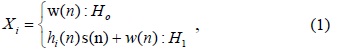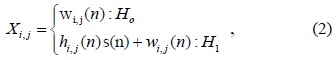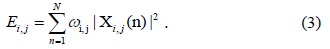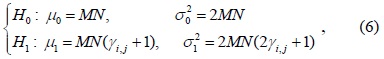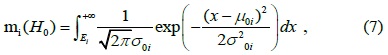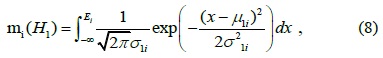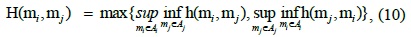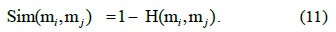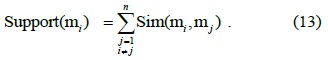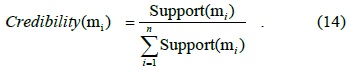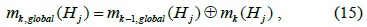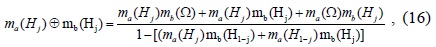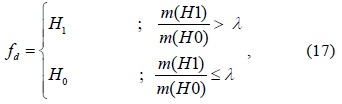In cognitive radios, spectrum sensing plays an important role in accurately detecting the presence or absence of a licensed user. However, the intervention of malicious users (MUs) degrades the performance of spectrum sensing. Such users manipulate the local results and send falsified data to the data fusion center; this process is called spectrum sensing data falsification (SSDF). Thus, MUs degrade the spectrum sensing performance and increase uncertainty issues. In this paper, we propose a method based on the Hausdorff distance and a similarity measure matrix to measure the difference between the normal user evidence and the malicious user evidence. In addition, we use the Dempster-Shafer theory to combine the sets of evidence from each normal user evidence. We compare the proposed method with the k-means and Jaccard distance methods for malicious user detection. Simulation results show that the proposed method is effective against an SSDF attack.
According to the Federal Communication Commission, most of radio spectrum is underutilized, which leads to inefficient usage of the allowed spectrum [1]. Cognitive radio (CR) technology has been studied as an approach to increase spectrum efficiency by allowing dynamic spectrum access. A major challenge in CR is spectrum sensing, which is used to detect whether a spectrum is occupied by a licensed user (LU). The sensing performance of a secondary user (SU) degrades because of the presence of channel effects such as fading, shadowing, and the hidden terminal problem. These problems are overcome by the use of cooperative spectrum sensing, which involves an exchange of local sensing results between multiple SUs by using a centralized or decentralized fusion center to arrive at the final decision regarding the presence or absence of an LU [2].
However, multiple SUs sending their local sensing result to the fusion center also increases the number of security risks. One of the security issues is the spectrum sensing data falsification (SSDF) attack, where a malicious user (MU) purposely reports false local sensing data to the SUs, thereby negatively influencing the overall decision. In [3], the authors discussed the security threats from passive and active points of view; the authors discussed the physical layer security for a passive attack; and MU detection is introduced for an active attack by using signal detection techniques to reduce the system interference. In [4], the authors used a weighted sequential probability test (WSPRT) to identify MUs on the basis of their reputation, which is determined by the rating assigned to every user. In [5], the authors proposed a correlation of utilization and shadow fading to detect malicious users. In [6], the authors proposed a scheme where the maximization of the secondary secrecy rate is subject only to the maintenance of a certain level of quality of service for a primary user via the interference threshold. In [7], the authors considered cooperative spectrum sensing with the existence of an MU; the authors formulated the detailed detection performance to analyze the impact of incorrect information on the sensing. Further, an authentication mechanism is proposed to filter out the incorrect information from the system. In [8], the authors addressed the problem of cooperative spectrum sensing in a CR network: in the presence of misbehaving CRs, an iterative expectation maximization is formulated and solved for hypothesis verification and radio classification. Similarly, in [9], the authors proposed a cross-layered approach to provide SUs with the ability to differentiate between a primary user and an MU by using a hidden Markov model at the media access control (MAC) sublayer. In [10], the authors presented a decentralized scheme for detecting MUs in cooperative spectrum sensing.
The authors of [11] and [12] explored the DempsterShafer (D-S) evidence theory in cooperative spectrum sensing but have not taken into account the MU’s activity. In [13], the authors proposed a reliable method based on clustering cooperating sensors; a cluster with no malicious user was found by using a fast sensor search algorithm. The authors’ model is based on trusted sensors and uses only the results obtained by these sensors; thus, the information of malicious sensors is not considered in the spectrum decision process. In [14], the authors utilized both the advantages of the D-S evidence theory combined with an enhanced weighted stage and the capability of robust statistics used for the elimination of MUs. In [15], the authors proposed a robust cooperative spectrum sensing scheme based on the D-S theory and the calculation of the trustworthiness degree. In [16], the authors developed a trust-based data aggregation scheme to tackle an MU attack; the scheme combined firsthand and second-hand sensing evidence to guarantee performance and adopt a static game model to discourage MUs from fake reporting. In [17], the authors proposed a similarity degree that calculated the reliability of evidence and then combined reliable sets of evidence sent by honest users, but the authors did not consider the physical position of the users, and MUs were found on the basis of its cardinality, which was practically unreliable.
In this paper, we propose a method using the Hausdorff distance and a similarity measure matrix. First, the Hausdorff distance is used for measuring the difference between two sets of evidence, and then, the similarity measure matrix is used for calculating the similarity between each normal user’s evidence and identifying MUs. The credibility (reliability) of MUs is less than that of normal users, and by using this value, we can remove the MUs. Finally, after removing the MUs, we use the D-S evidence theory to combine the normal users and estimate the performance of cooperative spectrum sensing.
The rest of this paper is organized as follows: In Section II, we describe the system model of the proposed system. In Section III, we describe the proposed cooperative spectrum sensing-based Hausdorff distance method and the D-S evidence theory. In Section IV, we discuss the simulation results. Finally, we conclude the paper in Section V.
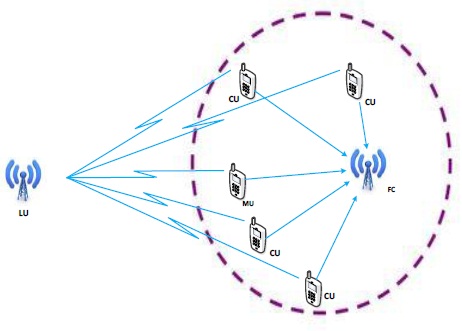
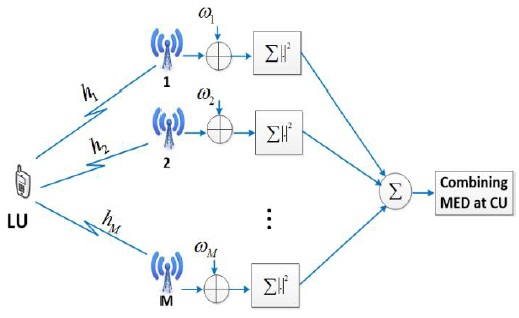
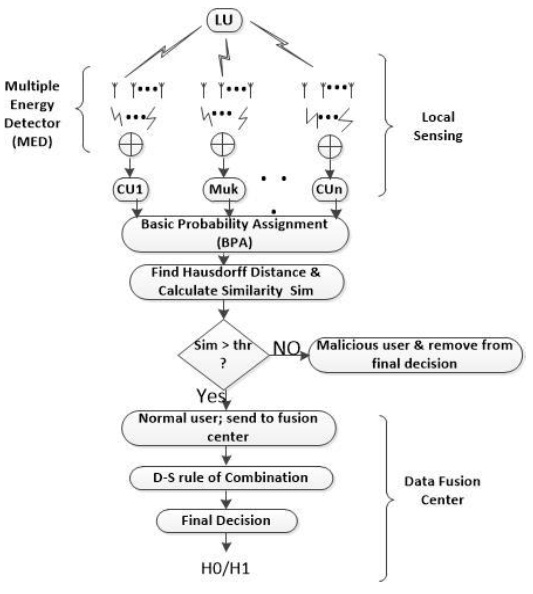
We consider a CR network, which consists of a LU, cognitive user (CU), MU, and fusion center (FC), as shown in Fig. 1. In the proposed system, we consider a multiple energy detector (MED), which has M energy detectors, each having a single antenna; the result of these antennas is combined at the CU by using the equal gain combining (EGC) method, as shown in Fig. 2.
In the first step, each CU performs local sensing by using MED. The local sensing at each CU (with a single energy detector) can be formulated as a binary hypothesis as follows:
where
In the case of MED, local sensing can be formulated as follows:
where
The signal received at each antenna is multiplied by a weight
The energy of each CU received from
The energy calculated at each detector is combined using the EGC method, which is given as follows:
where
where
III. PROPOSED COOPERATIVE SPECTRUM SENSING BASED ON HAUSDORFF DISTANCE AND D-S THEORY OF COMBINATION
In this section, we provide a detailed description of the proposed method for the detection of an MU and the mitigation of its adverse effects. First, we measure all the users’ evidence by using the basic probability assignment (BPA) method. Then, we calculate the differences among the sets of evidence by using the Hausdorff distance and formulate the similarity measure matrix. After forming the similarity measure matrix, we calculate the credibility of the sets of evidence and compare it with a fixed threshold value. If the credibility value is greater than the threshold value, the user is considered a normal user, and if it is less than the threshold value, the user is considered to be an MU. Finally, we combine the evidence of the normal users at the fusion center. The overall flow chart of the proposed system is shown in Fig. 3.
>
A. Basic Probability Assignment
The D-S evidence theory is one of the candidates for the decision-making to combine users’ evidence, where the system faces an uncertainty problem. In the D-S evidence theory, the frame of discernment
where mi (
>
B. Detection of Malicious User and Mitigation of Its Adverse Effects Using Hausdorff Distance
An MU falsifies the local detection results, and thus, its evidence is different from that of a normal user to some extent. Several alternatives for quantifying a similarity between focal elements have been proposed [19]. In this paper, we propose a method using the Hausdorff distance to measure the difference between the evidence of two different sources, because the Hausdorff distance measures the degree of mismatch between two sets; we then form a similarity matrix to find the similarity between the sets of evidence. After the similarity matrix formation, malicious users and normal users are separated on the basis of their credibility values.
The Hausdorff distance provides a simple method for quantifying the distance between two sets of evidence
where h(m
The similarity measure Sim(m
Suppose that we have n sets of evidence; after obtaining the degree of similarity between the sets of evidence, we can construct the similarity measure matrix (SMM), which expresses the agreement between the sets of evidence as follows:
The degree of support of the evidence of a CU with respect to the evidence of other CUs is given as follows:
The credibility degree of evidence is given as follows:
After calculating the credibility of the evidence, we compare it with a fixed threshold value. If the credibility is greater than the threshold value, the user is authenticated as a normal user, and if the credibility is less than the threshold value, the user is considered to be an MU and is prevented from sending its evidence to the fusion center for the final decision.
>
C. Final Decision at Fusion Center
Once MUs are removed by using the proposed method using the Hausdorff distance, the sets of evidence of the normal users are sent to the fusion center. The fusion center combines these sets of evidence by using the D-S evidence theory. At the fusion center, BPAs are sequentially combined in the order of the arrival of normal evidence as follows:
where
where
The final decision
where
IV. SIMULATION RESULTS AND ANALYSIS
This section presents the results of MATLAB simulations of the proposed method and compares the performance of the proposed method with that of the k-means and Jaccard distance methods. Simulations consider scenarios with and without MUs. According to the CR system, every CU should vacate the channel if an LU signal is detected. Thus, the existence of an MU will degrade the performance of cooperative spectrum sensing.
In scenarios with MUs, five CUs are randomly placed, among which one is an MU. The energy of each CU is measured using MED, and the information from MED is combined at each CU by using the EGC method; the number of MEDs = 2. The probability of the presence of an LU is set to 0.5, the bandwidth is set to 6 MHz, and the sensing time is set to 50 μs. The fusion center combines the sets of evidence of the normal users sequentially and forms a global decision.
We consider three types of SSDF attacks: always busy (AB), always free (AF), and random attack in the network. In an AB attack, the MU changes the evidence of mi (
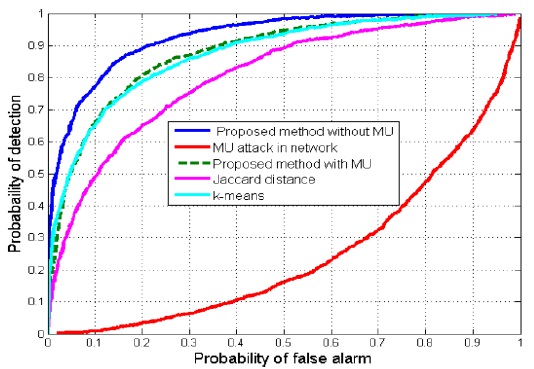
In Fig. 4, we have drawn the receiver operating characteristic (ROC) curve of the proposed method for an AB attack and compared its performance with the performance of the k-means and Jaccard distance methods. We have shown the performance of the proposed method with and without an MU attack in the network. It can be observed that when an AB attack occurs in the network, the probability of a false alarm increases and the probability of detection decreases; for example, when the probability of a false alarm equals 0.2, the probability of detection decreases from 0.9 to 0.1. The proposed method is able to detect and remove an MU from the network, resulting in better performance than the Jaccard distance and k-means methods.
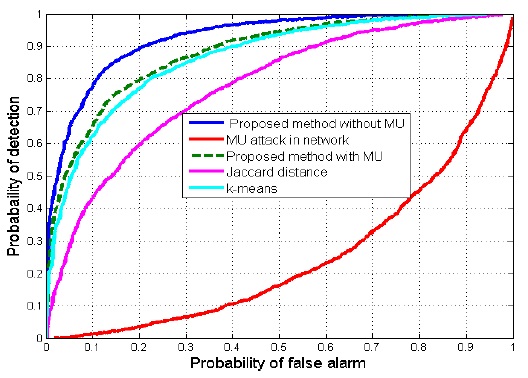
In an AF attack, the probability of a false alarm decreases, while the probability of misdetection increases, which increases the interference in the network. In Fig. 5, we have plotted the ROC curve with and without an MU in the network. It can be observed that the proposed method detects an MU and mitigates its adverse effects more effectively than the Jaccard distance method. The k-means method matches the performance of the proposed method at some points because it randomly selects the starting point for differentiating between the MU evidence and the normal user evidence.
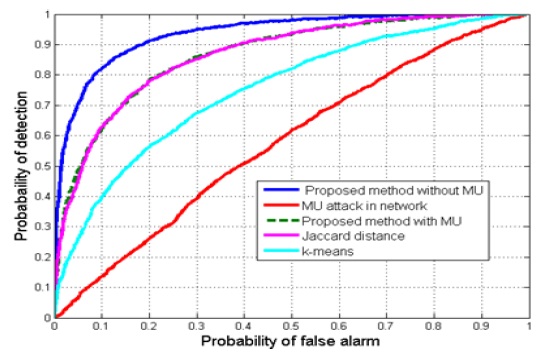
The simulation results of a random attack by an MU are shown in Fig. 6. The performance of the proposed method is better than that of the k-means and Jaccard distance approaches. From the simulation results, we can conclude that in all cases, i.e., AB, AF, and random attacks, the proposed method is better than the Jaccard distance and k-means methods in detecting an MU and mitigating its adverse effects on cooperative spectrum sensing.
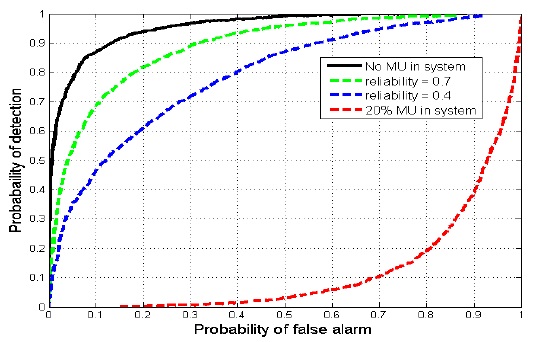
In Fig. 7, we have shown the ROC curve for scenarios with and without an MU and different values of reliability. As the reliability of the CU increases, it allows more sets of evidence to be sent to the FC and yields better results, which can be observed in Fig. 7, when the reliability increases from 0.4 to 0.7, because more sets of evidence reach the FC to help formulate a better decision.
In this paper, we proposed a method using the Hausdorff distance and a similarity measure matrix with the D-S evidence theory to detect an MU in a network and mitigate its adverse effects. The D-S evidence theory is one of the candidates to deal with the uncertainty of the evidence and improve the spectrum sensing performance. In this work, we considered three types of SSDF attacks, i.e., AB, AF, and random attacks. In our simulation, we compared the proposed method with the Jaccard distance method, which is also based on similarity, and with the k-means method. On the basis of the simulation results, we have shown that the proposed method is more effective than the other methods with respect to SSDF attacks.