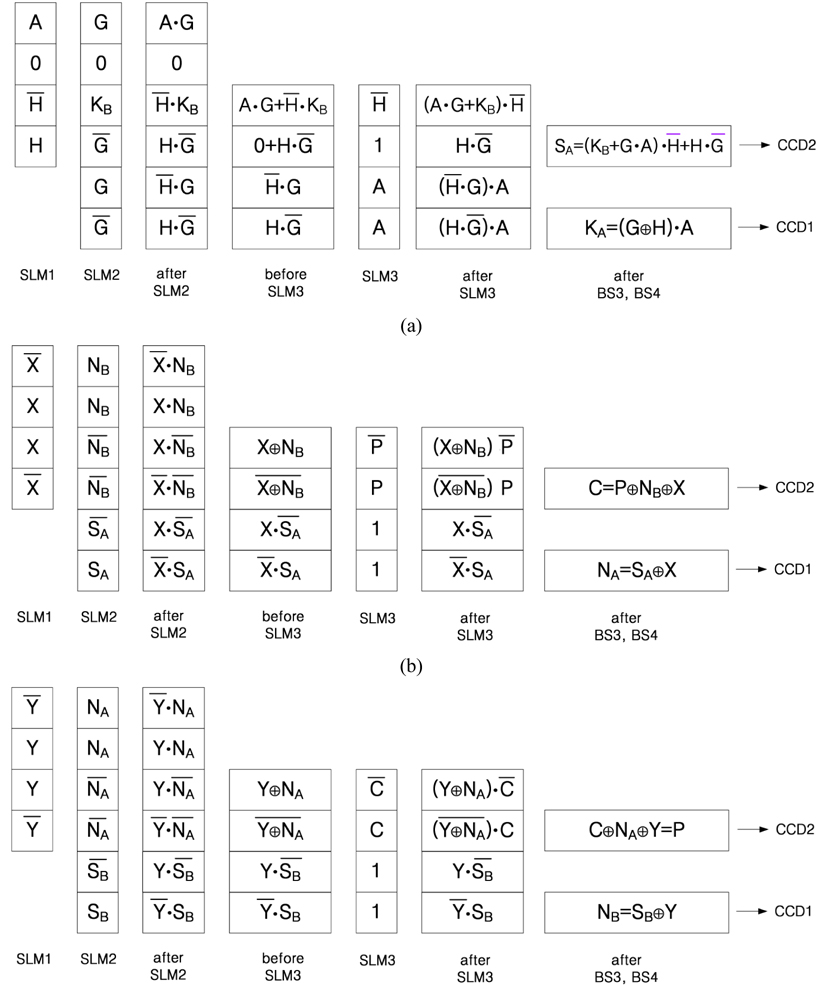
In order to explain operating principles of the optical configuration, the flow charts shown in Fig. 2 are considered. First, let us consider Alice’s first public key and shared secret key generations shown in Fig. 2(a). In Fig. 3, SLMs display two public random numbers
One of the advantages of the proposed optical cryptosystem is that it has dual outputs simultaneously. One is to generate the first public key and the shared secret key, the other is to generate the second public key and the encrypted cipher text. Also, the encryption optical setup can be used as decryption optical setup only by changing the inputs of SLMs. Another advantage of this optical setup is that it is convenient to alter the private keys at their own discretion. Changing of those private keys does not affect encryption and decryption of a plain text, because the encryption and decryption keys are changed according to the other user’s private key change directly.
IV. NUMERICAL SIMULATION AND PERFORMANCE ANALYSIS
4.1. Numerical Simulation of the Proposed Optical Asymmetric Cryptosystem
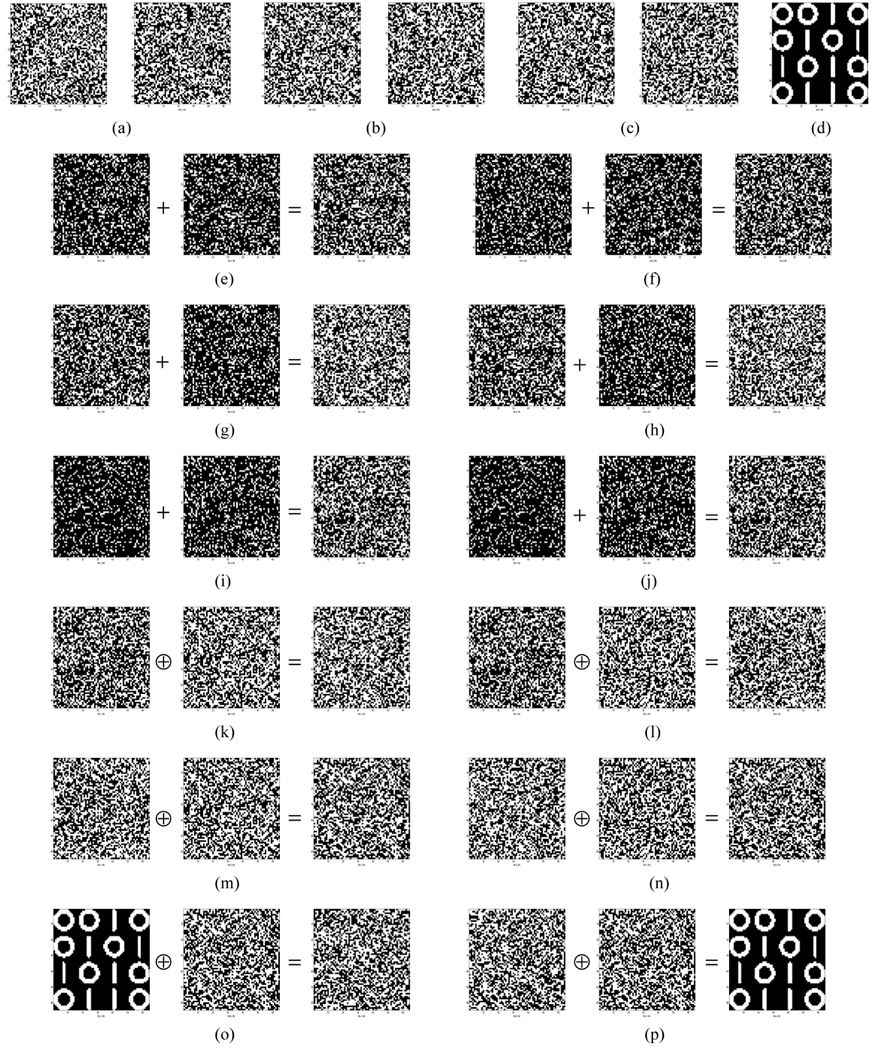
Generally, an optical information processing system has an inherent merit of 2-D data processing in parallel and fast processing time. This means that the optical cryptosystem with 2-D arrayed data can perform huge data processing, and the optical cryptosystem with 2-D arrayed key can have very long key length. In this paper, we perform the simulation with 2-D arrayed data format which consists of binary 64 × 64 bits for convenience, where white areas have value of ‘1’ and black areas have value of ‘0’ numerically. Also, this implies that the security key length of the cryptosystem has 64×64=4,096 bits which is very much longer key length compared to the conventional 1-D key length of electronic cryptography. Figure 5 shows numerical simulations for performing the feasibility of the proposed asymmetrical cryptosystem. Fig. 5(a) shows two randomly generated numbers
For the purpose of verifying the proposed asymmetric cryptosystem algorithm and of showing the effectiveness in the proposed optical cryptosystem, the security performance of the proposed system is analyzed. The first consideration for analyzing cryptographic algorithms is security strength of the cryptosystem, which depends on the length of the key. Assuming there is no better way to break the cryptosystem, other than to try every possible key with a brute force attack, a long encryption key takes more time than a short key to find the correct key. Generally, if a key has N-bits key length, 2N attempts are required for a successful brute force attack. Moreover, because the optical cryptosystem has inherently a key length of N×Μ bits with 2-D array, 2N×Μ brute force attacks are required. In this paper, the key length of the cryptosystem is set to be 64×64=4,096 bits so that 264×64 = 24,096 brute force attacks are required, which needs very huge attack time to find the correct key.
In addition to the 2-D arrayed longer key length, the proposed asymmetrical cryptosystem uses the 3DES algorithm. The D-H secret key sharing algorithm has the disadvantage of suffering from the “meet in the middle” attack problem. But, the 3DES algorithm using even double keys also provides more security than simply DES encrypting twice, because it protects against “meet in the middle” attacks. From Eq. (17), the cipher text
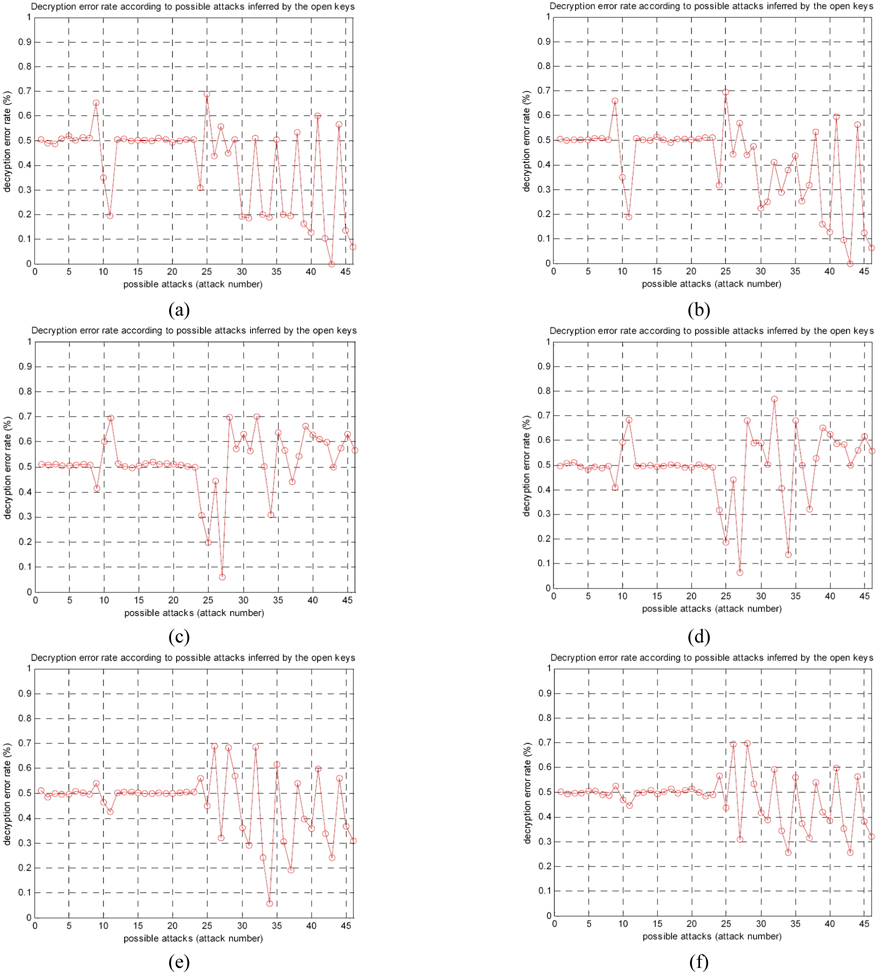
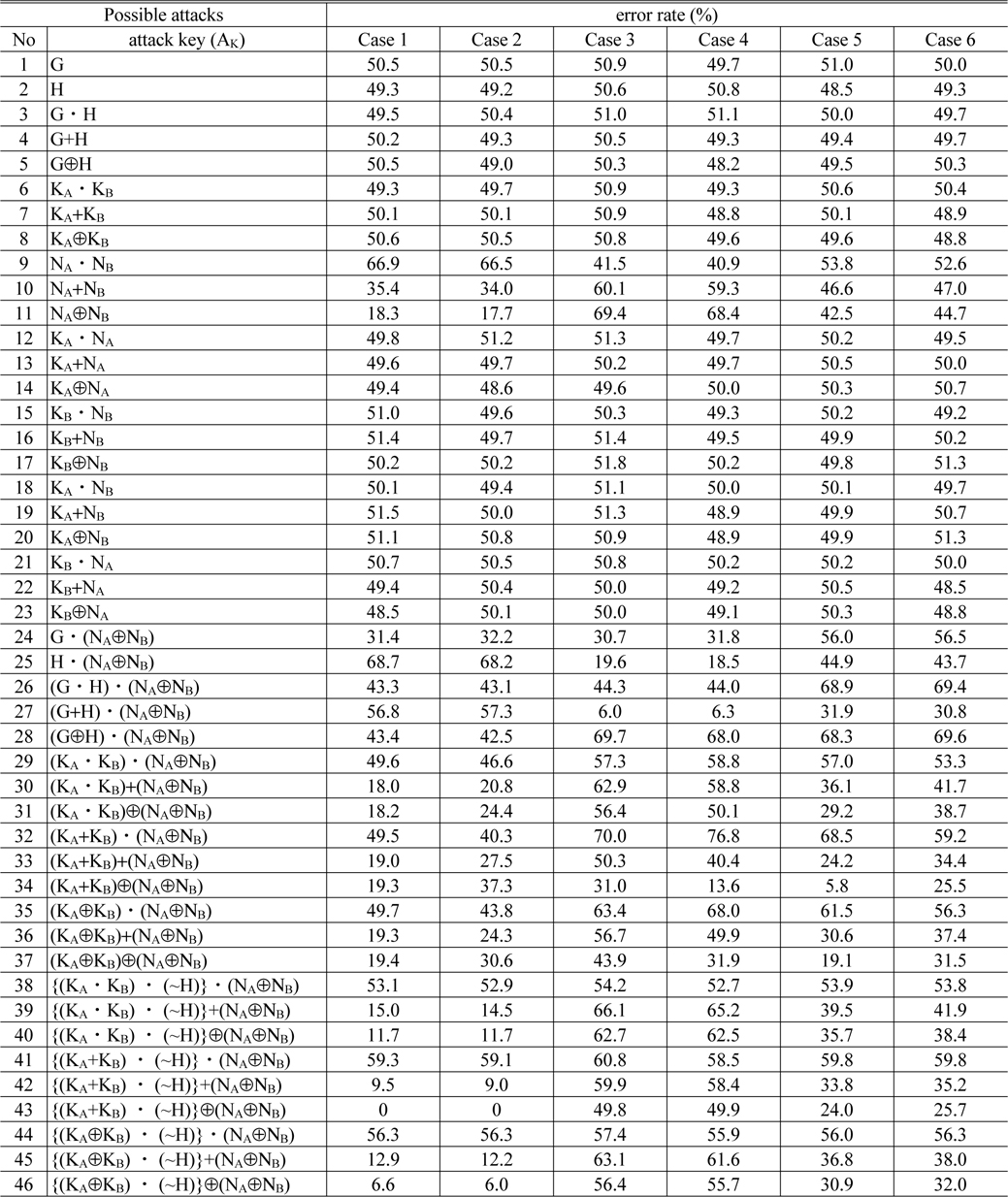
In order to examine “meet in the middle” attack with a cipher text, we analyze decryption error rate according to possible attacks inferred by the open public keys
For each case, Table 1 shows the average value of decryption error rate according to possible attacks from attack key 1 to attack key 46, where the average is calculated by 10 times trials to the corresponding attack case.
[TABLE 1.] Decryption error rate according to possible attacks inferred by the open public keys
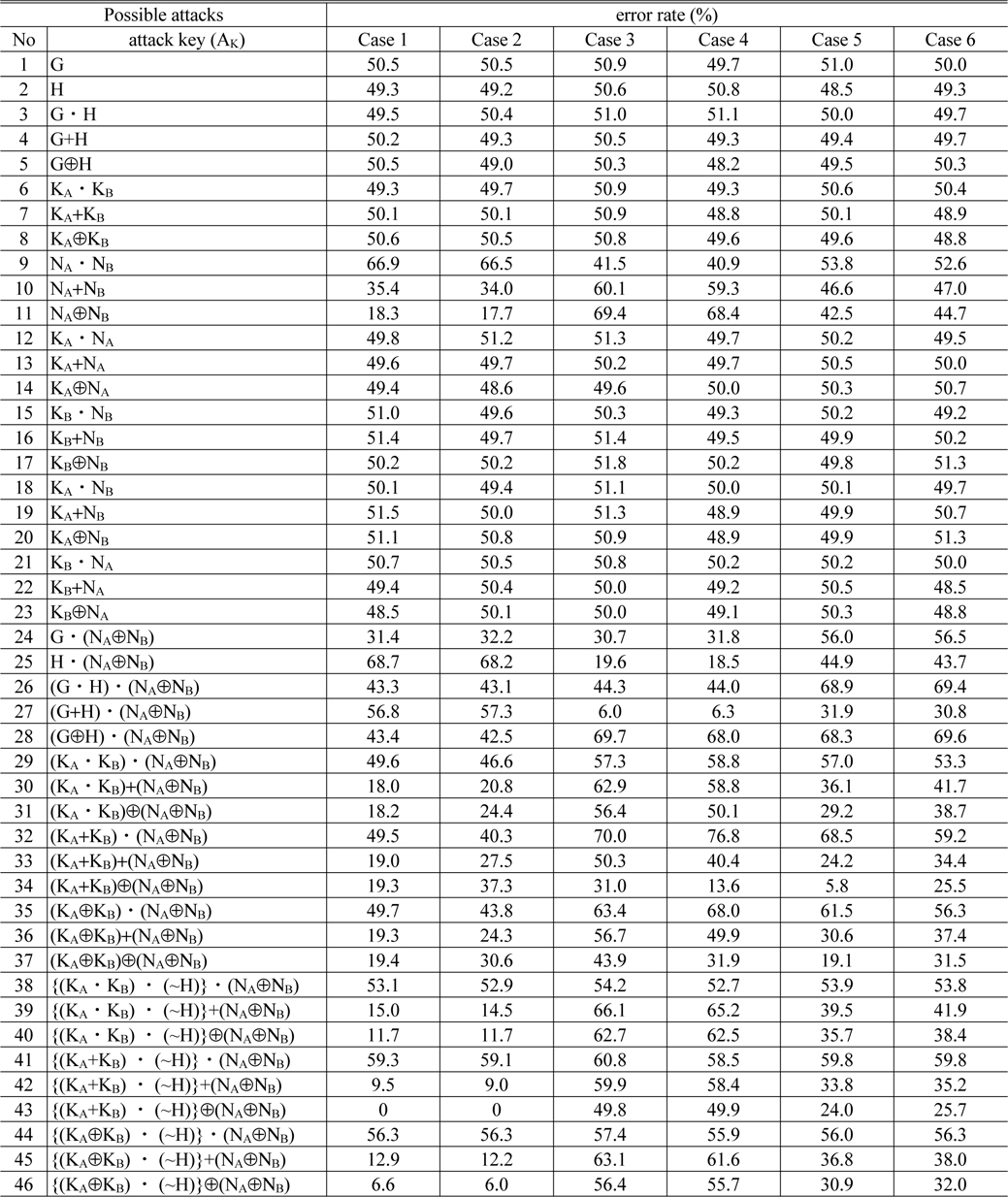
Decryption error rate according to possible attacks inferred by the open public keys
From Figs. 6(a) and (b), the original plain text
In this paper, a novel asymmetrical cryptosystem combined with D-H secret key sharing and triple DES and its optical implementation are proposed. The proposed optical cryptosystem is realized by performing free-space interconnected optical logic operations such as AND, OR and XOR which are implemented in Mach-Zehnder type interferometer architecture. The advantage of the proposed optical architecture provides dual outputs simultaneously by generating the first public key and the shared secret key or by generating the second public key and the encrypted cipher text. Also, the encryption optical setup can be used as a decryption optical setup by changing only the displaying inputs of SLMs. The proposed cryptosystem can provide higher security strength than the conventional electronic algorithm, because the proposed method uses 2-D array data which can increase the key length surprisingly and uses 3DES algorithm which protects against “meet in the middle” attacks. Also, by using 3DES with independent three keys, XOR logic-based triple key encryption technique is implemented for enhancing security strength. Another advantage of the proposed asymmetrical cryptosystem is that it is free to change the user’s two private random numbers in generating the public keys at any time. Numerical simulation and performance analysis verify that the proposed asymmetric cryptosystem is effective and robust against attacks for the asymmetrical cipher system.