Companies have been rushing to introduce supply chain management (SCM) systems for effective SCM and other benefits. However, there are a number of cyber threats in SCM systems. The main purpose of this study is to define the concept of cyber threat, examine general types of cyber threats, identify possible cyber threats to the supply chain, and suggest practical solutions. All procedures are based on a review of the available literature. The most common cyber threats to SCM systems are explored in this study: inference attacks, password sniffing/cracking software, spoofing attacks, denial of service attacks (DoS), and direct attacks. Until now, many enterprises have typically placed more emphasis on aspects of different technologies. Companies should concentrate on the development of innovative security technologies and investment in human resources such as standardized screening/employment processes, continuous education systems, efficient reward systems, and autonomous communication channels about security issues. In order to deal effectively with these procedures for improving organization security, the role of senior management in both the organization and government agencies is essential.
During the 1990s, a variety of changes in our market circumstances occurred, including globalization, a power shift from a seller’s market to a buyer’s market, deregulation in various industries, and new technology (Coyle
It is essential for efficient SCM to use information technology (IT) solutions via the Internet or intranet. The systems in SCM facilitate collaboration among supply chain partners and change the relationship-oriented pathways between suppliers and customers. The Internet-based supply chain is a very important business solution in respect to operations and strategy when firms do business with their partners (Zhang & Li, 2006). A well organized and integrated supply chain is one of the key factors for a successful business (Lee
A company is able to share various data, from useless to useful information, with its business partners through SCM systems (Moberg
Although effective information sharing in SCM is very important, the benefits of information sharing are not obtained without risks: correctness of information, disclosure of confidential information, timeliness issues, rights to the information, and continuous upgrading are all issues that must be considered (Lee & Whang, 1998). Cyber threat in SCM causes the loss of productivity and revenues (Anderson & Schwager, 2002), reduced competitiveness, and the loss of trust by supply chain partners (Kros
Up until now, little research has been conducted about cyber threat in SCM. To fill this gap, general cyber threats are addressed in this study, and some possible types of cyber threat in SCM are examined. Finally, this study explores the current possible solutions to protect against these investigated cyber threats in SCM.
This study is structured such that the next section on the concept of general cyber threat is followed by a section discussing the classification of cyber threat based on the literature review. The final section of the main part attempts to characterize threats in SCM and suggest appropriate solutions. The concluding section considers effective responses in the context of SCM.
Ⅱ. Definition and Types of Cyber Threat
The appearance of digital technologies has changed our living patterns, further accelerating changes due to information technology (IT). The word “digital” is being used naturally in our daily lives. Industrial, economic, and social systems are increasingly relying on IT infrastructure. This means that the major infrastructures of nations are faced with cyber threat as well as physical threat.
To define cyber threat exactly, several concepts related to cyber threat, cyber-terrorism, cyber-warfare and information warfare will first be examined. Cyber-terrorism and cyber-attack are regarded as a set of issues.
The compound word “cyber-terrorism” was coined in 1996 and has extensively spread after being adopted by the United States Armed Forces.
Based on several previous studies, cyber-terrorism can be defined as when cyber attackers, such as hackers, terrorists, international spies, and gang members, try to break into important national infrastructures, such as transportation, electric power, and communication, by using computer networking tools or to compel or threaten a government or civilian population or companies (Lewis, 2002). Janezewski and Colarik defined cyber-terrorism as attacks that are meticulously planned beforehand and aimed at a political purpose by targeting government institutions or secret societies, or individuals targeting critical information, servers, personal computer systems, or organized data that lead to serious consequences.
Janezewski and Colarik described information warfare as lying on a parallel line with cyber-terrorism. Information warfare is defined as a premeditated attack by countries or their lower organizations aimed at critical information, servers, personal computer systems, and organized data that results in significant damages to the counter party. The actual difference between cyber-terrorism and information warfare is that the former may bring about serious problems to someone such as injury, damage, anguish, or fear. Information warfare, however, has a designated mark in a war. We must try to distinguish between the concept of cyber-terrorism, information warfare and cyber crime, though it is difficult.
Cyber-warfare is parallel to information warfare and has been defined by SearchSecurity.com as a clash in cyberspace made with special purpose against computer systems or data. Cyber-warfare attacks can cause severe damage to authorized cyber homepages and system networks, disturb and deactivate vital services, steal or modify important data, and even destroy financial systems.
Cyber threat thus denotes a variety of risks in cyberspace posed by cyber-terrorism or cyber attack.
The vast network of the Internet has generated unimaginable threats in cyberspace. A gradual expansion of the scope of cyber threat leads to intellectual attack, which is easy because of various tools, difficulty of tracking, acceleration of networks, and use of infrastructures.
With the advancements in methods of cyber attack, almost everyone can attempt cyber threats against almost everyone else. Furthermore, they can easily acquire the tools or documents through the Internet that threaten the security of third parties. In the near future, the level of threat will increase dramatically, and tools for attacking will be developed at the same time.
1) Errors and omissions
Vulnerabilities to cyber threat can be created by errors and omissions. These threats often occur because of mistakes by system designers, programmers, system managers, maintainers, and users. For instance, they may make mistakes such as forgetting to create new administration accounts or to delete previous passwords when new systems or programs are installed (Cohen, 1997).
A considerable amount of software does not include a function for identifying various types of errors or omissions. Many users do not seriously consider “bugs,” or programming errors. However, these can frequently lead to disaster. In particular, if bugs in security programs for online banking, online payment, and websites relying on intellectual property are not dealt with, they can cause serious financial turmoil (NIST, 1997).
Malicious code is a sort of program code developed with ill intention. Malicious code, especially that existing in a state of independent software instead of being parasitic, is malicious software or malware. Typical forms of malicious code are viruses, Trojan horses, worms, and other harmful software. The aims of this software are diverse and range from stealing personal information and data to spreading information to unspecified individuals. In order to achieve these purposes, they sometimes delete specific files, format hard disk drives automatically, or transform original information or data (NSW Guideline, 2003).
3) Malicious intrusion attempts
Many types of malicious intrusion attempts have been reported, and various methods and programs are being developed to combat them. Four concepts will be dealt with: hacking, denial of service attacks, password sniffing, and eavesdropping.
Hacking is behavior that finds security vulnerabilities in networks, exploits these problems, and protects malicious use. A hacker is a person who undertakes these tasks. However, the meaning has degenerated into an unsound definition due to the wide dissemination of personal computers. For example, a cracker, as distinguished from a hacker, breaks into other users’ computers, steals information, makes unfair profit, gets rid of files, and sometimes paralyzes whole networks.
The warning “Denial of Service” (DoS) appeared often on our computer screen in the 1990s when we accessed websites. The server had pool processing capacity, and if many users tried to contact a server at the same time, the server went down, and then users would see this famous phrase. In the late 1990s, the DoS attack was invented from understanding this weakness. It is now impossible to crash a system via a DoS attack because of the development of networks in the 2000s. A new type of DoS thus developed, distributed denial of service (DDoS), was then developed. Unlike a DoS attack, this method does not need to get at users for the attack and just distributes malicious code with specific instructions among unspecified personal computers.
Sniffing or eavesdropping is one of the methods of hacking. It means that an attacker uses a tool (sniffer) or program to overhear packet switching in a the network. The program has storage, sorting, and analysis functions to change data packets into meaningful information, such as passwords, personal information, critical documents, and confidential reports. A sniffing attack is extremely threatening to web hosting and Internet data center (IDC) companies that share networks (NSW Guideline, 2003).
4) Fraud and deception
Spoofing is a technique used to attack a system in a way that hides its own network information, such as its IP address, DNS name, or Mac address. An attacker in a network tries to dissimulate his/her own network information in order to prevent reverse tracing by using the security vulnerability of the TCP/IP protocol. There are four kinds of spoofing attacks: IP spoofing, APR spoofing, email spoofing, and DNS spoofing. The simplest way is email spoofing, which gives a false address to receivers or uses an alias in the “from” field. The masquerade is a very similar technique to spoofing. Many specialists use spoofing mixed with masquerade.
The salami attack is used in computer fraud. The technique is to gather a small amount of information from many users. An example from Germany occurred when a teller in a financial company took round-off error amounts from customers’ accounts and moved them into his own account. Another example occurred when a fraudster opened a fictitious online shopping mall, gathered mass information on private credit cards, and asked people to pay a small sum of money. Most victims did not recognize that their own credit card was being used in an illegal way due to the small amounts involved.
5) Physical and environmental risks
Cyber threat may be caused by natural disasters, such as fire, flood, volcano, earth movement, solar flares, and severe weather. Environmental control failures can cause unauthorized access, physical damage, and service interruption. There are diverse causes around us, such as air conditioning breakdowns, heating failures, dust, toxic gases, power failures, and various chemicals.
Dumpster diving is behavior where attackers search through waste products to find necessary information. The attacker sometimes finds very useful information (Cohen, 1997).
Ⅲ. Cyber Threat in Supply Chain Management
SCM systems can be exposed to miscellaneous cyber attacks. For instance, a competitor, who could use it for a future strategy or promotion or sell the information to another company or individual, might steal confidential corporate information integrated by the SCM system. Moreover, certain malicious attackers might collect vast amounts of customers’ personal information and disseminate it via the Internet. Financial transactions are shut down due to malicious intrusion and attacks, and company funds are embezzled by malicious hackers. Furthermore, the SCM system may be attacked during failures or when it is under repair. A more complicated SCM system might facemuch higher risk because the system connects with the systems of business partners, trades much more information than a simple system, and has a great deal of information and data (Kros
In the following paragraphs, the most common cyber threats to SCM systems are explored based on various key pieces of literature.
1. The general cyber threat of supply chain management systems
1) Inference attacks
Inference problems are deeply associated with data mining. Data mining is a very useful method when researchers want to discover meaningful information from a huge data warehouse. However, this technique can lead to security threats, as when hackers use a data mining technique in order to find confidential information.
An inference attack is a cyber threat in an SCM system that happens when attackers infer critical information from minor information. It sometimes occurs in a multilevel secure database located in the company when a low-level administrator is able to deduce very important information through common information and authorized information acquired from other people or routes. Inference problems need not occur in direct relation to illegal intrusion or information leaks, so risks and problems become more serious if attackers then infer new information by using authorized data access (Raman, 2001).
Many companies are currently trying to establish integrated enterprise systems for effective supply chain operation and information sharing with all business partners. An SCM system can be faced with unexpected difficulties by an inference attack. For instance, such large retailers as Tesco, ASDA, and Sainsbury’s have their own SCM systems and share information with their suppliers under certain conditions. The companies strategically collaborate with various suppliers. Both parties are unwilling to share information for strategic operations regarding inventory level, logistics, customer demand, and related critical data. Price data is no exception. Suppliers have a decided tendency not to open up all information involving price despite demands from retailers. If suppliers could gain prices from retailers via SCM systems, suppliers could compare their prices with other suppliers. The leakage of information caused by careless suppliers could then be stolen or inferred by competitors (Zhang & Li, 2006).
2) Password sniffing/cracking software
Many different techniques are used in malicious hacking and intrusion attempts. Password cracking using software is one of the easiest ways for users to recover a forgotten password or for attackers to get a password for unauthorized access to a system (Warren & Hutchinson, 2000). The most popular software packages for password cracking are Cain and Abel (only for Microsoft Windows), John and Ripper, and THC Hydra. Some typical software for password sniffing are Wireshark, Kismet, and Tcpdump. Most of these software packages include a combination of principal password cracking methods, such as dictionary attacks and brute force attack (Insecure.Org, 2006).
These types of threats can result in severe damage to an SCM system in a variety of ways. A hacker can access an SCM system by using gained passwords via software packages or commercial services and then steal, delete, or change data related to customer information, supplier data, price lists, and product specification and information. Stolen information is often used to make a deal with a competitor or for fraud purposes. The most serious problem with attacks occur when attackers access the system repeatedly using a number of software packages.
3) Spoofing attacks
We often watch scenes in movies where a spy uses others’ identification so as not to disclose his/her identity. In this case, the spy usually employs a false identity, such as a driver’s license or passport, and physical transformation, such as plastic surgery, changing fingerprints, or voice alteration.
People who want to carry out malicious or clandestine activities also try to conceal their identity within networks. Distinguishable information in the networks includes IP (Internet protocol) addresses, DNS names (domain name system), MAC addresses, and email addresses.
The spoofing attack is a cyber-attack technique where the attackers lie about their true identity in cyberspace and indiscriminately deliver an attack against users or systems. An anonymous attacker in a network tries to hack based on very vulnerable TCP/IP protocols, and if the attacker hides his/her own system information (IP address, DNS name, Mac address and so on), it is very difficult to trace their origins. These attacks can support a number of related cyber attack activities, such as packet sniffing, DDoS (Distributed Denial of Service), and session hijacking.
SCM systems may be exposed to these cyber attacks. Attackers can use an SCM system for spreading spam emails for advertisement. Hackers who have made money from junk emails used to exploit mobile phones, but mobile phone services set a limit on the number of text messages per day, and the hackers had to pay per text and additional communication costs. Today, they often exploit large servers in companies via illegal cyber attacks. These servers, or zombie computers, send out over 40% of the world’s spam. IP spoofing is a highly alarming attack in the case of SCM systems as well. In the high-tech industries, such as aerospace (e.g., Boeing, Airbus, Rolls-Royce), shipping (Hyundai Heavy Industry, Samsung Heavy Industry, Maersk Sealand), heavy equipment (Caterpillar, Linde, Kalmar), and automobiles (Mercedes-Benz, Ford, BMW, Volkswagen), technical information and knowhow are very important, and these data are stored in SCM systems for the purpose of efficient information sharing with suppliers. If a hacker attacks by way of IP spoofing, this malicious behavior may be a deathblow. The hacker can be given money for technology information transfer to other countries or firms and rid themselves of the stolen products using logistics information.
4) Denial of service attacks (DoS)
A denial of service (DoS) attack is another hacking method. It works when one or more malicious users occupy or crash a computer or network resource. This is similar to when a phone number receives too many calls and is inoperative for a time. That is, the attack crashes the target computer or network by way of massive simultaneous access. The purpose of this attack is not to steal information or delete data, but to interrupt the availability of the resources (Howard, 1997).
The general procedure of DoS attacks is that a hacker first searches hosts or networks for weak points of security by exploiting freeware. The hacker then sets up attacking software (e.g., Trinoo, Stacheldraht, Tribal Flood Network) on a zombie computer or network. The compromised system can be fully controlled according to the hacker’s commands. This zombie computer sends illegal packet messengers, such as “packets with incorrect checksums, incorrect header field values, or an invalid combination of flags” (Hussain
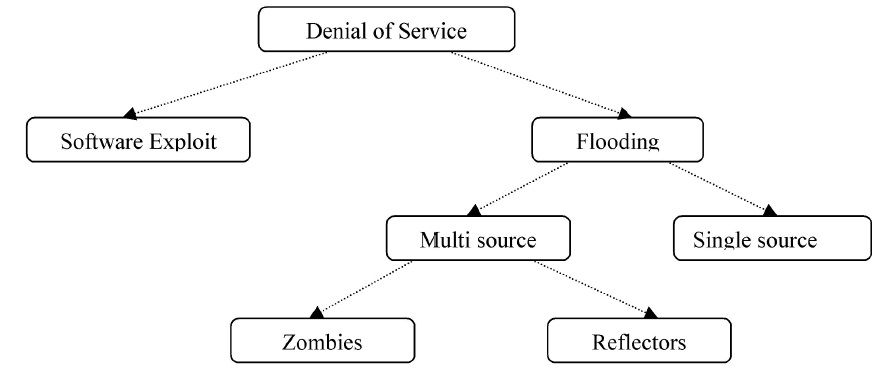
DoS can be classified based on the volume of packets and number of attackers, as in Figure 1.
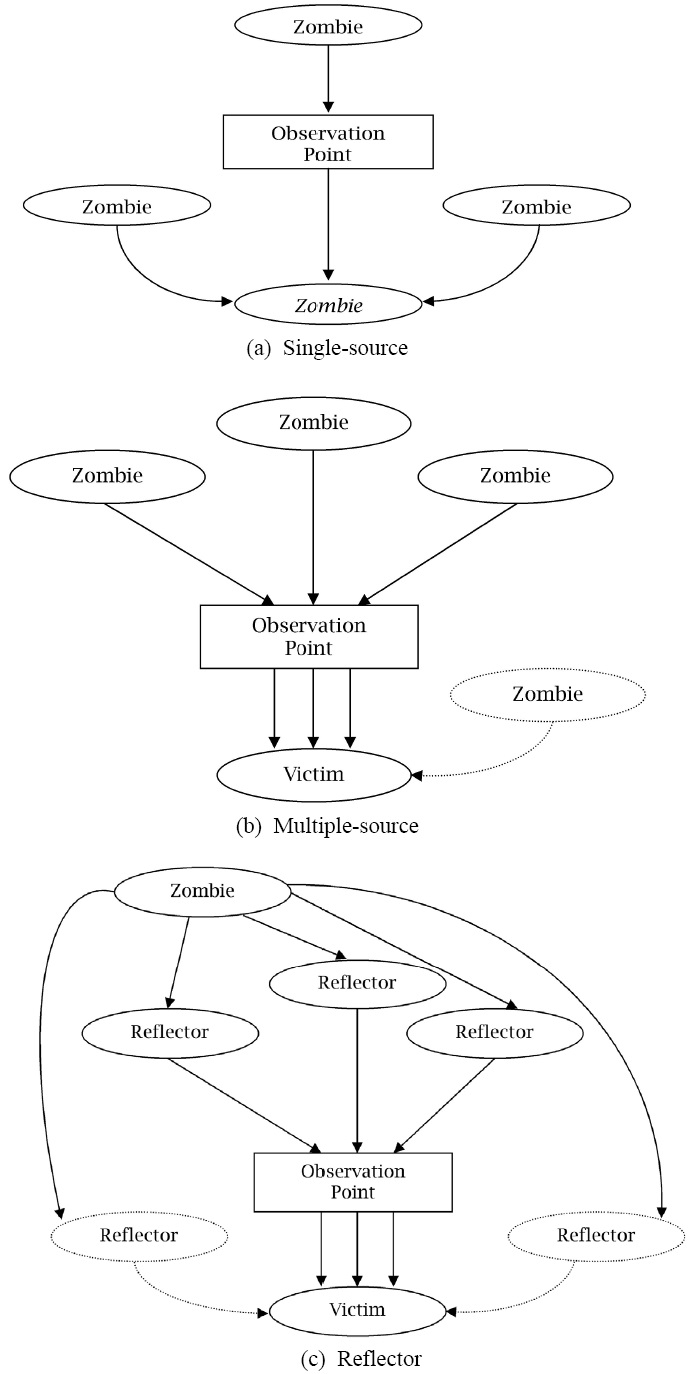
DoS attacks can be widely classified into software exploitation and flooding attacks. An attack with software exploitation uses fatal defects in the software of the targeted computer or network. A common instance is the “Ping o’ Death.” The “ping” command is used to check whether another system on a network is active. This attack results in a system crash by transmitting a single large ping packet (65-536 bytes) of more than the default size of 64 bytes (Warren & Hutchinson, 2000). Flooding attacks cause a persistent packet stream, whose purpose is to flood link bandwidth or computer resources using a zombie computer or network. DoS flooding attacks can be single-source attacks or multi-source attacks. The former is an attack from only one host (see Figure 2(a)), and the latter attacks a system with a bombardment of packets in order to cripple a computer or network via coordinated multiple hosts. This is called a DDoS (Distributed Denial of Service) attack (see Figure 2(b)).
Finally, Figure 2(c) shows the reflector attack. These attacks can be used when a hacker does not want to reveal his/her identity or would like to intensify an attack.
These attacks have a very serious impact on companies that value real-time information sharing. Let us imagine that the SCM system at Tesco, a leading UK retail group, is attacked by multiple zombie hosts. A number of business partners cannot access the integrated SCM system and get into uncontrollable confusion because Tesco has a very complex supply chain network on a global scale. These problems have a decisively negative effect on inventory management, customer satisfaction, the company’s income, and corporate image. These types of cyber attacks have become more complex, and a number of new tools and software have been developed by malicious users and firms.
2. Case studies on cyber threat to global supply chain management systems
Founded in 1981, Giordano has a leading position among clothing retailers in the Asia-Pacific region. It runs more than 1,900 stores in 31 countries and has more than 8,000 employees. The company highly regards the management and the operation of its IT environment as important because more than 80 percent of all employees utilize personal computers. IT management had become more complex according to increasing stores and offices in dozens of territories. One of the serious problems was that Giordano had a mix of operating systems in its shops and offices, so it had become difficult and costly to manage the company's PC environment. Whenever the firm would like to change network policies or systems, the global supply chain management systems were frequently exposed to various cyber attacks and IT staffs had suffered from time-consuming tests. For instance, employees often downloaded their own software into company computers, which increased the risk of exposure to malicious software. To effectively manage its information security, Giordano decided to upgrade and optimize their desktop and portable PC environment. Giordano needed to standardize its PC environment across its stores and offices in order to lower IT costs and simplify IT management. They wanted to control the entire IT and SCM systems centrally from the company's IT headquarters in Guangzhou, China.
First of all, Giordano evaluated the initial version of the Windows 7 and they installed the Window 7 Enterprise Edition into 25 computers in the IT department in 2009. The company set up the Microsoft System Center Configuration Manager to access the compatibility of the company's hardware and application suite with Windows 7 and confirmed that the new adopted system would help to enhance information security, IT management, user-interface environment, and productivity through a pilot test. In November 2009, the firm began launching Windows 7 Enterprise on 682 computers in retail shops throughout China and then in February 2010, they began deploying Windows 7 Enterprise Edition on more than 1,500 computers in stores in several other countries. Simultaneously, Giordano introduced Microsoft Application Virtualization (App-V) and Microsoft Advanced Group Policy Management which are components of the Microsoft Desktop optimization Pack for Software Assurance in order to boost centralization of IT management.
Giordano improved its control over the firm's PC environment and tightened up security by adopting Windows 7 Enterprise and the Microsoft Desktop Optimization Pack. To increase control over its computers and the application, the corporation exploited App-V and Advanced Group Policy Management. By using App-V, mobile employees could work in different places - even with different computers - and still access the applications they need. With more control over its PC environment, Giordano helped to strengthen security on its computers and reduce the risk of failure over large areas of its business. The IT team at Giordano used Advanced Group Policy Management to perform automated tests when it changed network systems, which resulted in reduced mistakes, significant savings, and increased flexibility.
2) Tesco
One of the most dominant grocery retailers in the world, Tesco, has now expanded from Eastern Europe to Asia. SCM systems at Tesco are crucial elements for successful on-line and off-line businesses. Tesco stores tend to keep better inventory than their competitors, while continuing to keep their costs down. A number of companies in the grocery industry are implementing warehouse management systems (WMS) that help to manage various warehouse operations. These systems consist of RF communication devices, hardware, computers for operation, automatic identification equipments, and application software. They are being used in order to minimize the costs that are associated or connected to space, equipment, and labor, together with real-time performance that directs and manages their tasks. Besides, they can also assist to maximize the utilization of different equipment as well as track, control and manage inventory. Tesco relies heavily on information technology, namely supply chain management systems to ensure the success of its global business strategy. However, some branches and stores had used the Windows XP operating system for nearly a decade. Therefore, executives concluded that it was the right time to move forward with a companywide upgrade in 2009. Along with the upcoming expiration of Windows XP, the firm was motivated by an opportunity to acquire new tools for tightening network security, accelerating PC performance, and improving employee productivity. In particular, the company regarded the protection against malicious software at the operating system level and in the browser as important.
To overcome these criteria, Tesco decided to deploy the Windows 7 Enterprise operating system, along with the Windows Internet Explorer 8 Internet browser. The IT department spent six months before the deployment performing readiness testing on more than 3,800 applications. It considered virtualization solutions that could deliver applications on a virtual PC running Windows XP. The IT team, however, chose instead to take advantage of the extensive guidance provided through the Microsoft Application Compatibility Toolkit, which is a lifecycle management tool that assists in identifying and managing application portfolios. Moreover, the Tesco IT team used AppTitude from App-DNA to manage testing and remediation for a subset of its applications. Tesco began an initial, limited deployment of the 64-bit version of Windows 7 Enterprise Edition to about 1,000 users after identifying 1,800 applications as fully ready for migration in May 2010. The company is on schedule to achieve full deployment to all its 187,000 PCs by the end of 2012 and it plans to use the operating system deployment features of Microsoft System Center Configuration Manager 2007 to automate image creation and network configuration tasks.
In the first several months after deploying Windows 7 Enterprise, Tesco has realized several benefits in accordance with its decision. The company plans to capitalize on the enhanced security model of Windows 7, including built-in support for a greater variety of smart card usage scenarios. The new employed system provides a greater level of protection against malicious software and other threats. Windows 7 Enterprise is a critical component in rigorously safeguarding its IT assets. By deploying the 64-bit version of Windows 7 Enterprise, Tesco has already benefitted from faster performance on a substantial number of its PCs and anticipates continued gains in worker productivity, along with improvements in user interface design.
Ⅳ. Methods of Security for Supply Chain Management Systems
The resource-based view (RBV) of a firm is a useful framework that provides easily understood results and measures when we decide to invest in security matters. The RBV focuses on the strong points and competitiveness that come from differences between departments within the company rather than on industrial attributes (Penrose, 1959). The concept of the RBV is adoptable to the supply chain context, and resources for supply chain security can be used to reduce losses, rather than to increase profits.
The development of organizational security capabilities can be applied from the perspective of supply chain security management. The development of such capabilities seem to considerably correlate with a firm’s dynamic capability. Eisenhardt and Martin (2000) defined dynamic capabilities as the unique abilities of a firm to reconstitute resource stocks. These organizational capabilities do not directly result in a substantial improvement in productivity, but are indirectly involved in business success through their influence upon regular operational capabilities (Helfat & Peteraf, 2003).
Autry and Sanders (2009) undertook a study on the possibility of applying dynamic capabilities to supply chain security management via preceding research by Eisenhardt and Martin (2000). They state that the dynamic capabilities method is suitable for the analysis of supply chain security management capabilities, which will now be discussed in more detail, based on the dynamic capabilities approach.
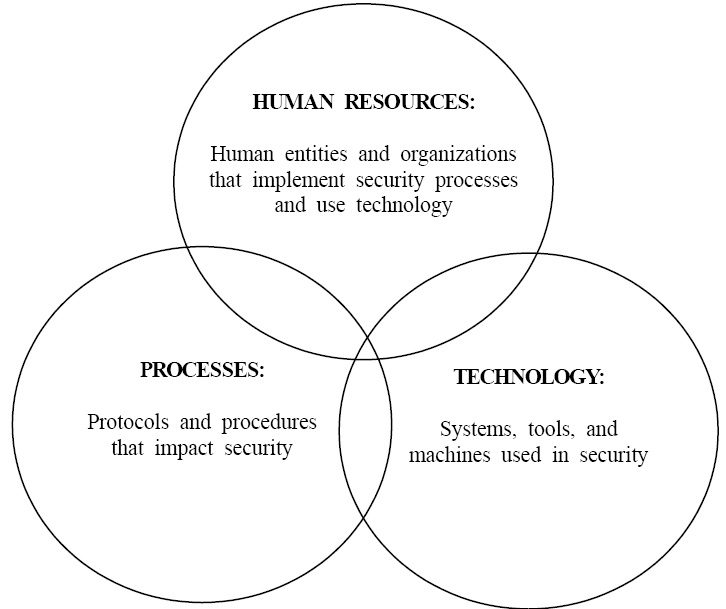
Continuity planning involves managing the activities of security fulfillment across the whole supply chain. It helps to relieve a variety of supply chain risks and ameliorate supply chain security. Dynamic security management capabilities are the foundation for accomplishing a firm’s goal of supply chain security. These capabilities can be divided into three major categories: processes, technology, and human resources (Autry & Sanders, 2009), as illustrated in Figure 4.
Processes are a series of procedures that include all activities, from raw material suppliers to end-users in the supply chain. They have their own regulations for effective management. Monitoring prevention and responsiveness are critical factors for building efficient processes. Technology is related to the use of systems, software, and tools for securing supply chain management systems. Another issue involves human resources, including all members of the organization, suppliers, and security-related firms. In particular, these capabilities have received wide attention because they are all controlled by human resources.
Processes, or protocols, are critical dynamic security management capabilities for building business continuity in SCM. In order to implement processes effectively, firms should manage all activities across the organization and supply chain. We can learn a good lesson from total quality management (TQM), which helps to build strategies for efficient systems throughout all processes (Lee & Wolfe, 2003). Before using TQM, most corporations used sampling or quality checks to inspect for product defects after production was completed. In the 1980s, several eminent scholars, such as W. Edwards Deming and Phil Crosby, showed that these measures can be costly to the firm. In an analogy to TQM, all processes should be ruminated.
Another lesson of TQM is that quality management should be carried out on each activity in the supply chain from raw material suppliers to end users. If a company applies this concept to supply chain security, they have to monitor every step for security, rather than checking certain points before delivery to the customers. Standardization is one of the keys to success for security in SCM. Security has to be considered in each process, which includes supply chain visibility, procurement, inventory management, process redesign, and demand forecasting procedures.
1) Supply chain visibility
One of the important factors for continuity from the perspective of supply chain security is to secure supply chain visibility (SCV). SCV, which is essential for global business systems, helps to synchronize supply chain processes, such as procurement, production, inventory management, logistics, and sales, as well as customer service and customer satisfaction. When problems occur in the supply chain network, the enterprise can detect the problems promptly and respond to them effectively.
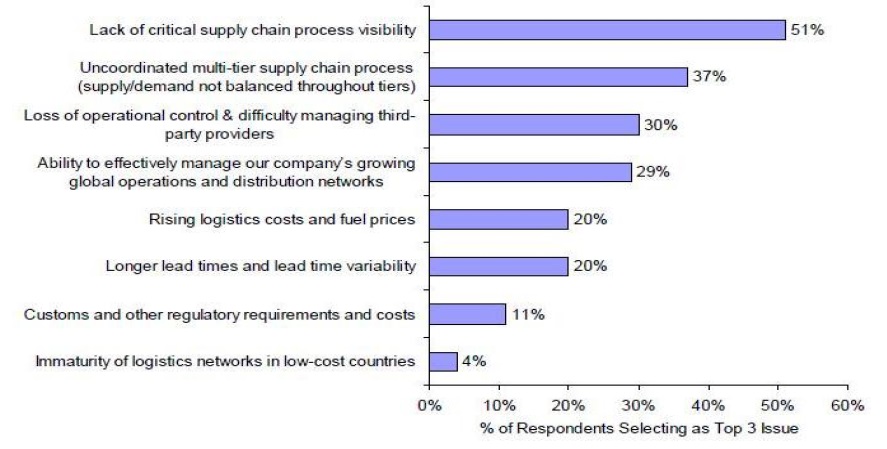
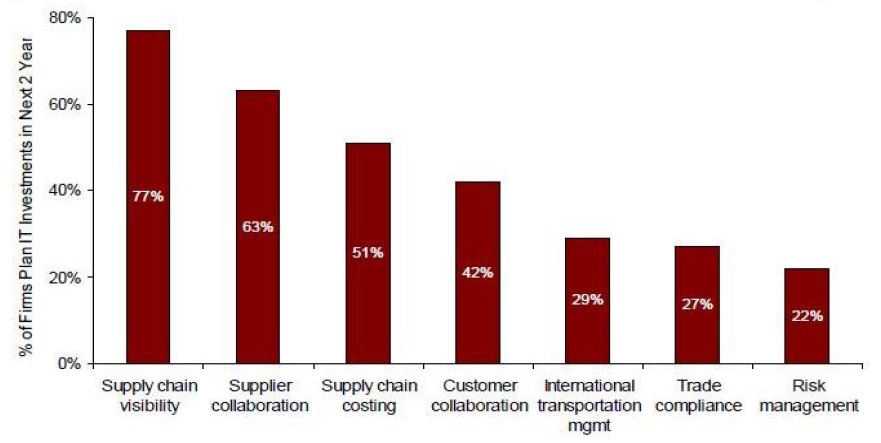
According to the Aberdeen Group’s research in 2006, visibility of the supply chain network, which helps to improve the speed and visibility of global business activity, is the area of most concern. It and the other top areas of concern are depicted in Figure 5. Furthermore, visibility in the supply chain network was selected as the main concern by 79% of large corporations.
The most important system of the supply chain network over the next two years was the supply chain visibility system. Figure 6 shows the research results.
Many multinational companies have realized that effective visibility is one of core competencies in doing good business with their business partners for global management. Effective visibility can be further promoted via a supporting system. System-based visibility is realized by real-time databases that include data such as inventory levels, sales, logistics, and demand.
2) Sourcing strategy
The method of just-in-time (JIT) has been used and spread in the field of manufacturing since the 1980s. A single sourcing strategy has been regarded as a good technique to support lean manufacturing. A number of companies believed that the best strategy was to reinforce cooperative relationships with their business partners, improving quality, and having a good relationship for a long period. However, these beliefs did not last long due to unexpected supply problems (Sheffi, 2005).
Since then, various sourcing strategies have been attempted by firms aiming to ease supply chain risks and improve supply chain security. One of the strategies is to manage costs effectively and increase flexibility. In order to achieve this, firms are exploring ways to diversify supply channels. For instance, Hewlett-Packard contracted with a supplier who provides fixed quantities of product, guaranteed by HP, for cost efficiency. HP then made a flexible contract with another supplier who provides flexible quantities with upper and lower volume limits. If provided products are less than the needed quantity, HP can trade through the stock market to mitigate the difference (Feitzinger & Lee, 1997).
A second sourcing strategy is to use local suppliers. Many companies currently procure sources from global suppliers for reasons such as cost, flexibility, and operational strategy. However, many companies in America realized, after the malicious attacks on 9/11, that dual sourcing efficiently reduces risk. Though sourcing from local suppliers can be more expensive than global supply, it provides advantages such as flexible responses to quick market changes and regional economy activation.
A final sourcing strategy is to establish business relationships with suppliers who have manufacturing bases in more than one place, thus diversifying to mitigate risks.
3) Inventory management
Strategic inventory management is regarded as one of the main processes for providing resiliency and building continuity (Lee, 2002). As mentioned earlier, supply chain visibility is a core matter in supply chain security. To manage this effectively, visibility is also important in inventory management. Inventory management visibility includes the locations of warehouses for raw materials, work-in-process inventory, and distribution centers.
Just-in-time (JIT) inventory management has played a key role in maintaining rational inventory levels and the elimination of waste. However, this lean management sometimes causes unexpected shortages. Therefore, a new JIT method has been assumed by leading companies. They use an integrated inventory system in order to calculate the amount of safety stock. Uncertain delivery times, the cost between stock-out and hold, and unstable supply and demand fluctuations should all be taken into consideration when companies decide the amount of safety stock using this system (Martha & Subbakrishna, 2002).
4) Product and process design
The management of product and process design, while still a fledgling phenomenon, has found a niche. The concept of product design is to plan products by taking into account common points of parts. This strategy can have a wider variety of selections from suppliers and helps companies more easily manage their inventory levels.
The second strategy is to standardize the manufacturing process among manufacturing locations. Companies can more easily move from one factory to another when a factory has a sudden problem. Intel Corporation applied this strategy for protecting against a security breach. They adopted a strategy of “Copy Exactly,” which is to overcome problems by using the exact same process elsewhere when one process is faced with a security breach or disruption (Sheffi, 2005).
Another strategy of postponement, or last stage manufacturing, has gained increased attention as it has much more flexibility. Postponement (flexible fulfillment) is a sort of manufacturing method that “attempts to delay the final definition of a product to the last possible stage in the supply chain, hence the popular description of postponement” (Michaelides, 2010). This strategy has some advantages, such as the reduction of production times, cost savings, and flexibility in terms of security issues. Postponement strategy has been mainly applied to the high-tech industry, such as digital cameras, computers, mobile phones, and cars.
5) Forecasting
Demand-based management and forecasting are critical factors in supply chain security. The former means that a company offers the right products in the right quantity at the right place to the customers with some flexibility. The strategy of Dell Computer Corporation is a good example. Dell adopted a direct sales channel rather than sales through retailers. Dell receives an order from a customer, and then they gives an order to their suppliers as a safety stock. This allows them to respond quickly to market changes and sudden catastrophes (Sanders, 2006).
The latter, forecasting, is very important, but a challenging task for many companies. There are two kinds of forecasting: statistical and managerial. Statistical forecasting involves predicting future figures by using historical data. This technique is slightly inaccurate due to such causes as inaccurate and missing data, various forecasting models and variables, and rapidly changing international circumstances. To compensate for these defects, many companies combine managerial forecasting with statistical forecasts. Sometimes, knowhow based on past experiences is more accurate than statistical data.
Another way to alleviate inaccurate forecasting is to establish a range of possible figures. This is important in terms of flexibility. Firms can build a procurement strategy, respond quickly to demand fluctuations, and cope with security breaches based on high and low ranges of figures. Another good method to attain reasonable data via forecasting is to collaborate with supply chain partners through integrated systems. Collaborative planning forecasting and replenishment (CPFR) is a good example. CPFR means that business partners create guidelines for forecasting and replenishment through information sharing. They are able to get more accurate data and share risks with each other, improving their performance (Sanders, 2006).
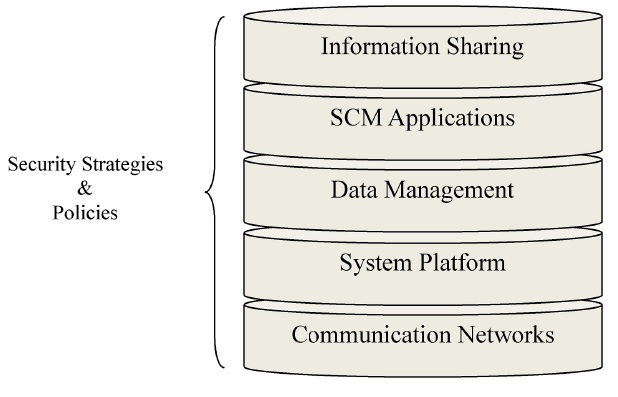
Prior to reviewing technologies for supply chain security, an understanding of the basic elements of the Internet-based SCM system is essential to identifying effective technologies against cyber attacks/threats in SCM. A reference model that includes all of the components is illustrated in Figure 7.
The reference model becomes the foundation for explaining cyber attacks/threats in SCM. To find efficient solutions, we have to explore each layer in the reference model.
Information sharing and SCM applications in this model are directly involved in business activities. The bottom three layers, data management, system platform, and communication networks, encourage smooth information sharing. These three layers are directly connected with security solutions in the SCM system. Effective security policies and strategies should be based on integrated technology solutions to assist staff understanding of the security rules and practices, mitigating potential cyber threats (Forcht & Ayers, 2001).
We will examine the key technologies for the bottom three layers and then explain three up-to-date technologies that help to promote cyber security in the SCM system: role based access control (RBAC) technology, the secure supply chain collaboration (SSCC) protocols suite, and radio frequency identification technology (RFID).
1) General technologies for securing communication networks in SCM systems
Secure sockets layer (SSL), multiple types of virtual private network (VPN), firewalls, vulnerability assessment tools, and intrusion detection systems (IDS) are the primary security technologies for securing communication networks. SSL and VPN have a security function based on the Internet protocol version 4 (IPv4). According to Zhang and Li, “Firewalls and vulnerability assessment tools are proactive tools for securing communication networks, while intrusion detection systems are reactive tools” (2006). These technologies will be reviewed based on a key text by Maiwald.
SSL is a global standard algorithm for the encryption of interaction data between a web server (website) and a user’s PC (web browser). In other words, this is a protocol for securing personal information when users trade data on the Web. SSL has become the most reliable cryptographic protocol for protecting personal and credit card information since it was developed by the IETF (Internet Engineering Task Force) in 1994. There are two major operation types: hardware-based SSL and software-based SSL.
VPN is a data network set up so that each enterprise uses tunneling protocols and security processes based on a public network. Firms can reduce operational costs through VPN because the connection is very simple between the private network and the Internet service provider, so additional hardware or software is not required. VPN encrypts data before transmitting to the public network and decrypts the encrypted data. Encryption includes the data and the transmitter’s network address for extra security. VPN can be adopted for all types of applications, but SSL can be applied only to web applications. Therefore, VPN is more useful for connecting different SCM systems.
The firewall is one of the effective security systems to block illegal access between external and internal networks. Many companies today use computer systems in order to manage all their information effectively. Therefore, if a number of malicious users try to steal useful information for a special purpose, the firewall works to prevent these disasters. The router and gateway are core technologies used to accomplish an efficient firewall, and all information exchange is made only through these technologies. The appearance of a firewall is closely related to the intranet, which has the role of catalyst. The three major types of firewalls are the packet filtering firewall, dual-homed gateway firewall, and screened host firewall. A firewall may be used to build a VPN tunnel for safe information sharing with business partners through SCM systems.
Vulnerability assessment tools, also called scanners, are designed to scan Web applications automatically and identify potential weaknesses in the network. This tool is a little different from other vulnerability assessment tools. Scanners do not investigate a wide range of hardware and software, but focus on checking for “potential field manipulation and cookie poisoning, which allows a more focused assessment of web applications by exposing vulnerabilities of which standard VA tools are unaware” (SAMATE).
An intrusion detection system is different from a simple security system that has a function for controlling access. The system performs real-time monitoring and detects intrusions by using a database of intrusion patterns (signature database) and an expert system. The advantage of an IDS is that it easily applies new technology, blocks internal attacks as well as external threats, blocks off access regardless of IP address, responds quickly to illegal intrusions, and traces intrusion routes. These systems can be classified into network intrusion detection systems (N-IDS) and host intrusion detection systems (H-IDS).
2) General technologies for securing system platforms in SCM systems
The operating systems and middleware, which carry out the role of assisting information sharing applications and databases, are contained in the system platform. The two major roles of the system platform in terms of security are to enforce security against potential threats and to act as a mediator between SCM applications and databases for secure communications.
System administration and maintenance are vital to keep the system platform in good condition. The system administrator should understand the current system configuration, install critical security patches, and regularly update them. Common object request broker architecture (COBRA) and distributed common object models (DCOM) are typical commercial operating systems and middleware systems for securing communication between SCM applications and databases.
COBRA is a standard platform for distributed object technology using object management architecture (OMA) suggested by the object management group (OMG). It provides solutions for integrating distributed object management with various applications. The existing distributed system needs to communicate with external security applications to secure the system because the system does not include internal security programs. However, the object security service provided by COBRA includes its own security applications from the object request broker (ORB). Therefore, we can expect to improve security performance because COBRA does not need to communicate with external security applications.
DCOM, developed by Microsoft, is a program interface that supports service requests from client program objects to server program objects in other computers. For example, a website may operate under unique scripts or programs. The website’s program accomplishes its processes using DCOM, and the results can be delivered by a remote procedure call (RPC) to a specific server object. Then DCOM passes the results on to website viewers. DCOM is used in large-scale networks and Internet-based networks. DCOM uses TCP/IP and HTTP, and DCOM is equal to COBRA because DCOM provides a variety of distributed services. It takes a Microsoft approach to program and data objects in the network itself, while COBRA is supported by OMG and other information and communication enterprises.
3) General technologies for securing data management in SCM systems
The systems managers or administrators of SCM systems have to keep an eye on inference attacks from hackers when they are trying to secure their data warehouse. Inference attacks sometimes occur in a company’s multilevel secure database when a low-level administrator is able to deduce important information through common and authorized information acquired from other people or routes. It is not easy to deal with the detection of such matters because innumerable problems can occur once a malicious user does this.
A method for detecting unauthorized inference was proposed by Clifton
The two current procedures will evidence a feasible technique to protect against inference attacks. Firstly, we should find the minimum protection requirements from the methodology suggested by Dawson et al. This strategy is important for drafting security policies. Secondly, we have to perform data mining and then build possible inference channels and associations based on the results. Then we can evaluate the security policy draft and propose more sophisticated alternatives.
4) Role Based Access Control (RBAC)
RBAC is one of the most common models for security administration and was proposed by Farraiolo and Kuhn in 1992. The RBAC model assigns access rights among multiple users based on the conceptual object of role. The model plays an important role in the three bottom layers of data management, system platforms, and communication networks in the reference model for an Internet-based SCM system. The simplest structured RBAC is modeled by a logical combination of three entities: users, roles, and privileges.
The RBAC model has been modified and extended in many different forms for effective general business operations as well as SCM systems. The administrative advantage of the model is compatible with “commercial database management systems (such as Informix, Sybase and Oracle), middleware standards, web-based applications and authorization servers” (Zhang & Li, 2006). To streamline access authorization procedures, a number of large companies have pursued the object of a centralized authentication server. In this case, the RBAC model is able to demonstrate significant performance by harmonizing the lightweight directory access protocol (LDAP), which is one of the authorization service standards on the HP Presidium Authorization Server (Chandramouli, 2000).
5) Secure Supply Chain Collaboration Protocols
Atallah
6) RFID for securing information sharing in SCM systems
RFID technology began when British forces developed “identification, friend or foe” (IFF), an automatic response machine, in 1939. This machine was used to distinguish between allies and enemies during WWII. In the 1980s, several industries, such as transport and defense, used RFID technology commercially.
RFID is an information sharing technology used over relatively long distances using radio signals. RFID needs tags and readers in order to exchange information, much like barcodes, except that barcode technology uses optical lights and cannot be used over long distances or past barriers. RFID technology, however, can do so because it reads information using radio signals. RFID technology is utilized in a variety of fields, such as recorders in sports, tracers on products or endangered species, identification or passports for obtaining individual information, and readers for items in containers. This technology can also be applied to the two top layers in the reference model for an Internet-based SCM system.
RFID can be classified into two types. Active RFID uses electric power from RFID tags when it receives and sends information, while passive RFID uses the electric power of the RFID reader. In the area of supply chain management, passive RFID may completely replace barcode technology in the near future because of its better speed, performance, and capability. If passive RFID technology is carefully set up in the SCM, firms are able to achieve higher visibility. These changes can improve inventory and logistics management, and finally, the companies will be able to reduce operational costs (Jones et al., 2004). According to the research carried out by Kay in 2003, enterprises can reduce operational costs in the supply chain using RFID technology and gain an increase in profit from 2% to 7% through greater inventory visibility.
Regardless of the advantages of passive RFID technology in SCM, low-cost passive RFID technology is faced with a severe security issue due to a shortage of encryption techniques. Passive RFID technology should be preparing for two types of attacks: passive attacks such as eavesdropping and active attacks such as fraudulent tags or readers, DoS attacks, or tampering attacks.
RFID technology is essentially communication between reader and tag in order to exchange information. In the case of passive RFID, the reader’s signal is much stronger than the tag’s because the electricity of the tag comes from the reader. It is possible to receive information from reader to tag over a long distance. Therefore, passive RFID technology is at the risk of eavesdropping. One technique to combat this is the silent or blinded “tree-walking” algorithm presented by MIT (Weis
Protection against fraudulent tags and readers is challenging because of mutual authentication applications. The existing authentication techniques, AES and RSA, cannot be applied to low-cost RFID tags due to the shortage of logical gates. A few “low-cost, one-way, hash function” technologies already suggested by security specialists have not given a satisfactory performance. Recently, research has focused on mathematical methods. In the end, technicians should work hard to prepare a compromise proposal between cost and the amount of information in a tag. Moreover, the delicacy of computing equipment and the time taken can be key points to making efficient low-cost RFID tagging (Ranasinghe
Research on the hardware, including RFID tags, is required prior to considering defense against tampering attacks. A study of tamper-resistant hardware was carried out by the Cambridge University Tamper Laboratory. One measure is to insert a low-cost RFID tag into a product or package, as in euros (Chai, 2003). Denial of service (DoS) attacks are possible through such routes as RF sources, illegal broker tags, and stolen tags. However, these types of attacks can be detected by special purpose readers (Molnar, 2004).
The current wave of interest in security efforts for protecting enterprise information has spread, and a variety of academic studies have been performed. Until now, many enterprises have typically placed more emphasis on technology such as building security systems, installing computer vaccine programs, and establishing firewalls. However, this involves risk due to the increase in cyber attacks/threats and the growth in demand for the effective management of security. To fill this gap, various studies on individual behavior or the members of organizations that are utilizing security technologies continue to be as vigorous as ever (Goodhue, 1991; Straub & Welke, 1998). Employees must be motivated to set up reformative policies and carry out established policies (Amitaya & McCrohan, 2002).
As mentioned in the process part of this chapter, many firms are interested in total quality management (TQM). The secret of successful quality control is not the effort of certain quality check departments or quality check staff, but of all members in the organization. These issues can be applied to security matters in SCM. Therefore, three critical factors of human resources across the supply chain, senior management, employees, and suppliers, will be examined along with the government agencies’ side.
1) Senior management support
Martha and Subbakrishna (2002) report that process, technology, and individual education are the key points for building continuity and maintaining security. Moreover, they insist on the importance of senior management support and emphasize that most employees cannot recognize the seriousness of information security without senior management’s efforts and direction. Senior management must be on guard against the over-consumption of energy and resources regarding supply chain security. To entrust the CEO with full powers over the vice-president or senior manager of the security management department is an effective alternative in order to negate bias.
2) Employees
A company is composed of a number of employees, and the organization is hard-pressed to control these distinct individuals. The same approach might be applied to security. An organization needs to pay attention to hiring and screening employees. In order to achieve these goals, the company should formulate a standard policy for recruitment procedures and work from past experience to recruit the right people and improve security. After hiring, the company should then run an effective screening system. It is always better, people say, to be safe than sorry.
Well-trained staff members are directly related to efficient security systems in SCM, so security education for all employees in the organization is vital. Employees have to be able to understand the importance of security matters, respond effectively in difficult situations, and sometimes suggest their own efficient security solutions. Measures that help reach these aims include periodic workshops and education on security issues for new recruits and existing workers, rewards for effective suggestions and improvements, and the opportunity for information sharing.
3) Suppliers
Building a system for filtering suppliers’ security performance is a critical process for strong security. Elkin
A firm first formulates a manual for security procedures in case of emergency. Security processes are better if the company has regular meetings with suppliers. The meetings can include the discussion of matters such as system utilization, financial matters, managerial regulations, and technical problems. It is an important task to discuss and identify potential security threats across the entire supply chain. To deal with possible threats, both sides have to understand the current security vulnerabilities and build countermeasures.
4) Government agencies
Finally, government security initiatives are important for building continuity. The decisions of government agencies have significant influence over business because they enact and implement security rules. The most typical governmental program for security is the Customs-Trade Partnership Against Terrorism (C-TPAT) in America. This program is very similar to ISO 9000 certification, which is related to quality and arranged by the International Standards Organization. Applicants, which include importers, manufacturers, forwarders, and logistics companies, have to fill out official documents such as the letters of application and self-appraisals involved in their supply chain security practices in order to acquire certification. An inspector reviews the documents, checks whether the provided information is correct, asks for the rectification of faults, and then sometimes visits without advance notification. After verification, certified companies can get “faster processing at ports and border crossings,” and the government can more easily manage their relationship with the business participants.
This study suggests possible security solutions in supply chain management (SCM) based on the dynamic capabilities method created by Autry and Sanders. The method consists of three major factors: processes, technology, and human resources.
Up until now, many enterprises have typically placed more emphasis on technologies such as building security systems, installing computer vaccine programs, and establishing firewalls in order to prevent cyber threats. However, we should not overlook the importance of processes and human resources.
With processes, we can learn a good lesson from total quality management (TQM). In order to implement processes effectively, enterprises should manage all activities across the organization and the whole supply chain. Managing all processes in a supply chain well is an extraordinarily important issue in order to assist SCM systems.
More importantly, systems are operated by people, and people have a responsibility for system management. Therefore, the issues around the management of human resources are critical in terms of security in SCM systems. We are able to identify through an examination of various studies that the most serious problem in security matters is not a disaster caused by systems,but tragedy caused by employees. It is essential for business activity to motivate employees to set up reformative policies and carry out established policies. For motivating employees on information security in their organization, security education and reasonable rewards should be followed up with efficient processes and robust systems. This will help employees to recognize the risk of compromised information and provide personal experience so that they may continually strive to protect enterprise information.
2. The limitation of this study
We must discuss the limitations of this study. The study has been conducted via a review of the literature, so readers are not able to judge the degree of importance in the relationships between processes, technology, and human resources in SCM systems through this research. In other words, we mentioned the importance of processes and human resources in a previous chapter, but explicit evidence, such as statistical verification using a qualitative study or questionnaire or time-series analysis, was not provided.
Empirical study is vital to progress further meaningful study in terms of security in SCM systems. If such a study looks at the issue of employee attitudes toward enterprise information security based on proven models, such as the technology acceptance model (TAM), deterrence theory, or control theory approach, it would contribute greatly to future study.
First, researchers can present primary factors, such as the perceived usefulness and ease of use, through reviewing various studies based on the technology acceptance model and specific variables extracted from the deterrence theory, such as security policy, system, and education, from the perspective of usefulness and convenience. In addition, the control theory’s punishment and reward variables could be assessed to influence an employee’s attitude toward SCM system security.
Second, a questionnaire could be composed of factors extracted from a literature review. The survey could be carried out in many ways, such as collecting data for analysis through face-to-face interviews, online Internet surveys, telephone polling, and/or mailing. In order to provide more sophisticated empirical implications, essential prerequisites would be a perfect understanding of the sampling methods and a questionnaire vetted by an expert panel linked to the research subject to prevent bias.
Third, the researchers must try to distribute as many questionnaires as possible. The number and quality of collected data are critical factors to gain precise results. SPSS, which is a statistical package for social science, could test a basic statistical analysis, such as factor analysis and regression analysis. To analyze structural equation modeling, AMOS or LISREL software would be good tools.
We cannot foresee the results without empirical study. Factors such as security education, usefulness of reward, risk perception involved in security, and personal experience all may directly and positively affect an employee’s attitude toward enterprise information security in SCM. If we attain desired effects via statistical testing, enterprises should enhance security education and appropriate reward, which are essential for motivating employees on information security in an organization. This will help employees to recognize the risk of compromised information and provide personal experience so that they may continually strive to protect enterprise information.
The main purpose of this study is to define the concept of cyber threat, examine general types of cyber threat, identify possible cyber threats to the supply chain, and suggest practical solutions. It is not easy to define the term “cyber threat” because similar terms are being used among scholars, such as “cyber-terrorism”, “cyber-warfare,” and “information warfare.” Based on previous research, a cyber threat can be defined as a variety of risks in cyberspace posed by cyber-terrorism or cyber attack.
SCM systems can be exposed to miscellaneous cyber attacks. For instance, corporate confidential information and data can be stolen by competitors or malicious hackers hired by competitors for the purpose of trading information acquired from cyber attacks, and deliberate sabotage might be carried out by malicious users during failures or while a system is under repair. The most common cyber threats in SCM systems are explored in this study: inference attacks, password sniffing/cracking software, spoofing attacks, denial of service attacks (DoS), and direct attacks.
As we looked at the real examples in chapter 3 (i.e. Giordano International and Tesco cases), significant numbers of firms consider the absence of effective systems and processes above all. In practice however, companies have to reevaluate on the basis of the internal and external human behavior in their organizations. To bolster the security of an Internet-based SCM system, it is an important step for enterprises to identify significant security vulnerability and manage the systems through an integrated approach. Therefore, we suggest that the firm operates its own IT department if the company is small, but if the size of the enterprise is fairly extensive scale, it is more efficient to depute the task to a IT specialized-enterprise. The firm can streamline the processes as well. Finally, human resource management is one of crucial elements in order to maximize the security matters. Senior management supports and emphasis are the key points for building continuity and maintaining security. Well-trained staff members are directly related to efficient security systems in SCM, so security education for all employees in the organization is vital.