It is difficult for students to learn from their classes based on existing education methods in knowledge-based societies in which the creation and dissipation of knowledge happen relatively quickly. The advance of information technology and the appearance of constructivist theory have gradually shifted teaching and learning from an instructor-centered paradigm to a student-centered paradigm instead [1, 2]. In particular, we have recently observed an increased interest in the cyber class, a typical example of student-centered teaching and learning in which certain temporal and spatial limitations are removed. Thus, most universities and industries are conducting and introducing cyber classes in the Republic of Korea [3].
However, the cyber class requires instructors to not only develop the curricula for classes, but also to operate the learning management systems (LMSs). Moreover, cyber classes do not currently employ effective protocols for verifying the students’ identity or against student academic misconduct because e-learning is performed online (in contrast to face-to-face learning). There are more substitute exam takers and group cheaters in cyber classes than in face-to-face classes. Therefore, it is more difficult for instructors to fairly assess students’ scholastic achievement in cyber classes. To overcome such problems, researchers have proposed blended learning [4, 5], exams consisting of randomly-ordered questions [6], and preventing substitute exam takers by employing verification techniques such as analysis of behavioral characteristics, facial recognition, and so on [7-9]. There is little research on cyber misconduct. Some studies are based on questionnaires which might not be exact or true, thereby making the results of such studies difficult to interpret.
Our study assesses the current status of misconduct taking place in the cyber classes of a real university by exploiting the IP address, the examinees’ personal information, etc., instead of relying on data from a questionnaire given to the examinee. In addition, we propose and implement an intermittent assessment system of pop-up quiz questions interspersed throughout the online study material by using Skinner’s reinforcement theory in order to prevent such cyber cheating.
>
A. General Perception of Cyber Misconduct
Education is often used as a means to attain employment; therefore, employers prefer result-oriented to process-oriented education or quantity-oriented to quality-oriented. In order to obtain good grades, most undergraduates who are trying to cheat justify substitute exam taking, cheating, and plagiarizing homework [10, 11]. Moreover, many students try to improve their academic record by repeatedly taking the same class. The cheating techniques of face-to-face learning include writing exam answers on desktops or walls, using crib sheets, and trading papers, all of which are easily caught and disciplined by proctors. Therefore, academic misconduct can be prevented by intense vigilance. The environment of cyber classes is different from that of their face-to-face counterparts. Cyber classes allow for various cheating techniques that are distinct from those used in face-to-face classes. Few strategies for reducing or preventing cheating in cyber classes have been reported in the literature.
>
B. Cyber Cheating Prevention Techniques
E-learning has many academic advantages, but it also has many disadvantages, such as requiring time, technology, and manpower to develop learning content. Moreover, e-learning does not have any proper schemes for preventing academic dishonesty and cheating because examinees are free temporary or spatially from proctors [6-8]. Several examinees can easily trade their answers; they can even congregate in the same area and solve their exam together. It is impossible to detect cyber cheaters without the examinee’s confession. The frequency of academic dishonesty and cheating in cyber classes is independent of the level of invigilation, while in the face-to-face class a higher degree of invigilation achieves less frequent academic misconduct. Thus, many researchers are still studying the prevention of cyber academic misconduct.
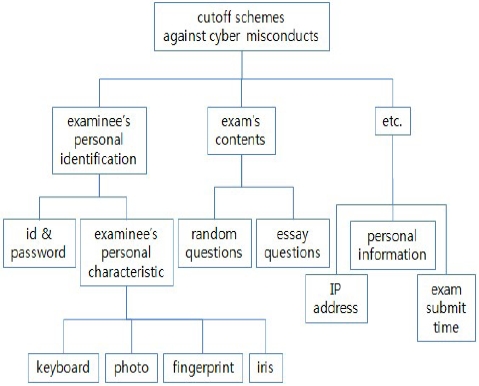
Except for blended learning, cutoff schemes against cyber cheating can generally be classified as shown in Fig. 1. The cutoff scheme of blended learning is beyond the scope of this paper because the scholastic assessment of blended learning is almost the same as that of face-to-face learning. Personal identification of examinees, random-ordered questions, and essay questions can reduce cyber misconduct, but it is difficult to detect cyber cheaters after exams.
The other approaches can detect cyber cheaters (even after exams) as well as prevent cyber cheating. The first approach, examinee personal identification, verifies whether or not the attendee is the actual examinee by using his password or his biometric/behavioral characteristics. The password cannot prevent substitute exam taking. The biometric or behavioral characteristics can prevent substitute exam taking, but they require the examinees to install additional hardware such as a webcam. The second approach based on the exam contents is that each examinee has different questions or essay questions. Different questions can be randomly chosen from an exam question bank or be set in different orders. This method can remove or reduce an examinee’s cyber cheating. However, this scheme has disadvantages, in that instructors should prepare many questions to create the question bank in advance or spend a great deal of time in scoring essay questions. The final approaches are to find traces of IP addresses, the examinee’s personal information, or submission time during or after the exam. This scheme can keep examinees from meeting together and sharing their answers, but it is difficult to discipline these cyber cheaters unless they do confess their dishonesty.
III. STATE OF ACADEMIC MISCONDUCT OF THE CYBER CLASS
The state of academic misconduct performed in cyber classes will be investigated in section III-A. Section III-B describes how the cyber cheaters in section III-A can be verified to be real cheaters and describes the distribution of possible groups of cyber cheaters.
>
A. Case Study of Cyber Cheaters
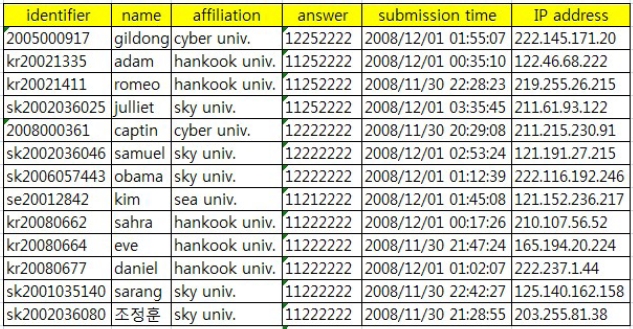
Online exams in cyber classes are similar to open book exams in face-to-face classes. An online exam is generally taken in a personal area at a given time for a given duration, thereby making fair invigilation difficult. In cyber classes, there are many forms of academic misconduct such as substitute exam taking, group cyber cheating, sharing answers by using communication media, and so on. Hence, it is almost impossible to prevent substitute exam taking because the examinee finds it inconvenient to attach additional hardware to his computer for personal identification as described in section II-B. Therefore, we focus on cyber cheating in groups or through communication media. We have chosen three cyber classes that were opened in a cyberuniversity in 2008-2009. This cyber university is a consortium of about 20 non-cyber universities. Learners are students from a non-cyber university. We collect some data such as examinees’ IP addresses, personal information, submission time, and similarity of incorrect answers, as is shown in Fig. 2. Hence, the first three columns (identifier, name, and affiliation) are not real because of privacy concerns. Moreover, the fourth column consists of a series of concatenated answers for multiple choice or true/false questions.
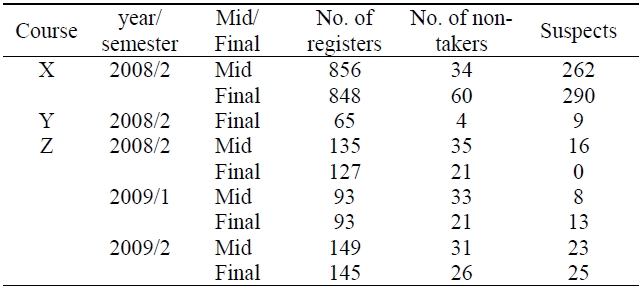
It is more difficult or almost impossible to investigate statistics for academic misconduct in cyber classes compared to offline classes. A cyber class has more kinds of academic cheating methods than offline classes. In a cyber-class, it is possible for an examinee to try to cheat more actively or positively because the examinee and proctor are not at the same place. However, we can easily identify a suspected group cheaters because they use similar IP addresses, attend the same university, and submit their papers at similar times. Cheaters who share their answers through communication cannot easily be detected because only their affiliations and incorrect answers are similar. Thus, it is difficult to catch this kind of cheater without their confessions. For now, we investigate the states of the former (group cheaters). Table 1 shows the status of cyber cheating. It is composed of 3 courses that have 9 exams. We use the following criteria for group cyber cheating: 1) the same C-class IP addresses, 2) the same university and the same entrance year of examinees’ identifiers, and 3) ranges between submission times are within 10 minutes.
[Table 1.] Status of cyber cheating
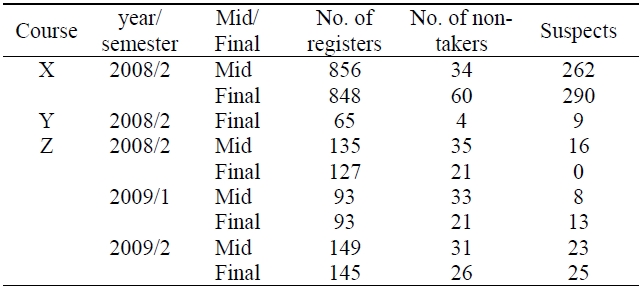
Status of cyber cheating
If the above conditions are all met, then we consider an examinee as a suspected cheater. Table 1 indicates no suspects in the final exam of course Z in the second semester of 2008. This is because we detected cheaters and put several warning notices on the class bulletin after the mid-exam. Thus, to obtain meaningful statistics, we remove the result of the final exam of course Z in the second semester of 2008. Table 1 shows that among 2,384 registered students, 244 students did not take exams and 646 students are suspected cheaters. Thus, the number of total examinees is 2,140. About 30.2% of examinees per course are assumed to try dishonesty on taking the exam. This ratio is too high to be acceptable. About 34.3% (for X), 14.8% (for Y), and 9.3% (for Z) of the examinees are assumed to be group cheaters, respectively. Examinees who take course X have the highest ratio of cyber cheating. One reason is that the exam of course X consists of multiple choice or true/false questions that are adapted for large-scale classes owing to easy scoring. Another reason is that courses Y and Z use a question bank and random questions with a tight exam time, while course Z does not.
>
B. Verification of Cyber Cheating in the Case Study
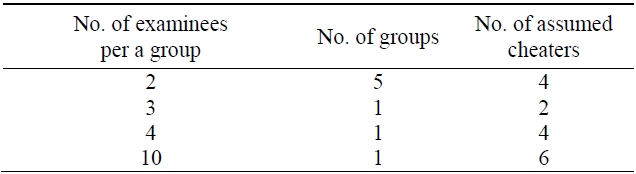
To investigate whether or not the suspected cheaters shown in Table 1 are actual cheaters, we have chosen course Z from three courses, a mid-scaled class. First, to verify group cheating, we check the three criteria in section III-A - IP addresses, personal information, and submission time - for assumed cheaters. Table 2 shows that there are four kinds of groups that use the same C-class IP addresses. Even though eleven examinees are in the same IP-addressed group, we exclude them from the suspected cheaters because they do not have common personal information and submit their papers at different times.
[Table 2.] Distribution of possible group cyber cheaters
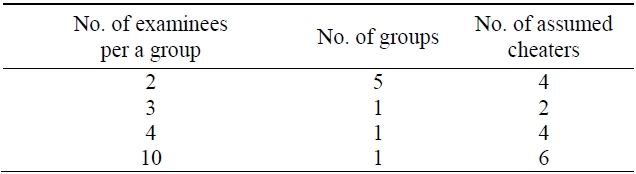
Distribution of possible group cyber cheaters
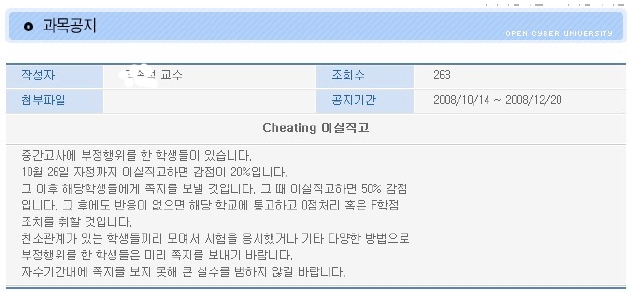
To distinguish actual cheaters from suspects, we made two announcements about dishonesty after the midterm exam. We sent suspects a warning message shown in Fig. 3 and even phoned them, too. The warning message tells them that they are group cheaters, some points will be deducted for their grades if they confess their misconduct, and they will fail the course otherwise.
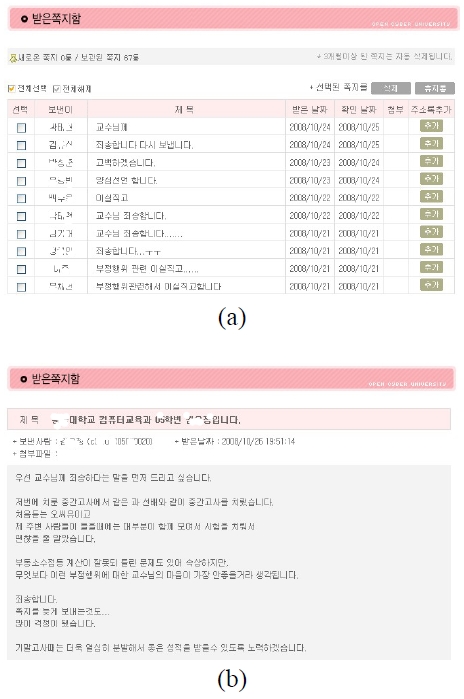
As a result, all of the assumed group cheaters (16 examinees) sent response notes back that they admitted their dishonesty and asked to be excused. Luckily, there were no suspects who claim to be innocent. Fig. 4a shows a received message box that the cheaters sent, and Fig. 4b shows one of the cheaters’ messages. According to our expectation, there were no cheaters on the final exam of the same course as shown in Table 1.Therefore, it is not too much to say that all assumed cheaters in Table 1 must have been actual cheaters who met in the same computer laboratory at the same time, solved their questions together, and shared their answers.
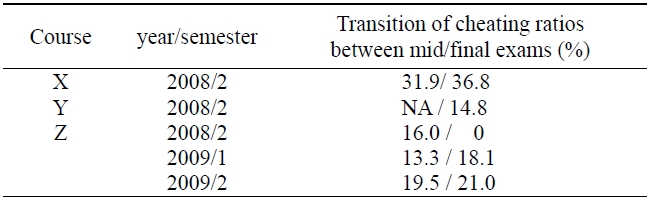
Table 3 shows the transition rates of cyber cheating between the midterm exam and final. We excluded course Y because it does not have a midterm exam. We also excluded a course Z from the second semester in 2008 because there were no cheaters on the final exam. In general, the cheating ratio of the final exam is higher than that of the midterm exam. As the final exam approaches, it is natural that learners become more concerned about their grades than when the midterm does.
[Table 3.] Ratio of group cyber cheaters
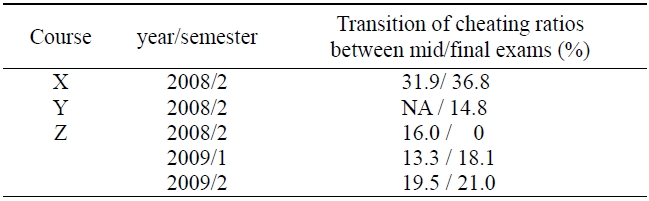
Ratio of group cyber cheaters
To investigate the status of sharing or trading examinees’ answers through communication media such as e-mail and cell phones, we analyzed some of the same data that was used in section III-A. We excluded 16 cheaters and 35 non-takers from 135 registered students. We asked 10 examinees among 84 exam-takers by a phone call whether or not they were involved in cheating, but we could not force them to respond. Moreover, there were no confessions, and they even complained about being suspected for no reason. Therefore, it is almost impossible to investigate this kind of cheating without the examinees’ confessions.
IV. INTERMITTENT ASSEMENT SYSTEM THAT MINIMIZES ACADEMIC MISCONDUCT
Cyber classes have a high possibility of group cyber cheating due to their characteristics. The proctor cannot see how examinees take the exam because they are in different locations. Thus, the results of scholastic achievement in a cyber-class are not accurate. If the instructor gives learners their credits or grades in cyber classes by using mainly midterm and final exams, he will confronted with various types of cyber cheating and cannot assess the learners’ acquired knowledge. Therefore, we propose and implement an assessment system that is applied by Skinner’s reinforcement theory, and thus eliminate or reduce group cyber cheating. Reinforcement is the overall condition that delivers a stimulus after a response that results in an increase in future rates [12]. In particular, intermittent reinforcement makes learners study better [13]. There are several LMSs that apply this reinforcement theory [14, 15]. However, they are trivial systems with simple quizzes. Therefore, this study applies intermittent reinforcement into scholastic assessment without mid/final exams on the basis of the results of the cyber cheating analysis in section III-B. That is, we randomly select some questions from a question bank. Learners can experience questions on random pages of their learning content. No learners can predict on what page questions will pop up. Thus, learners have no choice but to take the exam within a given time while studying. They cannot earn their grades without studying because they do not have any exams other than the popup exams.
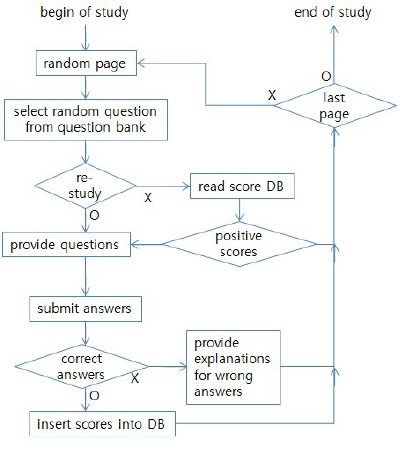
The assessment system proposed in this research causes the learner to experience intermittently random questions that unexpectedly pop up on random pages. Fig. 5 shows the flow of our assessment system. The assessment system stores the learner’s answers in the score database, and it provides the learner some explanation if his answer is wrong. Our system does not pop up questions that he has already solved if he studies the same material repeatedly.
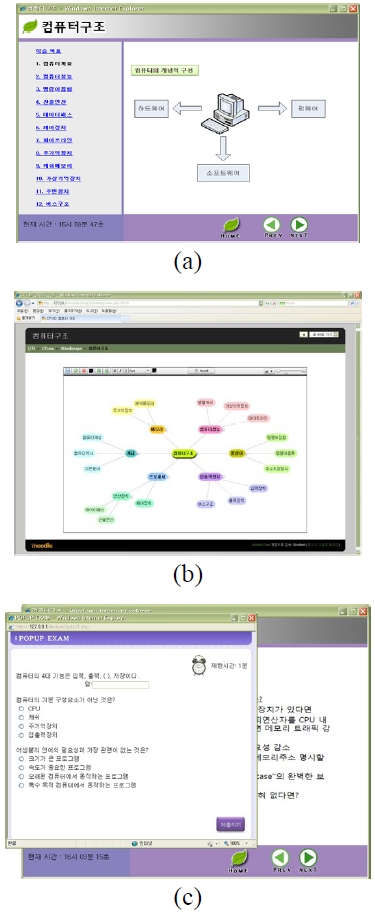
We implement our assessment system in Windows XP and an Apache web server by using MySQL, personal hypertext preprocessor (PHP), and JavaScript. In addition, we exploit Moodle [16], open source and free software, as our LMS. Fig. 6a shows an example course page in our LMS, Fig. 6b provides a mind map of an overall structural abstract of a given course’s contents, and finally Fig. 6c shows a random question window that popped up on a random page during studying.
Instructors still hesitate to use e-learning in spite of its advantages. One of the main reasons is that online exams are easily exposed to academic misconduct. Thus, this study investigates the nature of academic cheating in online classes in a non-cyber university by identifying the IP addresses and personal information of examinees and the submission time of exam-answers. Moreover, we confirmed through IP addresses and other indicators that suspected cheaters were actual cheaters based on their confessions. Finally, we implemented our assessment system for e-Learning in order to root out or reduce cyber cheating by applying Skinner’s reinforcement theory.
Future work must include the trends in scholastic achievement according to whether or not our assessment system is used in cyber classes and the status of cyber cheating through communication media and its prevention.