As application-specific requirements for wireless sensor networks emerge, both real-time and reliable communications become major research challenges in wireless sensor networks due to the many constraints on nodes and wireless links. To support these services, several protocols have been proposed. However, since most of them were designed as well as developed for general purpose applications, it is not recommended that they be directly adapted to applications with special requirements. In this paper, we propose a way to extend the current reliable transport protocol to cover a special real-time service, the (m,k)-firm deadline stream, in wireless sensor networks. While the proposed scheme is basically built on the PSFQ protocol for reliability, some features have been newly developed to support the (m,k)-firm stream efficiently. Finally, simulation results are given to demonstrate the feasibility of the proposed scheme in high traffic and with failed links.
In recent years, significant developments in wireless and electronics communications have enabled the expansion of limited-power and small-sized sensor nodes. A large number of these sensor nodes are deployed in a single geographic area and are utilized in a wide range of applications including monitoring physical and artificial environmental phenomena, events, and vehicle tracking [1]. This kind of network is called a wireless sensor network (WSN).
A sensor node is a small device that is able to perform essential functions such as environmental monitoring, mobile target tracking, smart space, and ubiquitous computing. The most noteworthy drawback of the wireless sensor network is that each sensor node is capable only of low-rate, short-range wireless communication. This feature inherently hinders reliability, which implies messages sent by a sender should be delivered to the destination without errors during transmission. Moreover, since reliability is generally influenced by many different factors such as channel loss, interference, bandwidth limitations, traffic peaks, and node resource constraints, a complementary scheme needs to be implemented in each layer in order to cover unreliable and resource-constrained networks. On one hand, to guarantee reliability, several fundamental mechanisms and tunable parameters have been proposed to be applied to wireless sensor networks in conjunction with well-known existing schemes. They include rate control, scheduling policy, drop policy, explicit notification, acknowledgments, MAC backoff, and next-hop selection. In parallel with research efforts in the transport layer, several routing protocols have been proposed to address the reliability problem.
In addition to reliability issues, real-time service has attracted researchers’ interests as many applications have emerged in wireless sensor networks such as monitoring and tracking. Current research works on real-time delivery are mainly focused on a network layer approach since most of the delivery time is consumed in this layer. In this layer, two kinds of approaches have been proposed to provide real-time service. One is real-time scheduling based on priority since queuing delay is the biggest component of end-to-end delay. The other scheme for real-time communication is real time routing, which is designed to find an adequate path guaranteeing end-to-end delay.
Since reliability has been closely related to real-time service, both issues should be explored together. However, few studies have been conducted that have addressed the above problem. The main example is known as VIGILNET, which is network architecture for real-time delivery. Its main mission is tracking operations and it was developed at the University of Virginia [2]. Military operations, including real-time tracking and observation, are major targets of VIGILNET. A mathematical model and threshold partition method were proposed to meet deadlines for end-to-end delay.
Based on the results of previous research, many schemes have been proposed by adapting existing approaches to WSNs to provide both services. Their major contributions are to modify existing schemes in order to meet the constraints of sensor nodes as well as the requirements of specific applications. As a result, current approaches for real-time and reliable delivery can be considered as approaches to extending existing schemes. Therefore, they naturally have several drawbacks to be mentioned because sensor networks have specific requirements as opposed to the general requirements of previous network designs.
Motivated by the above needs, we take the (
Thus, building on our previous work, the author proposes an approach to combining reliable and real-time services to support an (
The rest of this paper is organized as follows. In section II, several studies are briefly explained. The proposed scheme will be described in section III. The performance evaluation through simulation will then be given in section IV. Finally, we draw a conclusion in section V.
In this section, the research work on reliable and real-time delivery is overviewed. First, PSFQ and the reliable multi-segment transport (RMST) mechanism [8] were proposed to guarantee reliability in the transport layer. In PSFQ, a segment is divided into smaller multiple segments while providing sufficient time to detect a loss over an intermediate node. Another approach, referred to as RMST, includes several reliability schemes based on automatic repeat request (ARQ) and not acknowledge (NACK). On the other hand, schemes such as adaptive rate control (ARC) [9] and event-to-sink reliable transport (ESRT) [10] have been proposed to control congestion in the transport layer. In the ESRT scheme, the domain for reliability is sectoring into four regions, which consist of uncongested subthreshold, uncongested overthreshold, congested overthreshold, and congested subthreshold. Depending on the current region, a sink provides feedback to the source directly to control congestion. The hybrid reliable routing (HRR) technique [11] is designed as to construct a hierarchical network architecture rather than a flat one under the assumption that a cluster architecture can guarantee reliability by communicating between cluster headers having more power and a higher data rate on wireless communication radio. Another receiver-oriented load-balancing and reliable routing (RLRR) [12] protocol has been proposed to achieve both load balancing and reliability for large-scale WSNs. Other approaches have been proposed for developing routing protocols, which make use of either a multipath approach or a new metric suitable for reliability in wireless sensor networks. The authors in [13] presented the directed transmission routing protocol (DTRP), introducing parametric and probabilistic approaches. DTRP is a multipath proactive routing protocol specially designed for WSNs to provide improved scalability and reliability. Different from typical routing protocols, DTRP uses the beacon packet not to resolve the next hop node for the destination but to provide only the hop-count distance value between the sink and other sensor nodes.As for an approach with a new metric, the MintRoute protocol was proposed in [14]. To estimate the link quality, the average packet reception ratio is measured through periodic beacon messages and the link cost is set to this value.
SPEED [15] and Multi-Path and Multi-SPEED (MMSPEED) [16] are quality of service (QoS) based routing protocols that provide soft end-to-end deadline guarantees for real-time packets in sensor networks. Both use a geographic forwarding mechanism to route packets to the sink. SPEED ensures a network-wide speed of packet delivery for a real-time guarantee, i.e., it calculates the end-to-end delay by dividing the distance to the sink by the speed of packet delivery before making any admission decision. SPEED can also provide congestion avoidance when the network is congested. MMSPEED is an extension of SPEED; therefore, MMSPEED generalized the single network-wide speed approach of SPEED by replicating and using multiple SPEED layers that run independently of each other. For delivery timeliness, MMSPEED provides multiple network-wide packet delivery speed options for different traffic types according to their end-to-end deadlines. For QoS reliability, multipath forwarding is used to control the number of delivery paths based on the probability of reaching end-to-end. However, neither SPEED nor MMSPEED consider an energy consumption metric or the lifetime of the WSN.
In related work on the (
In this section, we explain the proposed scheme through the following algorithms. The proposed algorithm is based on the following assumption: that the (
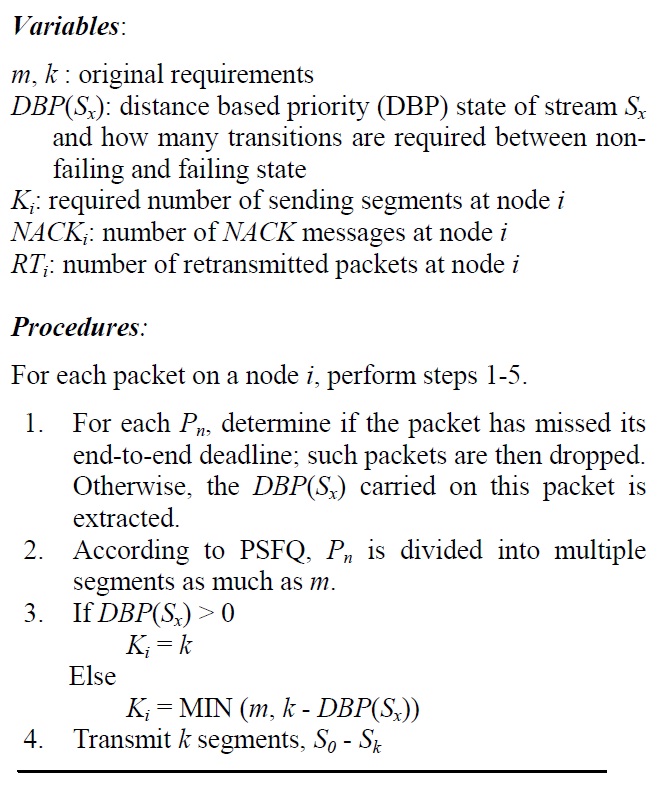
[Algorithm 1:] Procedures at the intermediate node
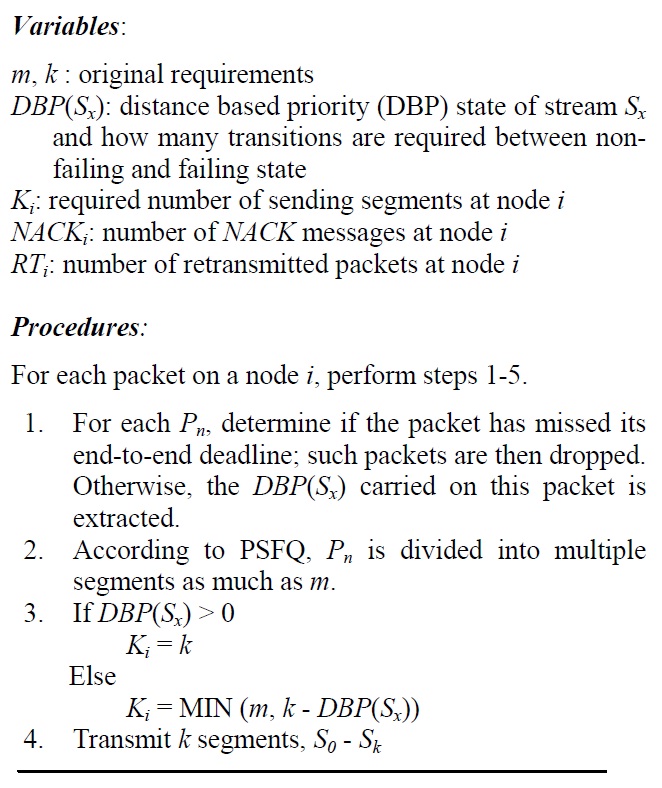
Procedures at the intermediate node
Step 1: When an intermediate node receives a packet, it checks the deadline for real-time service. If the elapsed time is over the deadline, a packet is dropped. Otherwise, several variables carried on this packet are extracted.
Step 2: Based on PSFQ, a packet is divided into sub-segments as much as k, the requirement.
Step 3: If the current stream status is considered to be sufficient, the number of segments that should be delivered to next hop is set to k, the original requirement. This means that the minimum number of segments will be considered for the (m,k)-firm stream. Otherwise, if a stream does not meet the requirement, this packet is very critical for the requirement. Thus, a stronger and stricter requirement is given by considering the current DBP value. The smaller the DBP value a stream has, the more packets should be delivered to next hop within the deadline. The maximum number of packets cannot exceed m packets.
Step 4: All of the segments are transmitted to the next hop over the link.
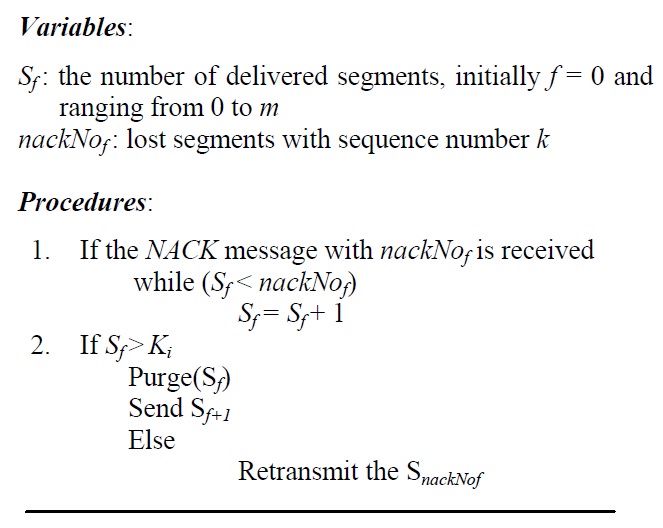
[Algorithm 2:] Deciding on retransmission
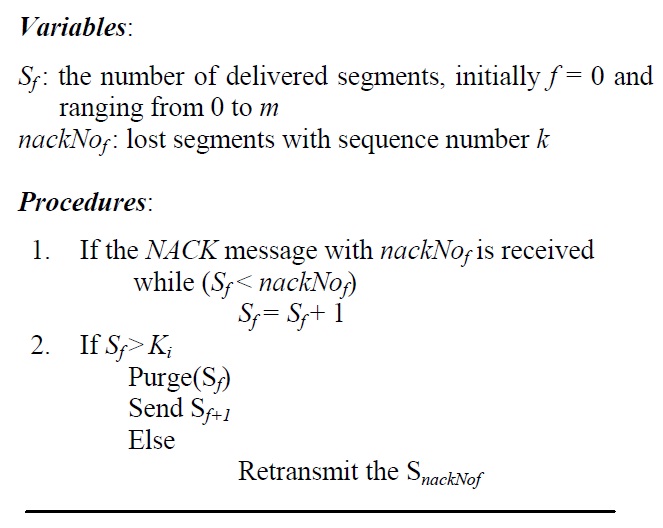
Deciding on retransmission
Based on the basic operational functions in PSFQ, a segment will be recovered in a hop-by-hop manner. Algorithm 2 shows how a
The main function of (
>
A. Simulation Model and Environment
In order to evaluate the performance of our proposed algorithm, we conducted simulations in Qualnet. We implemented our code in the Qualnet simulator [17] for diverse simulations. The simulation parameters and each protocol variable are described as follows. Our simulation modeled a network of 100 nodes placed randomly within a 1,000 m × 1,000 m area. The radio propagation range for each node was 100 meters and the channel capacity was 250 kbps. General carrier sense multiple access (CSMA) was used for medium access control (MAC) protocols and the two-ray model was used for propagation models to reduce the effect of the MAC and physical protocol. The application used for the proposed simulation was SURGE, which reports the sensing information at a predetermined rate. Unless otherwise specified, the mean period of a stream is 50 ms inter-arrival time between packets. The simulation parameters were derived from the sQualnet model [18], which was obtained from a datasheet in the MICA2 motes. The MICA2 has a CC2420 radio chip, which is made by ChipCon (Oslo, Norway) and is ZigBee compliant. It operates in the 2.4 GHz band and has a link capacity of 250 kbps using a spread spectrum and offset quadrature phase-shift keying (OQPSK) modulation for tolerance to interference. The CC2420 has a maximum outdoor range of 125 m with a maximum current draw of 17.4 mA (0 dBm). These ranges are based on the reception strength threshold. In this way, the simulation model is compliant to the actual sensor network model.
Each simulation was executed for 20,000 seconds. Multiple runs with different seed numbers were conducted for each scenario and the data obtained was averaged over those runs. Furthermore, the 95% confidence intervals of the mean were computed. A simulation was conducted to determine whether the proposed scheme could guarantee the (
The deadline for the real-time packet on each node is set to average-link-delay × number of shortest hops, respectively. The average-link-delay was computed by conducting several simulation scenarios. The first experiment evaluated the performance of a proposed scheme in the point of dynamic failure probability. Dynamic failure is said to the case when fewer than m out of any k packets meet their deadline. Thus, dynamic failure probability is represented as what percent of packets are delivered while meeting the (
>
B. Simulation Results and Analysis
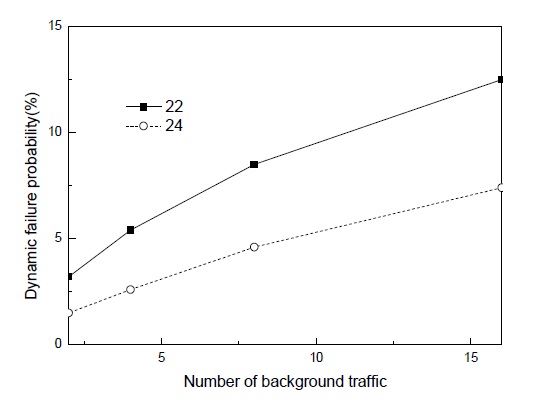
In Fig. 1, we evaluated the performance, specifically, how much real-time traffic was delivered within the deadline. The x-axis represents the amount of background SURGE traffic and the y-axis, the dynamic failure probability, while the 22 indicates the (2,2)-firm stream and the 24, the (2,4)-firm one. As shown in Fig. 1, the proposed scheme derives the acceptable performance from the dynamic failure probability. However, the failure probability increases as the amount of background traffic increases. In particular, the (2,2)-firm stream shows a higher failure probability because any lost packet affects the dynamic failure probability. On the other hand, the (2,4)-firm stream is tolerant of some lost packets.
The main reason for the acceptable performance results from two properties, hop-by-hop recovery and decisions using the current DBP value. First, hop-by-hop recovery can reduce the failure of passing the deadline. Like current network systems, if the reliability is guaranteed by an end-to-end approach, a long delay is too likely. Moreover, this long delay is not suitable for real-time service so a hop-by-hop approach in PSFQ is a good solution for real-time service. Secondly, the DBP value can contribute to preventing congestion by selecting the segment that should be retransmitted or ignored according to the current status. This feature makes additional control of the traffic so it can improve the dynamic failure probability compared to current traffic features.
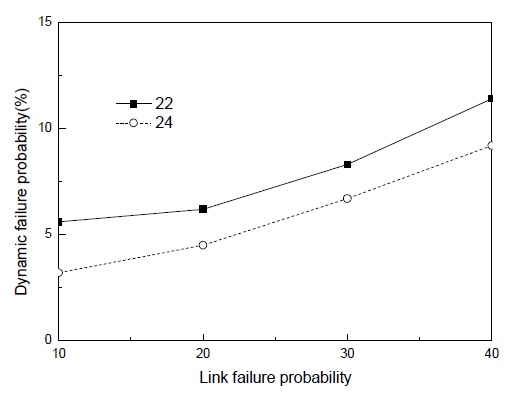
Another simulation was conducted to evaluate the performance of the proposed scheme as a function of number of link failures. In Fig. 2, the x-axis indicates the number of links in a failing state. The dynamic failure probability increases as the number of failed links increases. A failed link can hinder successful packet delivery in the middle of transmission. However, hop-by-hop recovery as well as operation with the DBP value contributes to maintaining an acceptable failure probability. If the proposed scheme were to be developed without any basis on previous work, the simulation results would be very different. However, the recovery scheme in PSFQ is very resistant to failure, and the (
In order to support real-time service in wireless sensor networks, several solutions have been proposed in the research literature. However, due to high complexity, it has not been easy to employ them in real environments. Also, there has been no consideration for an application-specific requirement. In this paper, we developed a new real-time protocol based on a scheme for reliability under the basic assumption that real-time service is greatly affected by reliability. For the application-specific model, we introduced the (
Based on basic operation and hop-by-hop recovery, we extend with the application of the (
Related to this work, the dynamic scheduling algorithm will be applied to produce better performance. Also, more studies of real-time service will be carried out through various topologies as well as adjustable parameters to determine the strengths and weaknesses of the proposed protocol.