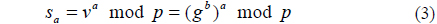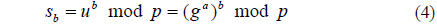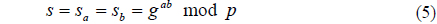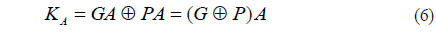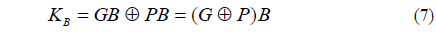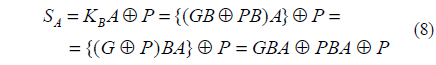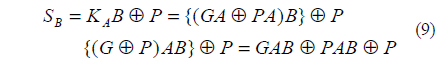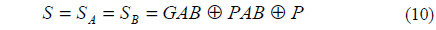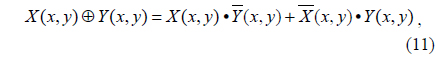Secure personal communication and information security of the public network are becoming more and more important with the progress in internet or mobile networks. According to demands for following such a trend of the times, information security technology has been developed for protecting information during data transmission in communication channels [1]. One of the cryptosystems was the private or symmetric key encryption method. In this method, two users, for example Alice and Bob, select a key in advance, which is their private key, then they use the key in a private key cryptosystem to communicate messages over the public channel. Sometimes they can change these keys periodically. However, this cryptosystem may have lost the private key when these keys are changed. To solve this problem, public key cryptography such as Diffie-Hellman key exchange protocol was introduced [2]. In this protocol, two users unknown to each other can set up a private but random key for their symmetric key cryptosystem. There is no need for Alice and Bob to meet in advance, or use some other secret means to select a key. In recent years, there has been increasing interest in the use of optical encryption methods for security systems [3-14]. In addition, we have presented several papers on the optical encryption techniques by using phase-shifting digital holography [15-19]. Optoelectronic methods using digital logic may be adequate for encryption. Some researchers reported XOR(exclusive OR)-based optical encryptions [20-22]. Recently, a technique using fractional Fourier transform based key exchange was reported [23]. However, until now there has been no other research to present an optical method of the Diffie-Hellman key exchange protocol.
In this paper, we propose a new optical secret key sharing method based on the Diffie-Hellman key exchange protocol, and show the performance of the proposed method. The secret key sharing algorithm is carried out optically by using dual free-space interconnected optical XOR logic operations. Section II is organized as three parts. In the first part, the Diffie-Hellman key exchange algorithm is overviewed. The second part explains the proposed optical secret key sharing method. In the third part, we propose an optical schematic and a compact optical module of the proposed system and explain the optical secret key sharing process. In Section III, computer experiments confirm the performance by showing results of the shared secret key generation with the proposed method. Finally, conclusions are briefly summarized in Section IV.
2.1. Diffie-Hellman Key Exchange Protocol
In 1976, Diffie and Hellman introduced a key exchange protocol [2]. The protocol is a specific algorithm of exchanging cryptographic keys. The Diffie-Hellman key exchange algorithm allows two users to exchange a shared secret key over an insecure communications medium without any prior secrets between each other. As to secret messages encryption, this shared key can be used to encrypt subsequent communications using a symmetric key cipher. In this protocol, two users(i.e., Alice and Bob) wish to communicate with each other but do not want an eavesdropper(i.e., Eve) to know their message. To do this, they will agree upon and set up a random secret key for their private key system, using a public but authenticated channel. The Diffie-Hellman key exchange algorithm is as follows.
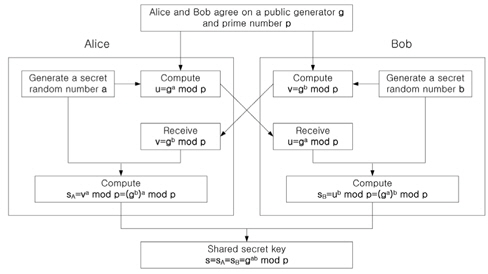
1. Alice and Bob agree upon and make public two numbers g and p, where g is called a generator and p is a prime number. Note that anyone has access to these numbers in public.
2. Alice chooses a random number a and computes u by modulo p and sends it to Bob.
3. Bob chooses a random number b and computes v by modulo p and sends it to Alice.
4. Alice computes a secret key sa by the same modulo p.
5. Bob computes a secret key sb by the same modulo p.
6. Now both Alice and Bob have the same shared secret key, namely s.
7. Both Alice and Bob store this shared secret key as a private key, and it will be used in message encryption to each other.
Figure 1 shows the Diffie-Hellman key exchange algorithm. As you see in Fig. 1, Alice generates a random number
2.2. Proposed Optical Secret Key Sharing Method
Fundamentally, it is very difficult for the Diffie-Hellman key exchange algorithm to be implemented by optical means due to two main reasons. The first one is that there is no proper method to perform modulo arithmetic by optical techniques. The second is that it is hard to represent a prime number on an optical device properly. It may be possible to encode the prime number into binary digits by conversion. Despite these difficulties, we propose an optical secret key sharing method by modifying the Diffie-Hellman key exchange algorithm. In the proposed method, the conventional Diffie-Hellman key exchange algorithm can be modified to an optically realizable algorithm, where modulo arithmetic can be substituted with an XOR logic based encryption simply. Therefore, modulo arithmetic is mathematically replaced by the XOR logic operation, that is, modulo two addition. Specifically, XOR-only encryption schemes will be perfectly secure if and only if the key data is perfectly random and never reused. When we apply the XOR-based encryption method to the above Diffie-Hellman key exchange algorithm, the modified Diffie-Hellman key exchange algorithm proposed in this paper can be described as follows.
1. Alice and Bob agree upon and make public two numbers G and P, where G is a generator number which is generated randomly and P is also a random number instead of a prime number. Note that anyone has access to these numbers in public.
2. Alice chooses a random number A and computes firstly GA and PA by Boolean AND logic operation. Next, Alice computes a public key KA by XOR logic operation of these two values, and sends it to Bob.
3. Bob chooses a random number B and computes firstly GB and PB by Boolean AND logic operation. Next, Alice computes a public key KB by XOR logic operation of these two values, and sends it to Alice.
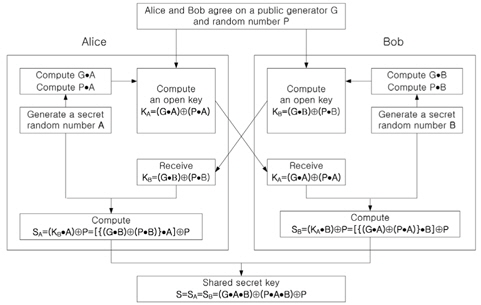
4. Alice computes firstly KBA by AND logic operation and computes a secret key SA by XOR operation with P.
5. Bob computes KAB firstly by AND logic operation and computes a secret key SB by XOR operation with P.
6. Now both Alice and Bob have the same shared secret key, namely S.
7. Both Alice and Bob store this shared secret key as a private key, and it will be used in message encryption.
Figure 2 shows the modified Diffie-Hellman key exchange algorithm, and Fig. 3 shows the flow charts for the proposed optical secret key sharing method. As shown in Fig. 2, Alice generates a secret random number A which is not open to public. Then, Alice pre-encrypts this random number A with a generator G and a random number P by AND logic operation at first. With these pre-encrypted values, GA and PA, Alice encrypts her own secret random number A again by XOR logic operation in order to open her public key KA. Alice sends this double encrypted key information KA to Bob as public key. From the received Alice’s public key, Bob computes a secret key SB by AND operation with his secret random number B and its sequent XOR operation with P. Similarly, Alice computes a secret key SA by Bob’s public key, and this key is as same as Bob’s secret key to share. Also, Fig. 3 shows that the proposed method has a realizable optical setup to provide the open public key and the shared secret key at the same time. In our proposed secret key sharing method, we use an XOR-based double encryption. This technique is very similar to the triple DES (Data Encryption Standard) algorithm and was reported in the previous paper [22]. Most 3DES algorithms use two security keys. Double encryption by two security keys gives us much security strength, and it is much harder to break the key. If Eve wants to compute the secret key S, she must know either a random number A or a random number B. Although Eve notices the set {KA, KB}, which is now open to public, it is hard to get A and B from the set {G, P, KA, KB} because these secret numbers are double encrypted. The longer the length of these random numbers is, then Eve requires very much mojavascript:;re time to break.
In our proposed method, one of the advantages is that it is a more advanced cryptosystem to exchange keys compared to the conventional Diffie-Hellman protocol because our method uses double encryption in making the public key and the shared secret key. Another advantage of this method is that it is convenient to change Alice’s and Bob’s secret random numbers in producing the public key and to exchange the public key without knowing the other user’s private key directly. This means this method has a property that users can change the secret random numbers at their own discretion. The last merit is that the proposed optical method has an expansibility of key length in 2-dimensions, which strengthens the security of the cipher system.
2.3. Optical Implementation of the Proposed Method
Generally, an optical information processing system has an inherent advantage of 2-dimensional (2-D) data processing and fast parallel information processing time. This implies that the optical encryption system can have huge key length and vast data processing in the cryptosystem. For this reason, the public key and the shared secret key lengths can increasingly be chosen by expanding these keys to 2-D array, but this 2-D expansion does not increase processing speed. With these properties, we propose an optical implementation of the modified secret key sharing method which has 2-D page-typed input format, resulting in the same 2-D arrayed public key and the shared secret key output formats.
In this paper, the main idea of the proposed method is that the modified Diffie-Hellman key exchange algorithm is implemented in an optical way by using the bitwise XOR-based encryption technique with a free-space interconnected optical logic gate method. The advantage of the free-space interconnected optical logic gate method is that no cell encoding-decoding process is required and the output has the same format as the input. In the optical configuration of a logic gate, binary input variables are spatially dual encoded by using two’s complement [22]. The architecture of XOR logic operation can be made by combining the logic AND scheme with the logic OR scheme. The 2-dimensional XOR logic operation is expressed as follows simply.
where symbols •, +, and ⊕ represent AND, OR and XOR logic operations, and means the complement of
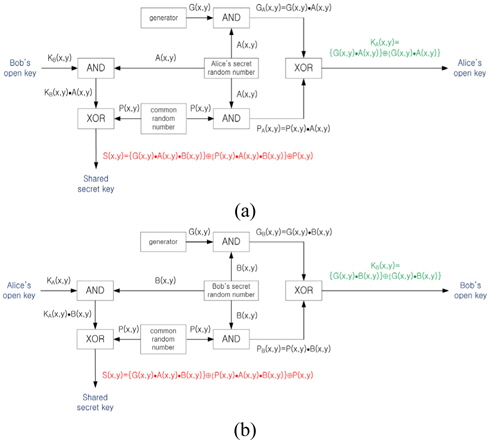
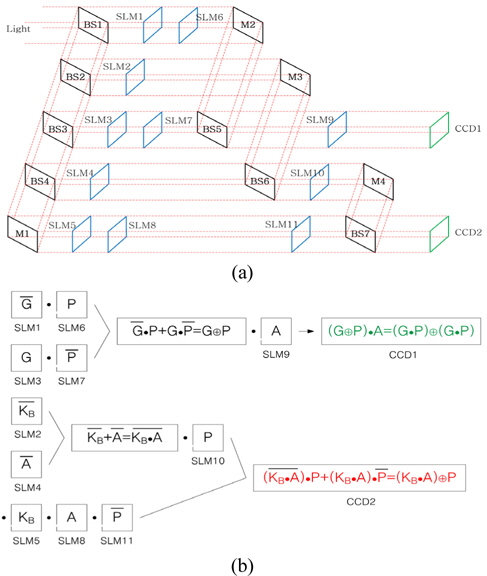
Referring to the modified Diffie-Hellman key exchange algorithm by using XOR logic operations shown in Fig. 2, we design the proposed optical Diffie-Hellman key exchange configuration with optical components such as mirrors, beam splitters(BSs), and spatial light modulators(SLMs). In this configuration, all the SLMs are used as free-space interconnected optical logic gates. Figure 4(a) shows the optical schematic for the proposed optical Diffie-Hellman key exchange method so as to generate an open public key and a shared secret key simultaneously, which is based on the dual free-space interconnected AND, OR and XOR logic operations for binary data. Schematically, the optical setup contains three Mach-Zehnder type interferometers. Four beam splitters BS1, BS2, BS3 and BS4 divide a collimated light into two lights and three beam splitters BS5, BS6 and BS7 combine these divided lights into one light, resulting in records on two CCDs. Also, this architecture is composed of eleven SLMs which are used for displaying data inputs.
In order to investigate operating principles of the optical schematic, the flow charts for the proposed optical secret key sharing method shown in Fig. 3 are considered. For convenience, let us consider Alice’s open public key and shared secret key generation procedure shown in Fig. 3(a). In Fig. 4(a), the collimating light, after being reflected by the beam splitters and the mirrors, illuminates and passes through the SLMs, where all the SLMs are arranged with a purpose of operating optical AND, OR and XOR logics as free-space interconnected optical logic gates. When the light continuously passes two SLMs in series, optical AND logic operation is obtained by inner production pixel by pixel. On the other hand, the combining beam splitter performs the optical OR logic operation by adding two lights in parallel. As a result, the integration of these processes is equivalent to the optical XOR logic operation obtained by the combination of two logic ANDs and one logic OR. First, Alice pre-encrypts her secret random number(
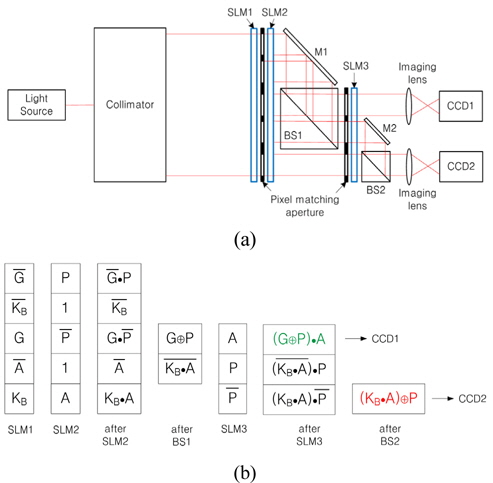
The proposed optical schematic for the secret key sharing method shown in Fig. 4(a) can also be fabricated in the form of an optical module. This module is implemented by rearranging the optical elements geometrically and by reducing the number of SLMs and mirrors. Figure 5(a) shows the simplified optical module for the proposed Diffie-Hellman key exchange architecture. In this module, pixel matching apertures are placed in front of SLMs for the purpose of blocking the unwanted diffraction wave propagation and of pixel matching between SLMs, and the imaging lens plays a role of another pixel matching between output image pattern and CCD pixel array. The advantage of this module is that it can be manufactured compactly and can be used for realistic applications. Figure 5(b) shows representations of input SLMs’ data and output CCDs’ data in the process of light propagation, and also it shows light distribution after passing through SLM2, BS1, SLM3 and BS2.
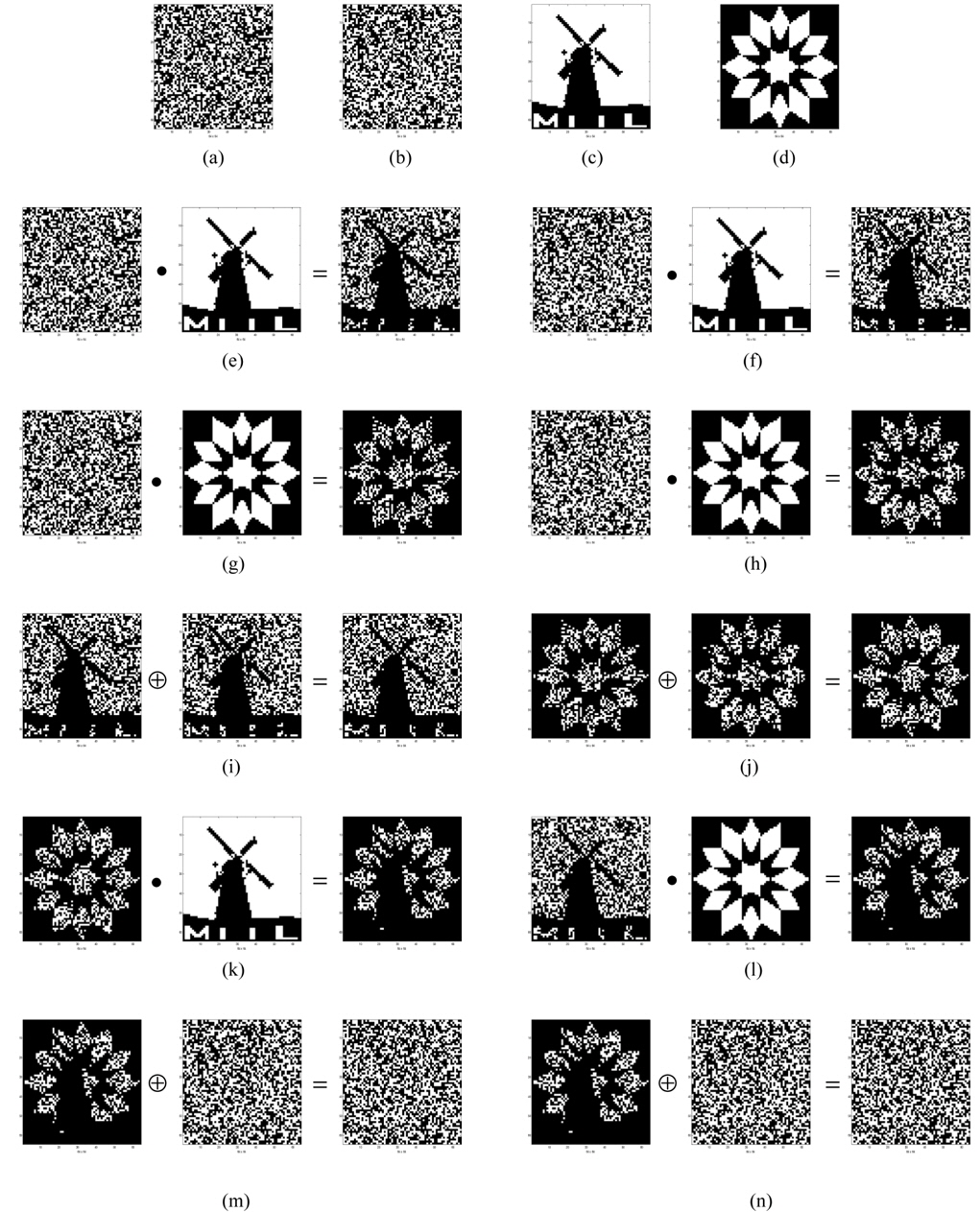
In order to verify the proposed method and show the effectiveness in the modified Diffie-Hellman key exchange system, we carry out numerical simulations. In our method, input data to be processed is binary bit data or a binary image. In computer simulations, all input data have the form of page-typed 2-D arrays which consists of 64×64 binary pixels for convenience. This data size provides the total heights of SLM1 and SLM2 shown in Fig. 5(a) with 64×5=320 pixels, which is easily obtained by the practical SLM. Also, this means the security key length has 64×64=4,096 bits which is very much longer key length compared to the conventional electronic cryptography. For example, the conventional 1-D key length for the RSA public key cryptosystem has 512 bits, 768 bits or 1,024 bits. If we expand the data size to 128×128 pixels array, then the height of SLM increases twice to 128×5=640 pixels which is also allowable in the practical SLM, and the key length increases to 16,384 bits surprisingly.
A generator
In this paper, we propose a new optical secret key sharing method based on the Diffie-Hellman key exchange protocol required in encryption systems. The proposed optical secret key sharing method is realized by using optical XOR logic operations to modify the Diffie-Hellman key exchange algorithm, where XOR logic operation is implemented by using a free-space interconnected optical logic gate method. The optical schematic of the proposed method consists of three Mach-Zehnder type interferometers to perform dual XOR logic operations. Also, we present a compact type of optical module. Schematically, the proposed optical module has a merit of being able to produce the open public key and the shared secret key simultaneously with a compact form. Our proposed key exchange system uses a kind of double key encryption technique which consequently enhances security strength. This can provide a higher security cryptosystem than the conventional Diffie- Hellman key exchange protocol due to the double encrypted complexity of a shared secret key. Also, the proposed optical configuration has 2-D array data format which can increase the key length easily to strengthen the security system. In addition, 2-D expansion of data size does not increase information processing time owing to parallel processing property despite increase in 2-D data. Another advantage of this method is that it is convenient to change the user’s secret random number in generating the open public key and to exchange the public key without knowing the other user’s private key directly. This means our method has a property that users can change secret random numbers at their own discretion. Computer experiments verify that the proposed method is effective and suitable for the Diffie-Hellman key exchange system and secure communication system. To the best of our knowledge, this proposed optical schematic may be the first report on the Diffie-Hellman key exchange protocol by optical means.