In this paper, we examine the problems of the low energy adaptive clustering hierarchy (LEACH) protocol and present ideas for improvement by selecting the cluster head node. The main problem with LEACH lies in the random selection of cluster heads. There exists a probability that the formed cluster heads are unbalanced and may remain in one part of the network, which makes some part of the network unreachable. In this paper, we present a new version of the LEACH protocol called the improved LEACH (ILEACH) protocol, which a cluster head is selected based on its ratio between the current energy level and an initial energy level, and multiplies by the root square of its number of neighbor nodes. The simulation results show that the proposed ILEACH increases the energy efficiency and network lifetime.
Wireless sensor network (WSN) [1-3] consist of hundreds and even thousands of tiny devices called sensor nodes distributed autonomously to monitor physical or environmental conditions, such as temperature, sound, vibration, pressure, and motion at different locations. Energy plays an important role in wireless sensor networks because nodes are battery operated. Consequently, many protocols have been proposed in order to minimize the energy consumption of these nodes.
Each node in a sensor network is typically equipped with one or more sensors, radio transceiver devices, a small microcontroller, and an energy source. Since in most WSN applications, the energy source is a battery, energy plays an important role in wireless sensor networks, and conserving the energy consumed by each node is an important goal that should be considered when developing a routing protocol for WSNs.
In general, routing in WSNs [4] can be classified into flat, hierarchical, and location-based routing, depending on the network structure. Hierarchical routing is a well-known technique with special advantages related to scalability and efficient communication. Low energy adaptive clustering hierarchy (LEACH), power-efficient gathering in sensor information systems (PEGASIS), threshold sensitive energy efficient sensor network protocol (TEEN) [5], and APTEEN use this technique for routing. In hierarchical architecture, higher energy nodes can be used to process and send the information, while low-energy nodes can be used to perform the sensing in the proximity of the target.
In this paper, we propose the improved LEACH (ILEACH) protocol that selects cluster heads using different thresholds. The new cluster head selection probability is calculated from the initial energy and the number of neighboring nodes. On a rotating basis, a head-set member receives data from the neighboring nodes and transmits the aggregated results to the base station. For a given number of data collecting sensor nodes, the number of control and management nodes can be systematically adjusted to reduce the energy consumption, which increases the network life.
The remainder of this paper is as follows: Section II related work, Section III will introduce the network model, Section IV will introduce the LEACH routing protocol in detail, Section V will introduce the ILEACH protocol, and Section VI describes the simulation analysis done by varying the percentage of cluster heads in the network in each simulation of the LEACH and ILEACH protocols. Performance is analyzed in terms of lifetime, energy dissipation, and throughput of the network, and Section VII concludes this paper.
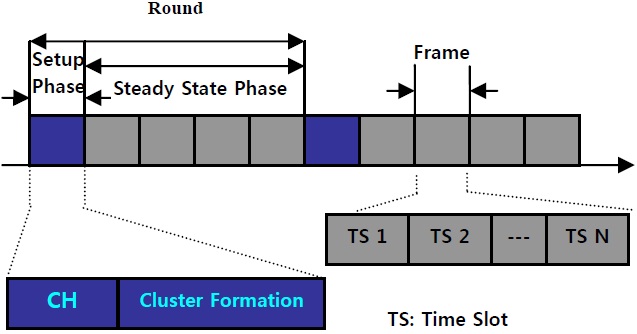
LEACH is a distributed clustering protocol that utilizes randomized rotation of local cluster heads (CHs) to evenly distribute energy utilization among the nodes of WSNs [6,7]. It uses one-hop inter-cluster communication towards the sink. The whole operation of the LEACH protocol is divided into rounds. Each round consists of a setup phase and a steady state phase.
The number of nodes that remain alive using LEACH is significantly larger (four to eight times larger) than that using static clustering or minimum transmission energy (MTE) routing. However, the main problem with the LEACH protocol lies in the random selection of CHs. There exists a probability that the CH formation is unbalanced and may remain in one part of the network, making some part of the network unreachable. One-hop inter-cluster and intracluster used in LEACH are also not applicable for large region networks.
A new adaptive strategy known as LEACH-B has been proposed; it chooses CHs and varies their election frequency according to the dissipated energy [8]. Moreover, an improved LEACH scheme was proposed, named LEACH-C [9]. In LEACH-C, a centralized algorithm at the base station performs cluster formation. However, the LEACH-C is not feasible for larger networks because nodes far away from the base station will have problems when sending their states to the base station. Since the role of the CHs rotates among nodes, the nodes far away from the base station will also not connect to the base station quickly, which results in increasing the latency and delay.
Further, the clustering protocol known as LEACH-E was proposed by Beni Hssane et al. [10]. In this protocol, the CHs are elected according to the energy left in each node. The drawback of LEACH-E is that it requires the assistance of a routing protocol by which the total energy of network should be distributed to each node.
Distributed efficient clustering (DEEC) is a dedicated design for energy heterogeneous scenarios, where nodes are initialized at various energy levels [11]. However the DEEC scheme may not ensure the selection of energy-rich CHs and the evenness of CH dispersion. The DEEC scheme also prevents cluster heads from being too close to each other, but ignores a cluster head’s energy qualifications.
Lindsey and Raghavendra [12] proposed PEGASIS. PEGASIS makes a communication chain using a traveling sales person heuristic. Each node only communicates with two close neighbors along the communication chain. Only a single designated node gathers data from other nodes and transmits the aggregated data to the sink node.
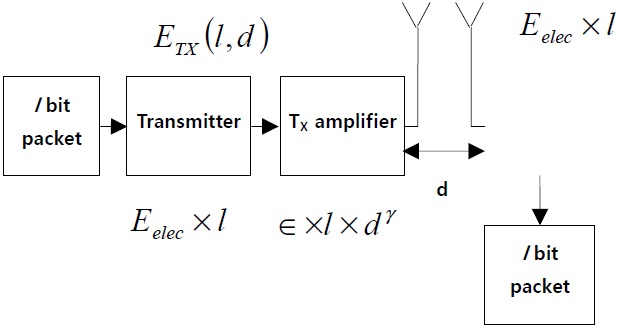
Let us assume a simple model for radio hardware energy consumption where the transmitter dissipates energy to run the radio electronics and the power amplifier, and the receiver dissipates energy to run the radio electronics. For our experiments, depending on the transmission range, we have considered the free space and multipath fading model, as shown in Fig. 1.
If the distance
where
The LEACH protocol for sensor networks, proposed by Heinzelman et al. [13], minimizes energy dissipation in sensor networks. It partitions the nodes into clusters, and in each cluster, a dedicated node with extra privileges called a cluster head (CH) is responsible for creating and manipulating a time division multiple access (TDMA) schedule and sending aggregated data from the nodes to the base station (BS) where these data are needed using code division multiple access (CDMA). The remaining nodes are cluster members. CHs change randomly over time to balance the energy dissipation of nodes. The node chooses a random number between 0 and 1. The node becomes a CH for the current round if the number is less than the following threshold:
where
This protocol is divided into rounds, where each round consists of setup phase and steady state phase.
During this phase, each node decides whether or not to become a CH for the current round. This decision is based on choosing a random number between 0 and 1, and if the number is less than a threshold
The CH node sets up a TDMA schedule and transmits this schedule to all the nodes in its cluster, completing the setup phase, which is then followed by a steady-state operation.
The steady-state [14] operation is broken into frames, where nodes send their data to the CH at most once per frame during their allocated slot shown in Fig. 2. It assumes that nodes always have data to send, and they send it during their allocated transmission time to the CH. This transmission uses a minimal amount of energy. The radio of each non-CH node can be turned off until the node’s allocated transmission time, thus minimizing energy dissipation in these nodes. The CH node must keep its receiver on to receive all the data from the nodes in the cluster. When all the data has been received, the CH node performs signal processing functions to compress the data into a single signal. For example, if the data are audio or seismic signals, the CH node can beam form the individual signals to generate a composite signal. Since the BS is far away, this is a high energy transmission.
In this section, we propose the improved LEACH (ILEACH) protocol, which is based on the initial energy and number of neighbors of the nodes. This protocol is more applicable than any type that assumes a protocol in which each node knows the total energy of the network and then adapts its election probability of becoming a cluster head according to its remaining energy. In the ILEACH protocol, we assign a weighting probability to each node. This weighting probability must be equal to the initial energy of each node divided by the initial energy of the normal node. The weighting probabilities for normal and advanced nodes can be given as
In Eq. (4), we replace
where,
rounds of the epoch,
rounds per epoch and the average number of CHs for normal nodes per round per epoch is equal to
Similarly, the threshold for advanced nodes is
where,
rounds. Here,
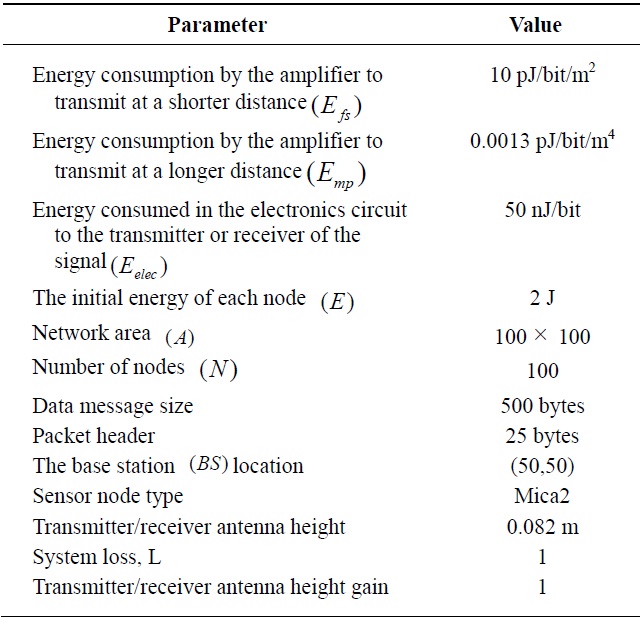
In this section, we evaluate the performance of the new energy efficient protocol implement in the MATLAB (MathWorks, Natick, MA, USA) environment. We assume that all nodes always have data to send and sensor devices do not have mobility. Further, the same initial energy and the capability of transmission range adjustment are assumed among nodes. The simulation parameters that we consider are summarized in Table 1.
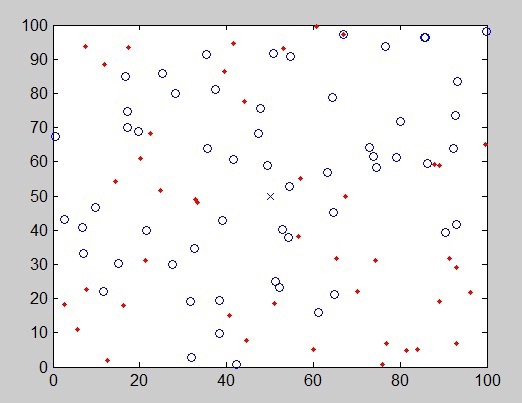
Fig. 3 shows the node deployments for simulation where the random distribution of 100 nodes is used and the BS is located in (50, 50) [13,14].
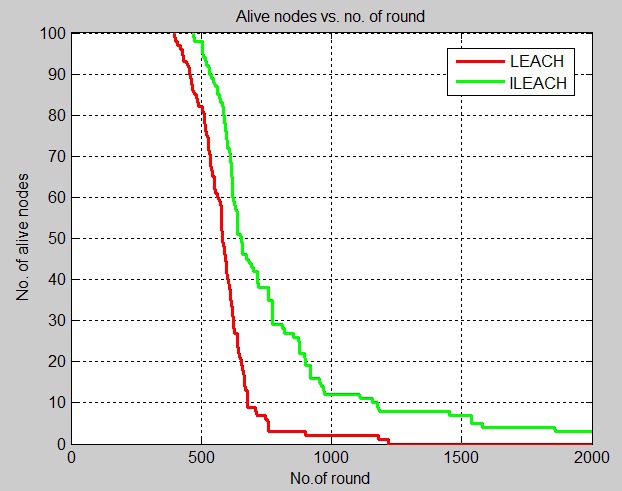
Fig. 4 shows that the first dead node appears at round 800 in LEACH while the first dead node appears at round 1700 in ILEACH in the case that the networking size was 100 m × 100 m and each node has the energy of 0.25 J. Therefore, the performance of ILEACH is better than that of LEACH.
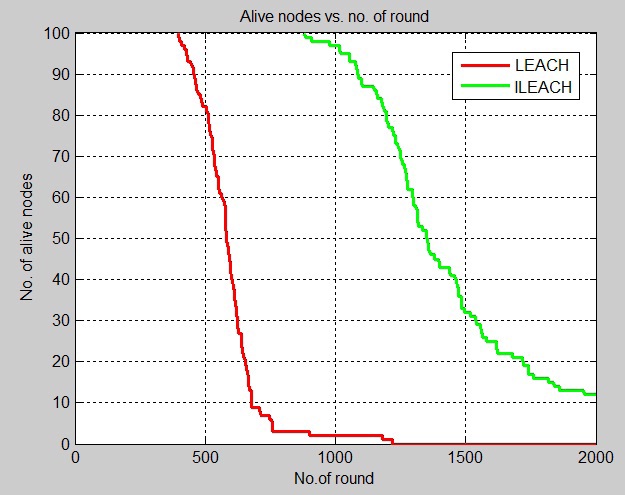
Fig. 5 shows that the first dead node appears at round 1100 in LEACH while the first dead node appears after round 2100 in ILEACH when each node has the energy of 0.5 J. Therefore, the performance of ILEACH is also better than that of LEACH in this case.
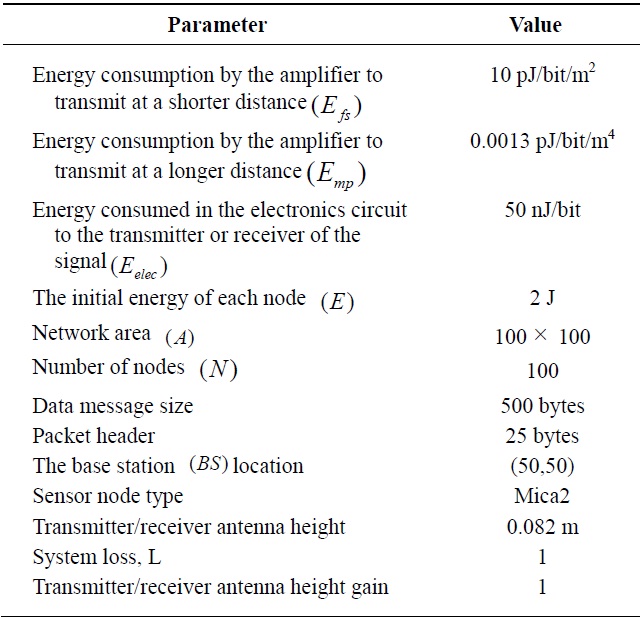
Parameter settings
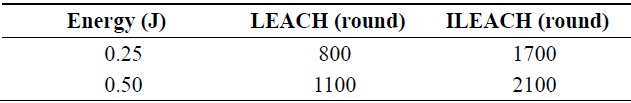
The simulation results in Table 2 show that the performance of ILEACH has an improvement of 31% and 40% over LEACH in the area of 100 × 100 m with an initial energy of 0.25 and 0.50 J, respectively.
[Table 2.] First node death of the LEACH and ILEACH protocols
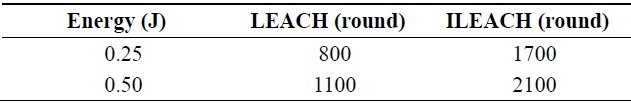
First node death of the LEACH and ILEACH protocols
In this paper, we considered a well-known protocol for WSNs called the LEACH protocol, which is the first and the most important protocol in WSNs to use a cluster-based broadcasting technique. Followed by an overview of the LEACH protocol implementation, we proposed a new version of the LEACH protocol called the improved LEACH (ILEACH) protocol. From the simulation results, we can draw a number of conclusions. In the first case that each node has 0.25 J, the first dead node appearing at 1700 rounds with ILEACH is better than the first dead node appearing at 800 rounds with the original LEACH protocol. In the second case that each node has 0.25 J, the first dead node appearing at 2100 rounds with ILEACH is better than the first dead node appearing at 1100 rounds by the original LEACH protocol. Therefore, it can be observed that there is a significant improvement in the network lifetime in the case of the ILEACH protocol comparison to the LEACH protocol.