At the 2012 Seville International Conference on Future-oriented Technology Analysis (FTA), FTA was regarded as a method to better prepare for the future and/or shape it in order to achieve a favorable outcome. This study attempts to broaden the FTA to identify future skills needs, which constitutes a critical subject for education and training. It is noted that there is still no research on the future skills needs linked to FTA, including patent analysis.
In the study of future skills needs, the crucial issue is how to proceed to identify future skills needs. On that matter, this study argues that some information derived from patent data can be used in the identification of future skills needs as a measurement of future technological trends.
As for forecasting and/or anticipating future skills, conventional studies analyze or 'interpret' changes of skills needs already occurring. By contrast, this study attempts to search for future skills needs directly derived from technological innovation. Conventional skills analysis focuses on labor market information. This information is useful for the analysis of the present and near future, but it has limitation on the analysis of newly emerging technology beyond information (CEDFOP, 2012; Lowery et al., 2008; Schmidt et al., 2004). This is a common limitation because conventional forecasting of workforce demand and supply is mainly focused on quantitative demand changes by industry and occupation.
The analysis of future skills needs that is required should contain tangible contents of skills needed; this analysis can be called a qualitative forecast, which is different from existing quantitative forecast on workforce demand and supply (Hwang, Coh and Lee, 2011; Hwang, Joo and Coh, 2011; Hwang and Lee, 2010). This qualitative supplement to a quantitative study can normally be altered through expert panel discussions, but it faces several challenges from the shortage of verification instruments. So, this study attempts to conduct a verifiable qualitative analysis on the specific and measurable basis of patent information. However, such analysis might be regarded as another quantitative approach or, despite the use of patent data, it might simply be called a limited quantitative approach in the interpretation and linkage carried out by experts on job and curriculum analysis.
Section 2 reviews the feasibility of analysis of future skills needs through patent data at theoretical level. It discusses a knowledge base and a knowledge network along with the possibility of examining future skills needs through patent data, and suggests a forecast methodology of future skills needs.
Section 3 proposes analytical statements on issues related to initial skills needs derived from the examination of current jobs in information security occupations. It links International Patent Classification (IPC) of information security technology to the skills needs.
Section 4 analyzes trends in the timescale of IPC on information security technology, carries out forecasting on skills needs, and verifies the appropriateness of actual forecast skills needs. In conclusion, the study discusses the achievements, limitations and future research directions of investigating future skills needs through patent data.
II . In Using Patent Data to Detect Future Skills Needs
In this study, skills include technology and dexterity, and thus can be considered an interchangeable concept with knowledge. Knowledge in this context focuses on knowledge as competence and acquaintance rather than propositional knowledge. On top of knowledge as competence and acquaintance, there are transcendent knowledge and logical knowledge that are closely related to propositional knowledge. As regards epistemology, knowledge can be classified into three categories (Balconi et al., 2007): Firstly, knowledge means an ability to do something (knowledge as competence) ranging from simple behaviors to complex cognitive behaviors, i.e. from use of simple hammers to use of complex languages. Secondly, knowledge is a familiar behavior of getting to know someone or something through past experiences (knowledge as acquaintance), like remembering the faces of frequently encountering people. Thirdly, propositional knowledge is recognition of the necessity of modifying certain information at hand. This is an inherent nature of mankind as an advanced species.
Knowledge as competence and knowledge as acquaintance are discussed by Gibbons et al. (1994), who analyze, in a useful fashion, the changes in knowledge production methods with a focus on modern science and technology. Gibbons et al. examine the transition of knowledge production method, naming knowledge production in a traditional method as Mode 1 knowledge and knowledge production in a new method that transformed traditional knowledge production as Mode 2 knowledge. While Mode 1 indicates knowledge forming that occurs within the boundary of certain disciplines, Mode 2 indicates knowledge forming that occurs through inter-discipline or trans-discipline. Nowotny et al. (2003) regard Mode 1 knowledge forming as a further development of existing science and technology measured on an academic standard, while they regard Mode 2 knowledge forming as a new paradigm of knowledge creation.
In the midst of rapid technological progress, Mode 2-type knowledge is also expanding (Cowan et al., 2000). Simple restructuring of existing knowledge is not sufficient, and it requires continuous knowledge creation. This kind of knowledge creation enhances knowledge convergence. In other words, the key to knowledge creation lies in the active participation in a continuous process of converging knowledge. In this context, simply absorbing convergent knowledge as a response has its limitation.
2. Usage of Patent as a Tool of FTA
For a while, patent data have been regarded as one of the most important sources or tools for FTA. With free accessibility in most countries, patent data provides valuable information on technological development and allows the analysis of emerging technologies, for instance, text mining in Yoon et al. (2004), Tseng et al. (2007) and An et al. (2011) and pattern recognition in Cong et al. (2010).
After reviewing several technology forecasting methodologies and models, Daim et al. (2006) propose the integration of multiple methodologies for forecasting in the areas of fuel cell, food safety and optical storage – integrating patent analysis and bibliometrics consisting of System Dynamics, Scenarios and Growth Curves. They insist on the need to develop such integrated tools for technology forecasting. Furthermore, Daim et al. (2006) suggest the inclusion of a Delphi methodology involving experts in FTA. Previously, after compiling several methods of analysis on future technology and considering recent changes in science and technology, including information technology, Porter et al. (2004) address several challenges related to the feasibilities and (current) limitations of FTA, and they offer steps for further advances.
Cagnin et al. (2013) insist that an appropriate combination of quantitative and qualitative methods should be made for specific purpose and context. It should enable confidence building through inclusiveness and transparency in all processes linked to rigorous methods. They warn that there is no uniform and proven FTA methodology, and that applying relevant methods in a rigorous manner is more important than assembling a set of highly sophisticated methods.
Even though combining quantitative and qualitative approaches is needed to bring about a better understanding of societal challenges and complex interrelated systems, Haegeman et al. (2013) explore aspects which ought to be considered in future analysis such as epistemological differences, cultural differences and conceptual differences.
3. Patent Analysis and Knowledge
Saviotti (2004, 2007) argues that knowledge has two different attributes in knowledge creation and utilization: (Proposition 1) knowledge has a co-relational structure; (Proposition 2) knowledge has a retrievable/interpretative structure. These attributes of knowledge can construct a (knowledge) network (Saviotti, 2009, 25-26). The ‘advent of new technology' and more recent 'convergence of knowledge' can be analyzed as this type of knowledge network.
Patent data could be used for examining this knowledge network. Due to skills resulting from a technological innovation, the examination of patent data - itself a product of technological innovation - could provide keys to the analysis of future skills needs. The structure of data embedded in patents could play a critical role as a “proxy meter” in understanding the structures of R&D activities and related knowledge. Quantifying and structuring patent data make it possible to understand the development and structure of knowledge.
4. Methodological Scheme in This Study
This study has selected the sector of information security that has witnessed considerable technological advances in recent years. It is also relatively well organized as to the skills needs identified through an analysis of jobs at a particular point in time, following a pilot.
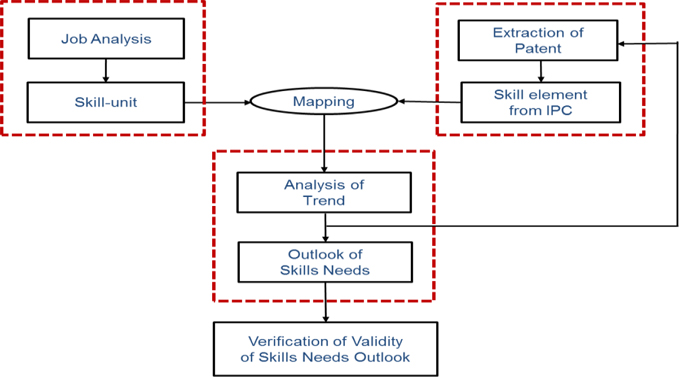
This study is configured in five large schemes: (1) extraction of skill units based on job analysis; (2) extraction of skill elements based on patent analysis; (3) matching IPC skill elements with skill units from job analysis
Correcting a search formula recursively via IPC analysis carried out the identification of patent, and the final search formula was determined through skills analysis. From the initial formula setting, security professionals provided consultation in a repetitive corrective process. A total of 174,155 patents were finally identified.
The identification of skills unit from jobs was carried out through a meta-analysis of related domestic and international job configurations. Especially, a substantial level of support was secured from US job data.
The mapping and matching of skill elements from IPC code with skills units from existing job studies is conducted in collaboration with information security professionals. The mapping is key to analyze skills trend from a patent trend.
Future skills needs for information security is drawn from an exploratory analysis of the timeline trend of the skills elements based on patent data. Continuous consultation with professionals on the results of the analysis helped distinguish the broad case from a narrow case of connection between IPC code and skills units in the sector of information security
Upon observing the apparent gap between forecast results and actual results, a better methodology could be developed by raising the validity of actual data. To test the degree of attributing the entire forecast results, including consistent forecast results, to the validity of actual situations, surveys of experts and companies were carried out.
III. Job Analysis and Patent in Information Security
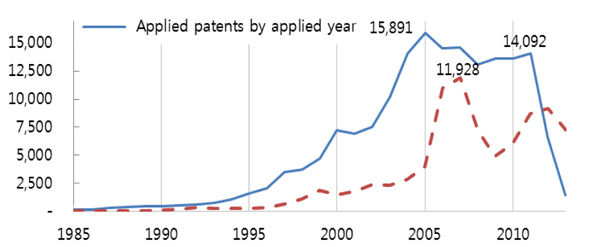
The field of ICT, which has recently experienced significant technological advances and represents relatively well-organized necessary skills needs identified through an analysis of actual jobs, was selected through a pre-analysis. This helped select subjects and method application to develop a methodology. The consistently rapid technological advances in the ICT sector since the 1990s was confirmed by annual trends in the number of registered patents in the U.S. Patent and Trademark Office.
The pre-analysis has also gone through expert consultation to check the validity of identifying technological advances in ICT from patent data. Furthermore, due to the relative clarity of job description, the ICT technology sector was deemed suitable for the analysis of current skills needs. It was recognized that this sector, through an analysis of patent, allows for a relatively easy comparison of forecasting demands for significantly advanced ICT skills. On this basis, the focus on the sector of information security was finalized.
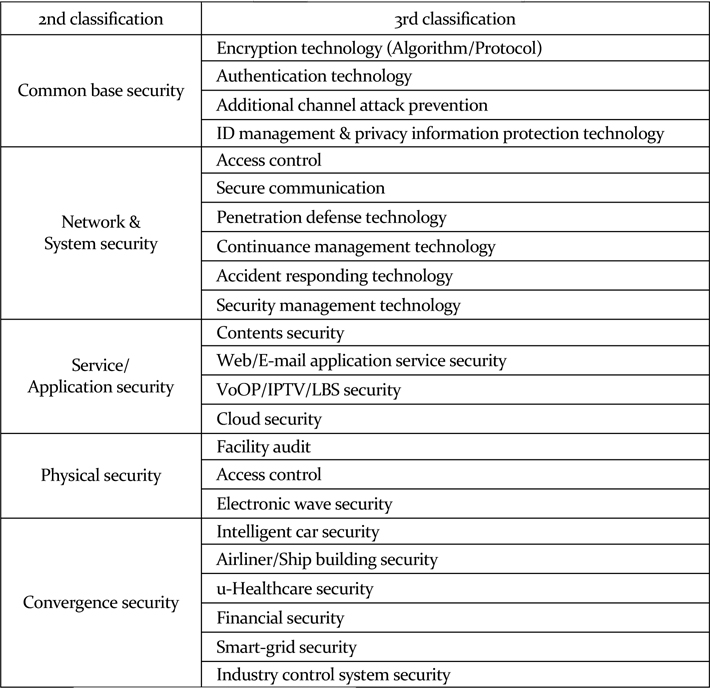
On Table 1, the physical security element is to be excluded from information security in this research because it goes beyond the brief of the study. Since both the application service security and the convergence security can be regarded as instrumental in information security, the study defines the range of information security by focusing on network and system security, including common base security. The technology of common base security was not analyzed separately, but examined as a component in the analysis of the network and system security.
[Table 1] Knowledge information security
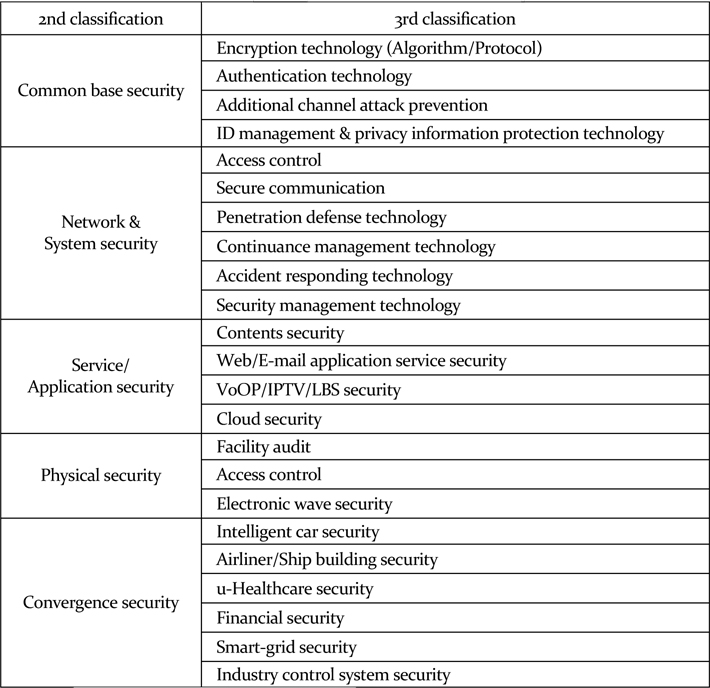
Knowledge information security
2. Skill Unit from Job Analysis
Before examining job configuration and skills needs for information security, the current and prospective status of human resources was considered by tapping into existing researches. The information for the analysis of job configuration and knowledge requirement was gathered through expert advice and material data from inside and outside of the country (Simpson et al., 2006; Yoo and Kim, 2009). After reviewing the knowledge requirement for the information protection and education certification program in the United States, relevant research material was collected to carry out the analysis of the information security job in Korea. As a final step, expert opinions were sought to identify the skills needs for information security jobs.
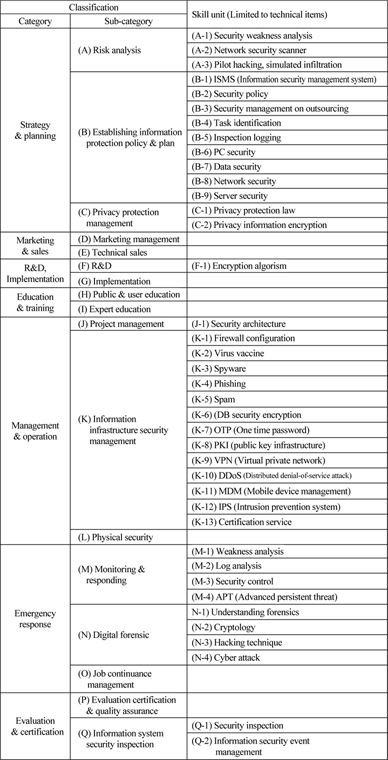
The result of identifying skills through a review of the nature of the jobs is presented in Table 2 as necessary skills corresponding to the sub-classification of job category. Patents are analyzed in response to these required skills.
[Table 2] Job configuration & required skills for information security sector
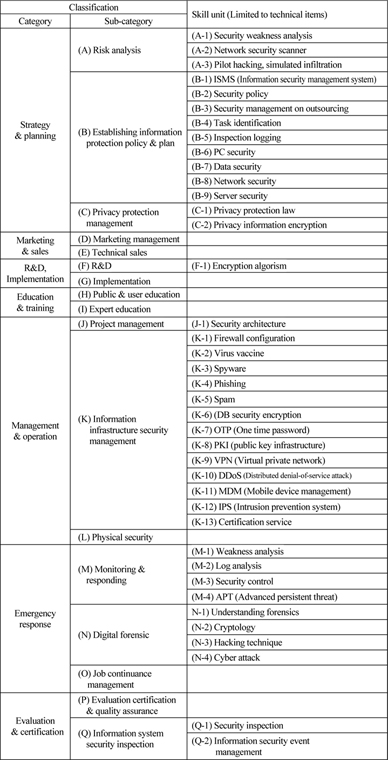
Job configuration & required skills for information security sector
3. Extraction of Patent Information
The basic element for analyzing a patent is an examination of patent application to Korean Intellectual Property Office each year. This data was extracted from KIPRIS DB (http://kpat.kipris.or.kr/). In fashioning a search formula, the first step involved a basic search using IPC. In the second step, the IPC code was re-extracted (7-digit level) from the search results obtained in the first step. In the third step, a keyword search was carried out of the patent summary. After running the entire analysis process based on the third search formula, all the previous analyses were run again by modifying the search formula. The search results on information security patent eventually covered 174,155 patents filed as of September 30, 2013.
4. Mapping Skill Element to Skill Unit from Job Analysis
In matching IPC-extracted patents with required skills, the skills that could not be comprised within IPC were excluded, and the IPC that does not include information security was also disregarded. Meanwhile, matching multiple IPCs with one skill unit was allowed as well as matching one IPC with several skill units, with regard to IPC as a skill element.
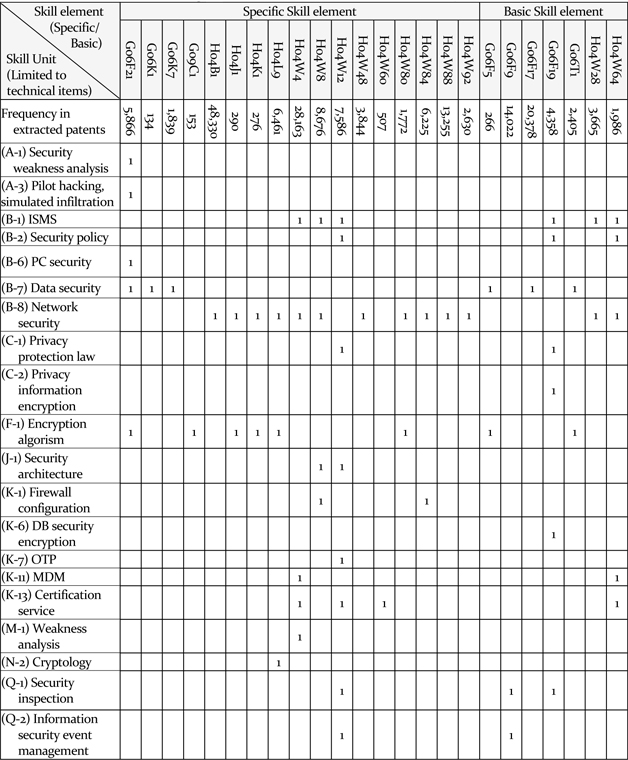
The matching results were obtained through consultation with experts. On the Table 3, H04W008 Network data management
[Table 3] Mapping skill element from IPC to skill unit from job analysis
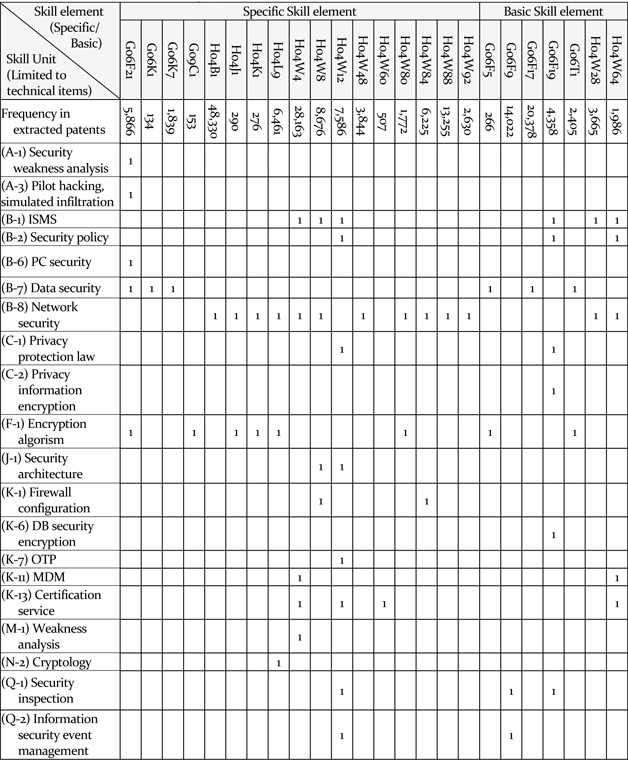
Mapping skill element from IPC to skill unit from job analysis
IV. Forecasting the Skills Needs from Patent Analysis
1. Trend of Expected Skills Needs from Patent Trend
Given a particular skill
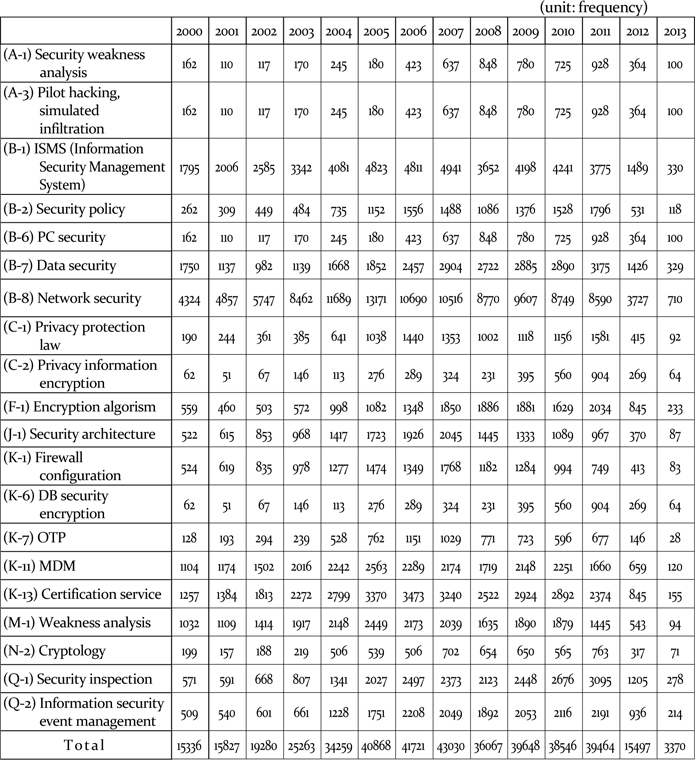
[Table 4] Trend of skills needs from absolute size of IPC
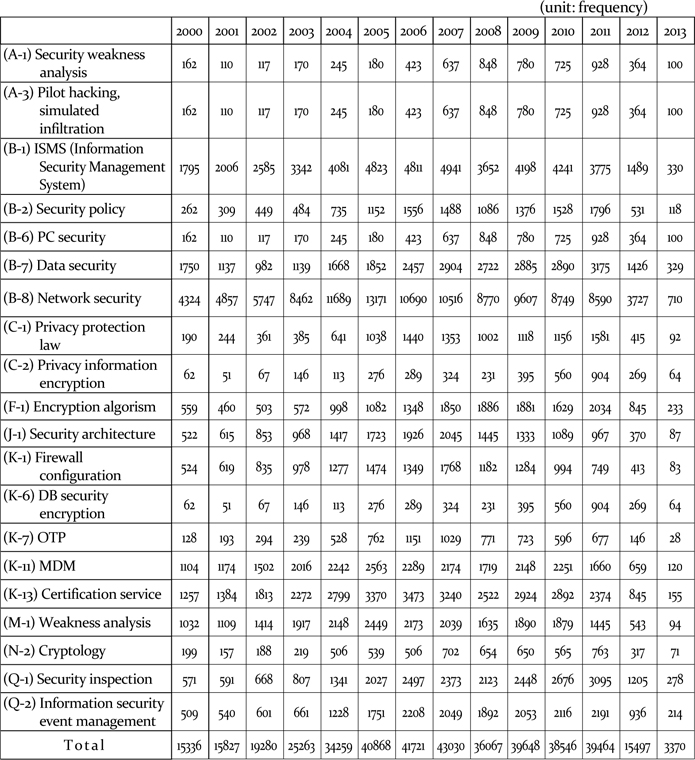
Trend of skills needs from absolute size of IPC
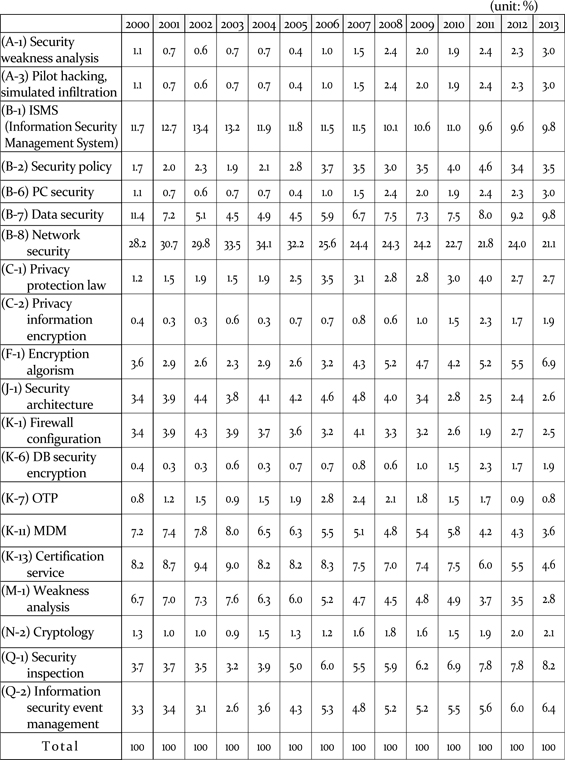
[Table 5] Trend of skills needs from relative size of IPC
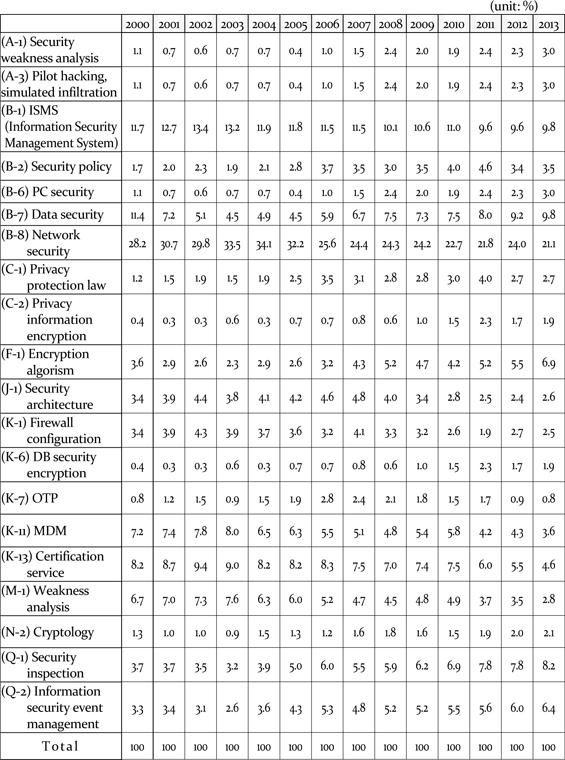
Trend of skills needs from relative size of IPC
2. Forecasting and Verification of Skills Needs
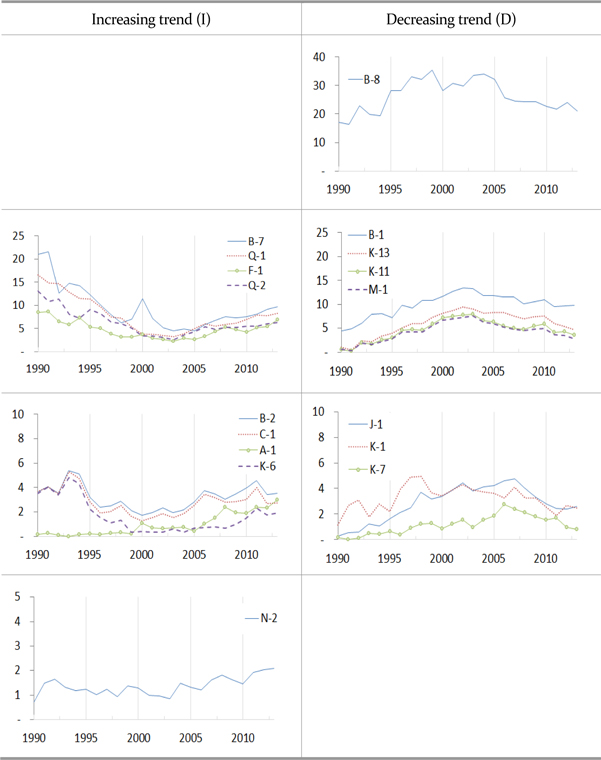
Based on the timeline trend, mainly since 2005, two categories are examined as increasing and decreasing trends, on Figure 3. In the findings, the distinction between specific skill elements only and the inclusion of basic skill elements was made. Furthermore, the distinction between the whole pattern of patent application and top 20 patent-applied companies only was also made. After conducting 2×2 analyses with overall similar results in terms of trends, Table 6 shows the whole pattern of patent applications with specific skill elements only.
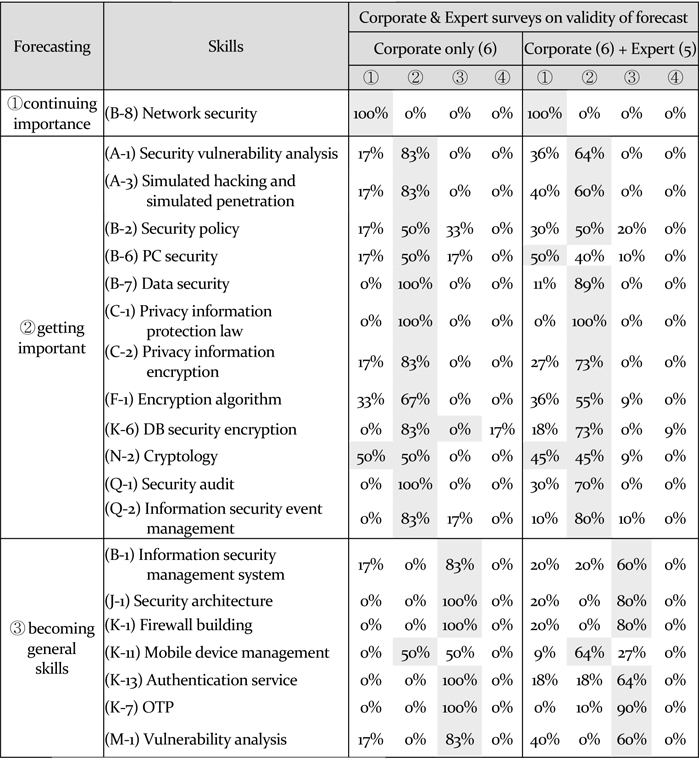
[Table 6] Survey for the validity of skills needs forecast
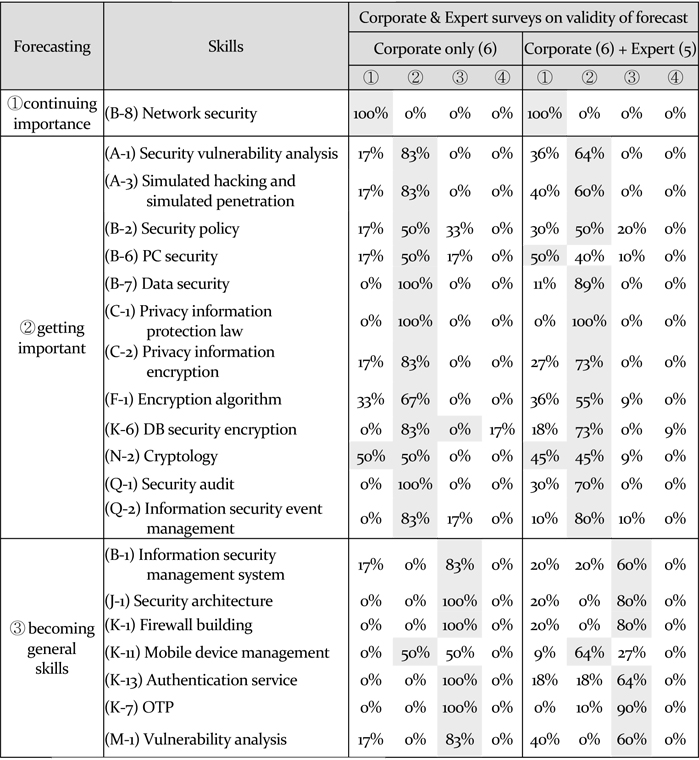
Survey for the validity of skills needs forecast
Regardless of the differences of treatment in the patent analysis, ① (B8) ‘Network security’ appears to be the skill that continues to hold a great deal of importance, while ② (F1) ‘Encryption algorithm,’ (B7) ‘Data security,’ (N-2) ‘Cryptology,’ (A-1) ‘Security vulnerability analysis,’ (A-3) ‘Simulated hacking and simulated penetration’ and (B-6) ‘PC Security’ were presented as newly-emerging skills. In addition, ③ (B1) ‘Information security management system,’ (K13) ‘Authentication service,’ (K -11) ‘Mobile device management,’ (M1) ‘Vulnerability analysis,’ (J-1) ‘Security architecture,’ (K-1) ‘Firewall building’ and (K-7) ‘OTP’ were presented as skills being incorporated into basic skills with receding independence compared to the past. Based on the forecast that includes general-purpose technology IPC, (B-2) ‘Security policy,’ (Q-1) ‘Security audit’ and (Q-2) ‘Information security event management’ are also expected to be newly emerging skills.
To verify the validity of the reality of these forecast results, a survey of information security companies and of relevant experts was conducted. Table 5 presents these findings as well as the forecast results that include a general-purpose technology IPC. The survey results were generally similar, with the exception of a high frequency for (B-6) ‘PC security' in ② ‘newly emerging skills’ in the category of ‘manufacturer only,’ and ① ‘skills that continue to hold importance’ in the category of ‘expert group.’ These results can be interpreted as supporting the findings of the skills needs forecast carried out by examining the entire patent filings, including general-purpose technology IPC (Fisher’s Exact-Test is significant, with the significant level of 5%).
This study attempts to develop a methodology that analyzes patent applications to identify future skills, in particular in the sector of information security, recently in the spotlight. Matching skill elements from IPC with skill units from job analysis, the study tries to track trends of the skills needs based on IPC time-pattern. It then verifies the validity of the outlook for future skills needs by addressing the situation through the use of patents. The research assesses the usability of patent information by showing how it can be utilized in the analysis on future skills needs.
The skills needs identified from the patent information in late 2000s in the information security sector substantially mirror the skills needs identified in 2013. However, the accuracy of matching the skills needs forecast in different fields or timeline with the actual skills needs is not guaranteed. Furthermore, differences in the speed and pattern of technological advances are revealed owing to differences in technological characteristics and differences in various socio-economic environments within which technologies are implemented. The most important issue in this study is ‘Matching required skills with jobs within IPC', but it is worth noting that more specific and detailed methods beyond the current one utilizing the 0-1 matrix would be required.
Despite its limitations, this current study might be worth refining the methodology to identify future skills needs by using patent information, because there is still no research in this specific area. While this study is limited to the sector of information security by using Korean patent information, it can be expanded in the future to other areas and patents in the United States and Europe. Technological change is a global phenomenon, so the analysis of global patent information ought to be a valuable contribution.