NETWORK APPROACH TO MIDDLE POWER DIPLOMACY
Network theories provide IR theorists with an alternative account of middle power diplomacy; they hold that a particular type of network creates favorable conditions for participating actors and how actors are positioned in the network facilitates by their ability to compete or cooperate with others (Goddard 2009). In this view, middle power’s actions are dependent upon the structural condition of the network in which a country ties to others. In other words, depending on how the structure is shaped, middle powers are likely to enjoy certain roles by degree. Comparing to other theoretical approaches, how then does the network perspective define the structural condition—i.e., “structure” in general?
While the neo-realists notion of “structure” is as an entity that is derived from the categorical attributes of actors (Waltz 1979), network theories look at the relational context of actors’ interaction. Structure is emerging from “continuing series of transactions to which participants attach shared understandings, memories, forecasts, rights, and obligation” (Tilly 1998, 456; Goddard 2009, 254). Here, structure is understood as the relational configuration among actors or the patterns of transactions themselves. Relatively durable, but fundamentally dynamic interactions constitute the structural conditions in which actors operate (Nexon 2009). In short, structure is not a kind of fixed entity reducing to actors’ internal properties or attributes, but a social relationship among or across actors (Nexon and Wright 2007).
This view is useful to identify the role of a middle power occupying a specific position in the network. It is not actor’s attributes or interests but its positions that enable a middle power’s agency. The positional perspective in social network theory holds “that how actors are positioned in a network facilitates their ability to act as entrepreneurs. Because social and cultural ties provide power, information, and ideas, an actor’s ability to introduce new norms, manipulate symbols, and radically influence political outcomes, all depends on network position” (Goddard 2009, 257). Middle powers’ strategies are more likely to succeed if they accommodate the requirements of the structural conditions in the network. If the concept of middle power is defined in terms of structural position in a network, what specific roles would a middle power play under a certain network structure?
Among various roles of middle powers, this study pays special attention to the advantages of brokerage empowered by positioning within a strategically important spot in a particular network structure. According to Ronald Burt, people who hold brokerage positions enjoy a competitive advantage over others who are less well placed. When they capture strategic places that connect otherwise disconnected groups, those people can exercise a special kind of power. In particular, Burt gives us some analytic insight: the unique forms of cleavages, which usually are conceptualized as “structural holes,” are found in a network which provide structural opportunities for some actors—known as brokers. By bridging the structural holes, brokers occupy central positions in a network structure, acting as nodes through which multiple transactions coalesce (Burt 1992).
It is this structural position, not an actor’s attribute, that enables middle powers to exercise a certain kind of power. The structural conditions of a network— e.g., number of nodes, pattern of links, and architecture of the whole network— enable or disable middle powers to play particular roles and thus to have more possibilities to exercise powers. In this sense, the power of broker—i.e., brokerage power—could be called “positional power” (Gould and Fernandez 1989; Chang 2009). Positional power is contrasted to the existing notion of “resource power,” which refers to the power based on resources held by actors. In this respect, positional power is one aspect of recent theoretical attempts concerning “network power” that derives from one’s relationships with others (i.e., networks) rather than its attributes (Grewal 2008; Castells 2009; Hafner-Burton, Kahler and Montgomery 2009; Ha and Kim 2010; Kim 2014b).
In wielding the positional power, the pre-stage of the game is to identify the nature of network committed, and to contextualize a middle power’s position within the network structure of the whole system. In other words, a major task here is to comprehend the overall configuration of the network, and define the coordinating or conflicting interests of the actors who are engaging the network game. For a middle power, a central task at this stage is to read the context of which world powers set the scheme. Only after reading the context can a middle power assign itself roles within the network. Those roles could be articulated by understanding three aspects of network strategies: brokerage, collection, and complement.
First, situated at the interstices of networks, a middle power is likely to play the role of brokerage. Brokerage may alter network structures, leaving actors with a fundamentally different set of network ties, and changing the agenda in a network. This occurs because the brokerage process is usually accompanied by the process of “asymmetric coordination of relationships.” This is to make certain ties stronger and to sever others. Simply, a process of network diplomacy is to break existing ties on the one hand, and to build new relationships on the other hand. It is this process of integrating and destroying ties that lies at the heart of brokerage. Indeed, this process belongs to the realm of strategic choices at the risk of opportunities costs.
Second, the enriched pool of supporters in the network enables middle powers to play active brokerage roles. In fact, a large portion of a middle power’s brokerage roles comes from its ability to bring more actors than others do. Being aware of the limitations of their brokerage roles, middle powers have to rely on collecting and attracting as many like-minded countries as possible. This carries with it the basic ideas of network power—i.e., “social power” (Hafner-Burton, Kahler and Montgomery 2009; Kahler 2009) or “collective power” (Kim 2014a). The patterns of power remind us of online collaboration, conceptualized as “collective intelligence” (Levy 1999). In particular, middle powers seek to exercise the collective power through coalitions or alliances.
Finally, middle powers may exercise a “programming power” as new architects of the network program. However, a middle power’s programming power is concerned with the ability to complement and possibly further renovate the whole system, designed by world powers. Indeed, its unique position in the existing system requires a middle power to play a complementary role to the existing world order, not to play an exploitive role through challenging world powers’ initiatives. In this sense, middle powers do not necessarily have to be a whole-system designer; it is sufficient for a middle power to be a complementary programmer, who can provide system adjustments and adaptations that increase interoperability and compatibility, and further reinforce normative values and legitimation.
Theoretical notions introduced in this section are useful to understand the structural conditions of the cyber security sector and South Korea’s middle power strategies under the unique structural conditions. In recent years, South Korea as an Internet power is likely to play diplomatic roles in easing cyber conflict between world powers, and to building a new global mechanism for cyber security governance. To achieve these tasks of middle power diplomacy in this sector, it is essential that South Korea properly identify the structural conditions in which it currently operates, and determine adoptable options for the future to aid in its success.
1Concerning the literature on cyber security and International Relations, see Eriksson and Giacomello (2007), Cavelty (2007), Kramer et al. (2009), Manjikian (2010), Klimburg (2011), and Choucri (2012). Currently, various theoretical perspectives are being applied to cyber security issues. For the strategic approaches to the so-called NetWar, see Arquilla and Ronfeldt (1996; 2001) and Libicki (2009). For the liberal view on cyber security, See Nye (2010) and Rattray and Healey (2011). Schimit (2012) applies the traditional framework of international law and the laws of war; Morgan (2010), Lupovici (2011), Singer and Shachtman (2011), Nye (2011), and Lawson (2012) adopt or criticize the Cold-War metaphor, for example, the notion of “nuclear deterrence” to the cyber security sector; Deibert et al. (2002; 2008; 2010; 2011; 2013) constructivist view on cyber security; and Steinberg and McDowell (2003)’s spatial constructivist view is also useful. For a network perspective on theorizing cyber security issues, see chapter 11 in Kim (2014b) and Kim (2014c). 2For existing studies on middle power diplomacy in traditional views, see Gordon (1966), McLin (1967), Holbraad (1971), Pratt ed. (1990), Cooper, Higgot and Nossal (1993), Cooper, Higgot and Nossal (1993), Otte (2000), and Gilley and O’Neil eds. (2014). 3This paper does not provide a comprehensive literature review of network theories. While the discussion of this paper mainly relies on theoretical assets of social network theory, network theory is not a single theory. There are different variants from “social network theory” to “network organization theory” and “actor-network theory (ANT).” For an overview of network theories in IR perspective, applied to the Korean context, see Kim (2014b, esp. ch.1). For the network perspective of world politics, see Hafner-Burton and Montgomery (2006), Goddard (2009), Nexon and Wright (2007), Nexon (2009), Ha and Kim eds. (2010), Kim (2014a; 2014b).
GLOBAL GOVERNANCE IN CYBER SECURITY
Over the last decade, the world has been exploring a new order for cyber security, which will be established in due consideration of the complexity of the domain. Since the late-1990s, cyber security issues have been handled as a subfield in Internet governance rather than a
>
MULTISTAKEHOLDERISM VS. INTER-GOVERNMENTALISM
In its early days, Internet governance was conducted by a decentralized multistakeholder network of interconnected autonomous groups drawn from civil society, the private sector, governments, academic and research communities, and national and international organizations. This multistakeholder governance model, sometimes known as a multistakeholder initiative (MSI) or multistakeholderism, is a governance structure that seeks to bring stakeholders together to participate in the dialogue, decision making, and implementation of solutions to common problems and/or goals. The global framework of Internet governance has also been constituted by the initiative of those multistakeholders whose activities are mainly based on the United States, and not by the consensus of government representatives in the diplomatic arena of international organizations.
A remarkable example of the multistakeholder model is found in the Internet Corporation for Assigned Names and Numbers (ICANN), which is a non-state organization headquartered in California, USA. Since the early years of the Internet, ICANN has overseen the assignment of globally unique identifiers on the Internet. ICANN must be a global governance model of private-public partnership since it has been governed by an international board of directors drawn from across the Internet’s technical, business, academic, and other noncommercial communities. However, in the sense that the U.S. Department of Commerce continues to have final approval over changes to core issues, the ICANN model has been suspected as a tool of U.S.
Against the ICANN model, Russia, China and other developing countries have raised objection; they continue to advocate for the use of a traditional international organization—e.g., the United Nations’ voting procedures— instead of the ICANN model, for making global decisions, and defend their right to control domestic cyber activities. They maintain that, even if the U.S. leadership as a first mover has been tolerated in the embryonic stage of Internet development, the world now has to establish a new inter-governmental consensus on global Internet governance. It is because the Internet has evolved so quickly that nations find their interests conflicting. The state’s intervention to cyberspace seems to be legitimized as a part of territorial sovereignty. In particular, the rising significance of cyber security issues as a matter of national security provides state actors with imperatives to intervene and regulate cyberspace.
With state actors moving to tighten control over cyberspace, some argue that too much government involvement would undermine freedom, creativity and openness. Here, we find a confrontation between two ideas on how to govern the Internet in general, and the cyber security domain more specifically. And this ideational confrontation has been reflected to various challenges to institutionalize global Internet governance. The inter-governmental approach to the Internet and cyber security issues has been pursued by international entities, such as the United Nations’ International Telecommunication Union (ITU) and the Organization for European Economy Cooperation (OECD), and by regional bodies, such as the North Atlantic Treaty Organization (NATO).
First, the United Nations’ organizations are expanding their jurisdiction to the realm of Internet governance. For example, ITU, an international organization that traditionally has authority over telecommunications, began to deal with the Internet. In 2003 in Geneva and in 2005 in Tunis, ITU held the World Summit on the Information Society (WSIS), UN-sponsored conferences about information, communication and, in broad terms, the information society. WSIS’s chief issues included such international issues as bridging global digital divide, cultural diversities, and securing cyberspace. WSIS established the Internet Governance Forum (IGF) to open an ongoing, non-binding conversation among multiple stakeholders about the future of Internet governance.
Second, the Organization for Economic Cooperation and Development (OECD), an inter-governmental framework of advanced countries, has also participated in global Internet governance, especially securing the Internet environment for electronic commerce and the Internet economy. The OECD has developed key indicators to provide a knowledge-base for digital governance policies. In a similar vein, advanced countries have held the Conference on Cyberspace since 2011 in London; and subsequently in Budapest in 2012, and Seoul in 2013. The Conferences on Cyberspace particularly aim to develop a better collective understanding of how to protect and preserve the tremendous opportunities that the development of cyberspace offers. The issue of cyber security has quickly been making its way up the agenda in the conferences.
Third, the regional frameworks of alliance are also mobilized to cope with cyber threats from non-state actors and to prepare cyber warfare with other state actors. Among those regional efforts, the Tallinn Manual is noteworthy (Schimit 2012). As for the rules of engagement in cyber warfare, the Tallinn Manual has laid the foundation for international discussions. Written in 2013 by a group of independent experts at the request of the NATO Cooperative Cyber Defense Center of Excellence (CDCOE), the non-binding manual carries academic opinions about the application of international law to cyber conflicts and cyber warfare. However, because the manual was mainly prepared by Western countries—Russia and Chine were excluded—some contend that it represents the interests of the United States and European countries after the 2007 cyberattacks against Estonia.
In short, a variety of state and non-state entities provide some form of Internet governance, but no one organization is central to Internet governance on the global level. With the absence of an established order in global Internet governance and the cyber security realm, two different ideas concerning the issues are competing to initiate the institutionalizing process: one could be conceptualized as multistakeholderism; the other might be called intergovernmentalism. This confrontation raised concerns about a challenge to the existing global Internet order managed by the United States; the concerns fully surfaced at the NETmundial Conference recently hosted by Brazil in 2014.
>
THE U.S. AND EUROPE VS. RUSSIA AND CHINA
Behind the ideational confrontation for global Internet governance, there are conflicts of interests among countries. Led by the United States, Western countries have argued that freedom, openness and trust should be the basic principles in cyberspace. It also believes that various actors including individual citizens, civil society, businesses and governments should participate in the creation of international norms and rules. On the contrary, non-Western countries including Russia and China have maintained that information control should be possible in cyberspace for the purpose of national security, and that they cannot accept regulations that seem to unfairly benefit Western countries. This tension between the two camps shows up in the efforts of Russia, China, and other developing countries to create inter-governmental frameworks as follows.
First, on September 22, 2011, a “Draft Convention on International Information Security” was released at an international meeting of high-ranking officials responsible for security matters in Yekaterinburg, Russia. Key provisions of the draft convention may be at odds with the Western consensus on basic concepts of Internet security. The sixth article of the draft convention obliges “not to use information and communication technologies for the interference into other state’s internal affairs,” and “to abstain from slanderous statements, abusive or hostile propaganda for the implementation of intervention or interference into internal affairs of other states.” The document contains a very important stipulation: the governments may make limitations “for the protection of national and public security” (
Second, in 2012, a similar divergence was starkly apparent at the World Conference on International Telecommunication (WCIT), a conference convened in Dubai by ITU. Though the meeting was ostensibly about updating telephony regulations—the International Telecommunications Regulations (ITRs)—the underlying issue was the ITU’s role in Internet governance. Authoritarian regimes and many developing countries believe that their approach to sovereignty, security and development would benefit from the multilateral processes that the ITU employs. But democratic governments fear that these processes are too cumbersome, and would undercut the flexibility of the multistakeholder approach, which stresses the involvement of the private and non-profit sectors, as well as governments. The conference ended with the notable result: 89 states signing the new ITRs and 55 publicly opposing them. The result of the vote reinforces the image of confrontation in which there are two competing visions for the future of the Internet.
Third, the most notable development concerning cyber security came in 2013 at the UN Group of Governmental Experts (GGE) on Developments in the Field of Information and Telecommunications in the Context of International Security. Since 2004, the UN GGE has examined the existing and potential threats from cyberspace and possible cooperative measures to address them, including the original 1998 Russian proposal. In June 2013, the UN GGE made a series of recommendations on voluntary measures to build trust, transparency and confidence, as well as international cooperation to build capacity for cyber security. These have been seen as milestones in the efforts to bring about global cyber security cooperation. However, it is noteworthy that the UN GGE report includes the significant affirmation that international law, and in particular the UN Charter, is applicable to the security issues in cyberspace.
To summarize, two groups of countries are competing in the global governance of cyber security. With the United States and Europe working as a team and Russia and China as another, the group of advanced countries and the group of former socialist, authoritarian states have sought to maximize their own national interests in the process of shaping a new order in cyberspace. Whether or not the latter group’s challenges attain the goal, these two visions of the Internet are unlikely to go away any time soon. The next decade is going to be filled with similar clashes. In this context, it is essential for a middle power to see the cleavage that reflects structural conditions of the cyber security sector or Internet governance in general.
U.S.-CHINA COMPETITION IN CYBER SECURITY
Cyber security issues have recently become a major source of both tension and potential cooperation for the U.S.-China relationship.4 The two countries’ competition for world hegemony in the twenty-first century lies behind the competition in the cyber security domain. In fact, according to IR theories, the competition in leading sectors mirrors the overall hegemonic competition in world politics. Over the last few years, the issues of cyber security (or IT and the Internet in general) as a leading sector have been elevated to a top priority within the overall U.S.-China relationship. This current form of world power rivalry underlines the increasing strategic importance of cyberspace.
In June 2013, President Barack Obama of the United States and President Xi Jinping of China reached a consensus that cyber security is one of the major issues between the two powers, along with the denuclearization of North Korea. This consensus on cyber security has elevated the issue of cyber security to a top priority within the overall bilateral relationship. In spite of the developments, U.S.-China conflict over hackings and espionage are emerging. U.S.-China cyber conflict seemed to reach its peak when the U.S. Attorney General Eric Holder indicted five Chinese military officers in May 2014 for their engagement in the hacking of prominent U.S. companies’ computers to steal commercial secrets, presumably for the benefit of Chinese companies. Beijing’s response to the indictment was unusually strong. Beijing maintained that the United States caused serious damage to mutual trust between the sides. Beijing also accused the United States of hypocrisy, recalling Edward Snowden’s revelations in June 2012 that the U.S. National Security Agency (NSA) had overseen the hacking of Chinese companies (
China’s fear about the U.S. technological hegemony underlies the cyber conflict described above. China has concerns that the United States allegedly uses its technological advantages to wield its hegemony, depriving China of sharing information on the Internet and creating backdoors in its software to facilitate hacking (Swaine 2013). China is especially worried that heavy dependence on U.S. cyber security technologies would result in political disadvantages and military threats to China’s security (Lu 2013). In fact, U.S. technological companies have monopolized major technologies for cyber security in the Chinese market. The awareness that these companies are subject to U.S. law, including the U.S. Patriot Act, undoubtedly triggered a reaction in China as policymakers and ordinary users realize the huge disadvantage of their dependence on U.S.-controlled networks (Deibert 2013).
The indictment of Chinese military officers in 2014 ignited the Chinese fear about the U.S. technological dominance. China seemed to adopt a strategy of economic retribution, striking at U.S. technological companies operating within China—Microsoft, IBM, and Cisco—over security concerns (
Answering the question about the Internet security review by the Chinese government, Chinese foreign ministry spokesman Qin Gang said “whether discussing foreign companies or joint ventures, an important prerequisite is to respect China’s laws and regulations, in line with China’s national interests, and in line with China’s national security” (
>
INTERNET POLICIES AND REGULATORY INSTITUTIONS
Similar competition in cyber security technologies is also found in the conflict between U.S. technological companies and the Chinese government over the policies and institutions for Internet censorship. While the Internet was originally designed to be free of censorship in the United States, the Internet came with the state’s Internet censorship system in China. The Chinese government argues that it is a legal privilege of a sovereign state to impose the Internet censorship system on foreign technologies and companies in order to filter harmful and insecure information for national security. In this context, U.S. companies such as Microsoft, Cisco, Yahoo, and Google had to admit regulatory standards of selfcensorship if they want to enter into and stay in the Chinese domestic market (Hughes 2010).
However, tensions exploded in January 2010 when Google announced that it was withdrawing from business in China. The case involved three issues: alleged efforts by the Chinese government to steal Google’s intellectual property; intrusion into the G-mail accounts of Chinese activists; and in response, Google’s decision to stop complying with censorship of searches by Google China, although Google had been complying for four years. Google’s decision inflicted a noticeable cost upon Chinese soft power (Nye 2011). Thus, the Chinese government responded quickly to this series of events. It officially argued that it was not involved in the intrusion into Google, and that it does not make sense for the government to mobilize hackers to launch cyber-attacks on a private company. It maintained that any business activities of IT companies in China must follow the laws of China.
On January 15, 2010, the U.S. government became involved, and supported Google’s position on the conflict. In particular, Secretary of State Hillary Clinton mentioned Google’s example at a speech on Internet freedom on January 21 (Clinton 2010). The Google case seemed to hit the U.S.-China relationship in other ways. The Obama administration announced the plan of arms sales to Taiwan, and a plan for President Obama’s meeting with the Dalai Lama. The problems with exchange rates of Chinese yuan and trade barriers, such as antidumping duties, were raised. In a broader sense, the 2010 Google dispute revealed the differences in the models of political economy. If Google’s decision came from the private-public relationship, which was rooted in Silicon Valley, the attitude of the Chinese government is based on China’s state-driven model. In this sense, the Google case reflected the competition between two institutional models of political economy: the Washington Consensus vs. the Beijing Consensus (Kim 2012).
The attitude of the Chinese government expressed in the Google case in 2010 has been reinforced with the 2013 Snowden case and the 2014 indictment case of Chinese Army officers. For example, in the Brazilian Congress speech on July 16, 2014, Xi Jinping, referring to “shoes theory,” maintained that “Only people who wear shoes know whether or not they fit . . . there is no universal model of development and we should continue to firmly support each other’s path of development suited to their own national conditions” (
>
COMPETING SECURITIZATION OF CYBER SECURITY
At the most abstract level, U.S.-China competition over cyber security issues enhances the competition for securitizing the domain. The complexity of cyberspace makes it plausible to adopt the theory of “securitization,” presented by the Copenhagen School of security studies in International Relations (Buzan et al. 1998; Wæver et al. 1993; Wæver 1995; Hansen and Nissenbaum 2009). According to Barry Buzan, the securitization of particular issues is constituted by “the intersubjective establishment of an existential threat with a saliency sufficient to have substantial political effects” (Buzan et al. 1998, 25). Cyber security issues are typical examples of securitization in the sense that threats to security in cyberspace, at least so far, tend to be a matter of constituting discourses, rather than that of hunting down real threats. Because cyber-attackers may operate at a distance obfuscating their identities, locations, and paths of entry, the culprits are presumed rather than proven to be guilty. In fact, cyber security has long been highly politicized and securitized by dozens of government agencies and traditional corporations.
In fact, the cyber security domain, in which threats are still imagined virtual, and thus are not yet regarded as real, is a terrain on which multiple discourses compete (Rid 2013). Thus, the securitization of cyber security is important: to define what cyber security is, what challenge it presents, who poses threats, where the threats are originated, and how it mitigates the cyber security threats (Deibert 2002; Hansen and Nissenbaum 2009). In this view, U.S.-China cyber conflict and Internet policy frictions are all predicated upon the competition for preoccupying security discourses in cyberspace. It is because the competition is not related only to ideational difference, but also deeply involved with interest conflict that affects the future of the reality. This article addresses U.S.-China differences of security discourses from three aspects.
First, while the United States points to “cyber security” against their computer and network system by attacks to crash, slow, or paralyze vital infrastructure, and by the theft of proprietary commercial data or information, China securitizes trans-border information flows and diffusion of resistant political discourses as threats to its regime, and asserts “information security” including a kind of overt censorship. Formulating the discourses of “Chinese hackers’ threats,” the United States asserts that a growing number of destructive cyber-attacks on commercial enterprises and government institutions originate from China (Dahong 2005; US-China Economic and Security Review Commission 2009; Barboza 2010; Hvistendahl 2010; Clark 2011). In 2013, for example, the California-based U.S. cyber security firm Mandiant linked “a number of attacks to a military-affiliated group based in Shanghai” (
Second, while the United States highlights cyber security at the individual level such as protection of privacy, human rights, and freedom of expression, China has been more concerned about Internet freedom at the national level through means to secure domestic political stability such as censorship and regulations, restricting the freedom of press. U.S. cyber security discourses emphasize securing individual rights in cyberspace as an open space, and are cautious of possible threats to these values. Hillary Clinton’s address on January 21, 2010, around the time when Google decided to retreat from the Chinese market, shows well the value of Internet freedom that the United States appreciates (Clinton 2010). In comparison, China legitimizes Internet censorship and policy autonomy for elevating national freedom rather than individual freedom, and maintains that freedom of the Internet is subject to the laws and morality of a nation. The Chinese government’s position toward the 2010 Google case, and its policies to implement Internet security reviews over the foreign IT companies could be legitimized in terms of national rights and freedom to protect security in the Internet (Wang and Xu 2011).
Third, while the United States security discourses have been based on neoliberal visions on the free flows of information in cyberspace, the Chinese discourses are composed of anti-hegemonic and nationalist visions of state sovereignty in that the globalized Internet poses a major threat to the sovereign authority of nation-states. Since the early age of the Internet, the United States has assumed cyberspace to be a global space, in which information flows transnationally, and has presented an Internet discourse that urges to remove any obstacles that impede the establishment of a liberal order in cyberspace. The discourse is consistent with the U.S. position appearing in the process of building international norms as discussed above. In comparison, China advocates the need for a government to identify the boundaries of cyber territory and protect it against cyber threats (Swaine 2013). For example, President Xi Jinping called for respect of all countries’ cyberspace sovereignty on July 16, 2014, telling the Brazilian congress that “although the Internet is highly globalized, the sovereignty of the information of all countries should be respected” (
To summarize, two world powers are competing over cyber security at multiple levels. In the sense that these two powers are leading the aforementioned two groups or networks of countries that have different orientations to Internet governance, their competition could be called a form of “inter-network politics,” which this article presents to conceptualize the politics of cyber security. Certainly, whether the United States and China have a basically cooperative or antagonistic relationship over the coming several decades, this will be a significant structural condition for South Korea that pursues middle power diplomacy in the cyber security domain.
4Concerning the U.S.-China relationship in cyber security, the Internet and information technology in general, see Shen (2010), Manson (2011), Cai (2012), Liberthal and Singer (2012) and Kim (2012; 2014c).
MIDDLE POWER DIPLOMACY IN CYBER SECURITY
I now turn to middle power diplomacy in the cyber security sector, of which structural conditions are conceptualized as “asymmetrical inter-network politics.” What diplomatic roles would South Korea play under such structural conditions? Before going for middle power diplomacy, it would be wise for South Korea to build “cyber capabilities” to fend off cyber terror and threats. Could South Korea be referred to as a “strong cyber security nation” corresponding to its reputation of being a “strong Internet nation”? In the wake of a series of North Korean cyberattacks, South Korea has sought to strengthen those capabilities by developing firewalls, cyber specialists, cyber warfare command, educational organizations and legal frameworks to push for cyber protection. Putting off the discussion about South Korea’s cyber capabilities, however, this article examines South Korea’s middle power diplomacy in the sector, adopting three conceptual pillars of middle power diplomacy—brokerage, collection, complement—presented in the second section.
>
BROKERAGE DIPLOMACY IN CYBER SECURITY
Identifying overall structural conditions of the sector, South Korea has to contextualize its position within the network structure of cyber security politics. In other words, required for South Korea would be the strategies of adjusting itself to the structural conditions of the sector. With regard to the adjustment strategies, this article pays special attention to the middle power’s strategic roles of “brokerage.” The unique forms of cleavages found in the sector are likely to provide middle powers with structural opportunities of brokerage. However, the structural conditions are also likely to create a situation threatening South Korea’s attempts for brokerage on the following three aspects.
First of all, it is probable that South Korea faces opportunities and difficulties with regard to its choice between the two different technical standards. In fact, brokerage issues in the cyber security sector would be concerned with choosing a technical standard between the United States and China. Does South Korea keep compatibility with the dominant standards of the United States? Or does it cross the threshold and move into an alternative standard that China wants to set in East Asia as well as in China? In the case that China takes a technological offensive with its cyber security standards, what would be the decision for South Korea, which has heavily relied on U.S. technical standards, such as Microsoft’s Windows operating systems and Internet Explorer, and Cisco’s network equipment? Recently, South Korea was dissuaded by the United States when South Korea attempted to introduce network equipment provided by Huawei, a Chinese telecommunications company, in early 2014 (Kim 2014c).
This is a tough choice because it is not only relates to technologies but also involves diplomatic issues: i.e., will South Korea stick to the U.S.-Korea alliance or will it broaden the existing Sino-Korea cooperation? Indeed, the choice means a process of “connecting and disconnecting” that might build new relationships on the one hand, and break existing ties on the other hand. It is usually accompanied by the process of “asymmetric coordination of relationships,” belonging to the realm of strategic choices relating to the risk of opportunity cost. This process of integrating or destroying ties lies at the heart of brokerage in the sense that brokerage may alter network structures, leaving actors with a fundamentally different set of network ties, and changing the agenda in a network. Recognizing the roles of brokerage diplomacy, South Korea has to be familiar with managing the asymmetric coordination game among network partners, but must not forget to pursue compatibilities between two networks.
Second, opportunities or difficulties on a middle power’s brokerage are also detected in issues regarding Internet policies and regulatory institutions. In building the Internet policy and governance models, South Korea’s choice is placed between the private-sector-driven model of
South Korea’s experiences in politico-economic development provide good examples for the meta-model, in the sense that the South Korean model of political economy, which I would call “Seoul Consensus,” is likely to combine the concerns of developing countries as well as those of advanced countries. Indeed, although the South Korean model began with the authoritarian model pursuing economic growth—recently conceptualized as “Beijing Consensus”—it has come to achieve the goal of democracy after remarkable economic development—which is usually called “Washington Consensus,” as prescribed by advanced countries, especially the United State (Sohn 2007). In this context, it is a plausible scenario to develop a model of “Seoul Consensus for cyber security” in the sense that South Korea has achieved prosperity in the Internet economy, initiated by the private sector although it is still regarded as a country that has state initiatives against social activities in cyberspace.
Finally, opportunities and difficulties exist between two different positions with regard to global Internet governance. Indeed, South Korea has difficulties in positioning itself between two different visions for global Internet governance. One vision has been driven by Western countries that believe the Internet should be more open and free; the other driven by developing countries’ support for the inter-governmental approach and state sovereignty over cyberspace. South Korea’s official position is now known to support the open and flexible approach to global Internet governance initiated by various international entities such as the UN, ITU, OECD, and ICANN. The approach could be called the complex strategy of Internet governance, combining the two competing visions.
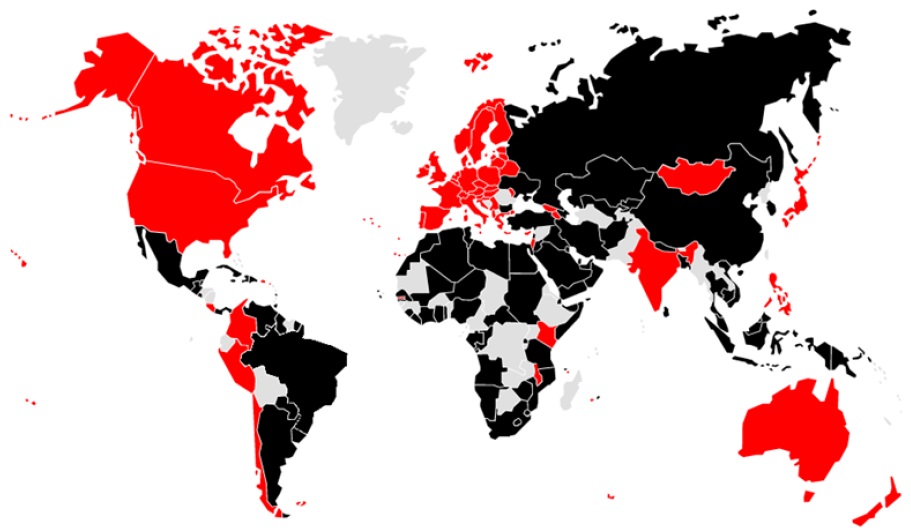
However, it is expected that South Korea would have difficulties in structural positioning in the sector. For example, South Korea was crammed between advanced countries and developing countries in the vote for updating the ITRs at WCIT in 2012. At last, South Korea voted for the ITRs so that it joined the group of 89 developing countries (Black in Figure 1), and thus took an opposite position to the 55 countries that publicly opposed the ITRs (Dark Gray in Figure 1); non-member states of ITU are in grey . Right after South Korea’s vote, a South Korean newspaper denounced the South Korean government when it revealed its intention to control the Internet (
>
COLLECTIVE DIPLOMACY IN CYBER SECURITY
To attain the goals of middle power diplomacy in cyber security, South Korea has to rely on the strategy of collecting and attracting as many like-minded countries as it can. In other words, South Korea has to define the new roles for like-minded groups and continue to attract them as supporters. It is critical for South Korea as a middle power to adopt this strategy of diplomacy, as it will help alleviate the dilemma of being a broker in the cyber security sector (Kim 2014a).
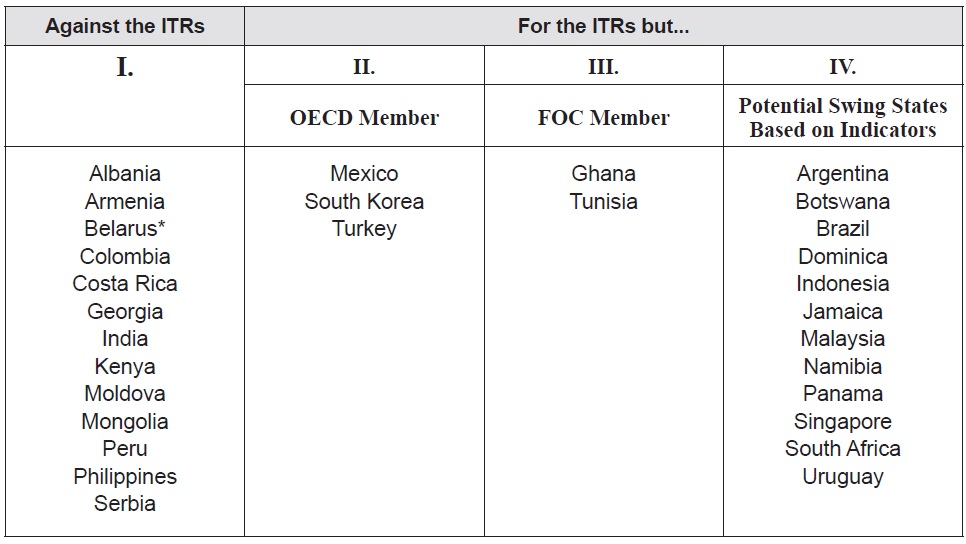
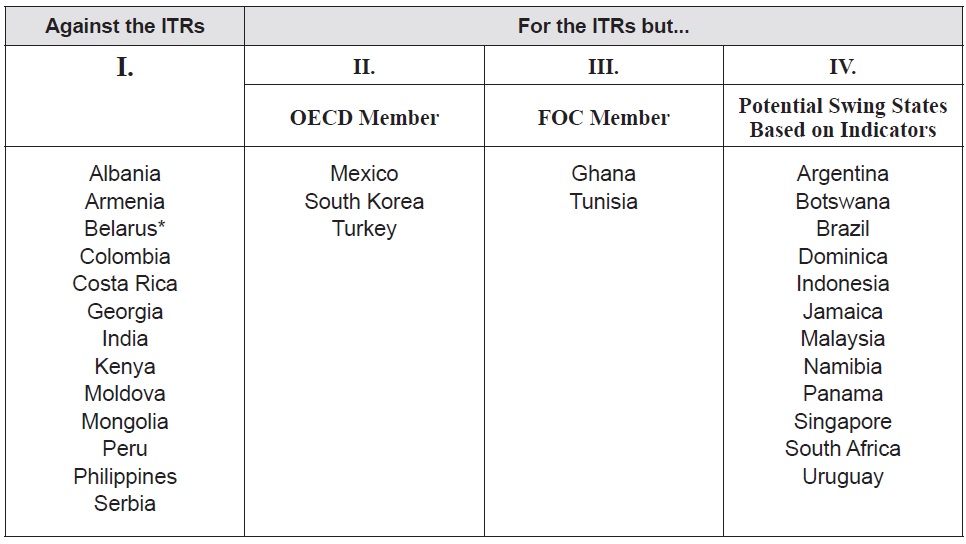
With regard to collecting like-minded countries in the cyber security sector, Maurer and Morgus (2014) conducted research for the Centre for International Governance Innovation (CIGI), identifying some interesting patterns among certain groups of states voting at WCIT 2012. A core group of potential swing states—a total of 30 countries—is identified based on their voting behavior. The research “essentially marries the voting record on the ITRs with a series of other indicators to identify patterns and the group of countries likely to act as swing states in the global Internet governance debate in the future due to path dependence, logic of appropriate behavior and state interests” (Maurer and Morgus 2012, 4). These 30 swing states are sorted into the four groups of countries as follows (see Table 1).
[Table 1.] Top 30 Global Swing States
Top 30 Global Swing States
Group I includes 13 swing states voting against the ITRs: Albania, Armenia, Belarus, Colombia, Costa Rica, Georgia, India, Kenya, Moldova, Mongolia, Peru, Philippines and Serbia. These 13 swing states are noteworthy because they are not part of any of the group of states, but their positions at the WCIT set a precedent for similar behavior in the future. These states also have the resources to persuade other countries to change their behavior and to significantly influence the outcome of Internet governance discussions. Group II includes three OECD countries, Mexico, Turkey and South Korea; and Group III includes Ghana and Tunisia—two members of the Freedom Online Coalition (FOC).5 All these five states supported previous commitments by both the OECD and FOC, and thus their membership and commitments are at odds with their ITRs voting record. Moreover, they are likely to experience significant pressure from their peers in the future to change their behavior to be appropriate with their membership and commitments. Group IV includes 12 countries voting for the ITRs: Argentina, Botswana, Brazil, Dominica, Indonesia, Jamaica, Malaysia, Namibia, Panama, Singapore, South Africa and Uruguay. They are potential swing states because several indicators, adopted by the research, show the importance of the Internet for those countries and various characteristics of these states suggest that there are opportunities to engage with them to potentially change their behavior in the future (Maurer and Morgus 2014 11).
Maurer and Morgus’s groupings of the 30 swing states provides South Korea’s middle power diplomacy with some implications for collecting and attracting like-minded countries and formulating coalitions in the cyber security sector. First, it is conceivable that South Korea pursues coalition with countries voting for the ITRs, which belong to Group II. Interestingly, three countries in Group II—Mexico, Turkey, and South Korea—are participants of MIKTA (a coalition of Mexico, Indonesia, Korea, Turkey, and Australia), which has gained increasing attention in recent years. Second, it is also probable that South Korea extends the MIKTA coalition to FOC countries, Ghana and Tunisia, which belong to Group III. Third, it would be more interesting for South Korea to associate with the positional swing states in Group IV. Among them, Indonesia is the first candidate since it is a member of MIKTA. Also, two IBSA (India, Brazil and South Africa) countries, Brazil and South Africa are possible partners that keep pace with South Korea in the fields of global Internet governance. Impressively, these countries, especially Brazil, have played a leading role in renovating the ICANN system. Finally, it is imaginable that South Korea may form solidarity with another IBSA country—India for example, which belongs to Group I as it is voting against the ITRs. In addition, Australia, which is not included as a part of the 30 states, is likely to have a similar mind with South Korea since it is a member of MIKTA.
In implementing collective diplomacy, South Korea should be flexible in choosing partners and in coalescing issues. For example, South Korea has to figure out which agenda is appropriate for the selected coalition partners. Various issues on global Internet governance in general could be linked to the specific issues of cyber security. Beyond the boundaries of Internet governance, other security and economic issues could be linked to cyber security issues in order to increase the effectiveness of collective diplomacy. For example, official development aid (ODA) must be a good item of issue linkage politics for South Korea’s middle power diplomacy in cyber security. Also, South Korea could grasp opportunities through combining non-traditional security issues together, such as cyber security, atomic energy, and ecological security, as world powers are still competing for the priority of, and even the goal of, governance mechanisms.
>
COMPLEMENTARY DIPLOMACY IN CYBER SECURITY
While South Korea needs to engage in programming the “rules of the game” in the cyber security sector, middle powers’ programming diplomacy, if any, should be complementary to the existing system; it is likely and even desirable for them to patch up some sub-programs upon the platform designed by world powers. Those complementary programs might target some niches or holes that world powers neglect due to their ontological and epistemological limitations. In particular, its unique position in the existing system requires middle powers to play a complementary role to the existing world order, not to play an exploitive role through challenging world powers’ initiatives (Kim 2014a).
South Korea’s complementary diplomacy in the sector has to begin with a more thorough understanding of the features of the cyber security sector. Both offense and defense take place in cyberspace as an environment of complex networks, in which it is sometimes not possible to identify the subject of offense or the object of retaliation. A wide array of threats to state and business actors are perpetuated by non-state actors. Moreover, cyber threats are continuously evolving, and increasingly blurring distinctions between human and non-human actors, such as computer viruses and malicious codes that “exploit” holes in computer networks (Galloway and Thacker 2007). In this sense, the world powers’ simplistic approach, based on the traditional conception of “power politics,” does not fit into the nature of cyberspace, which is strongly predicated upon complexity. Indeed, cyber security issues do not belong to the realm of “international politics” between nation-states competing over traditional security issues. In this context, the possibilities of middle powers’ complementary roles would emerge.
For example, middle powers are likely to privilege the problematizing of normative legitimacy that the existing world order may lack. I would call it the strategy of “normative programming” in the sense that diplomatic concerns are with normative, not with positive, aspects of the sector. For middle powers that have less military capabilities and economic resources, norm- or value-oriented diplomacy are crucial and effective means to attain goals. Indeed, diplomatic strategies which are inclusive and close to international norms are more likely to be attractive to other countries (Slagter 2004). Moreover, if the middle powers pursue collective diplomacy, and mobilize supporters around the world, the authority of normative diplomacy will be reinforced. Considering the normative aspect of middle power diplomacy, is it possible for South Korea to “exploit” such “structural holes”? In this context, I present three ideas on the complementary and normative approaches, which South Korea needs to develop.
First, South Korea as a middle power could criticize and complement the security discourse of world powers, based on the Cold War metaphor and the analogy of the arms race. Recently, concerns have grown to view the cyber threat from the perspective of militarization in cyberspace (Lawson 2012). Cyberconflict is after all the newest mode of warfare and cyber-weapons have been described as weapons of mass disruption. In reality, the United States and China are strengthening their capacity to engage in both defensive and offensive cyber actions against each other, presenting the prospect of a cyber-arms race while potentially intensifying the already high level of distrust between the two countries. Attention on the military dimensions of cyberspace is justifiable. However, no solution for a security dilemma will appear as long as the world powers keep relying on the ‘zero-sum arms race’ analogy. In this context, it is meaningful for South Korea to stress the other aspect of cyber-conflict, by developing the demilitarized peace discourse in cyberspace.
Second, South Korea has to complement the current security discourses of international laws—a national or international approach to cyber security with legal minds. Recently, scholars point out the lack of an international legal framework that defines the use of force in cyberspace; they examine the legal dilemmas regarding the use of force in cyberspace and questions of how the Law of War can be applied to cyber-threats (Liaropoulos 2011). The Tallinn manual is a noteworthy example that applies international norms to transnational threats in cyberspace. However, considering operational difficulties in deterring and identifying cyber-attacks and the asymmetric dimension of cyber-conflicts, inadequate are international laws and norms, predicated upon the dichotomy of actors—i.e., offense and defense—in the modern international politics. What we need is more complex discourses and norms that are able to handle the postinternational or inter-network dynamics of cyber security issues. In this context, South Korea as a middle power could contribute by developing a new network discourse complementing the existing international discourses.
Finally, South Korea could complement the world powers’ security discourse with cyber ethics. Cyber ethics encompasses Internet users’ behavior and what computers are programmed to do, and how this affects individuals and society. Previous examples of cyber ethics include various issues concerning personal information or privacy: Who owns digital data? What should users be allowed to do with it? And, how much access should there be to obscene contents online? Now those ethical questions should be extended to international or transnational issues of cyber security. As an ever increasing amount of people connect to the Internet, there is a susceptibility to identity theft, cybercrimes, and computer hacking. Historically, security has long been a topic of ethical debate. Likewise, it is expected for such ethical debates to arise in the cyber security sector. In this context, South Korea as a middle power is likely to develop new discourses in cyber ethics as an underdeveloped field, which complement the realist or the liberal discourses of the world powers.
5The membership of the Freedom Online Coalition (FOC) currently includes 22 countries. This coalition defines itself as “an inter-governmental coalition committed to advancing Internet freedom—free expression, association, assembly, and privacy online—worldwide (Maurer and Morgus 2014, 7–8).
Cyberspace is now an unavoidable reality that covers the earth with complex networks; it has evolved so quickly that individuals and organizations have to adopt proper measures for security. This is challenging because cyber security issues are characterized by the dynamics, structures, and actors in complex networks, making these issues distinctly different from traditional security issues. Cyber threats are continuously evolving, and increasingly blurring distinctions between territorial boundaries. As cyber security continues to rise to the front line of world politics, the stakes will increase and tensions and disagreements will become more prevalent.
Bearing the rising significance of cyber security in mind, this article explores the possibilities or constraints of South Korea’s middle power diplomacy in the sector. To explain the roles of middle power, this article relies on the positional or network approach, which has its origins in network theories of the natural and social sciences. In this view, it is critical to comprehend the conditions of structure first, not the attributes of actors. Before exploring some details for South Korea’s middle power diplomacy, this paper identifies from two aspects of the structural conditions that are unique in the cyber security sector.
On the one hand, two groups of countries are competing for global cyber security governance: the existing model has been driven by Western countries that believe the Internet should be more open and free. In recent years, however, the challenges, driven by a coalition of states—including Russia, China and other developing countries—are organized and have a clear, more state-controlled vision for the Internet. On the other hand, the United States and China—two world powers in the twenty-first century—are competing over cyber security. Different approaches to cyber security in technical standards, regulatory policies, and security discourses are contrasting between the two world powers and such differences are likely to spill over into a broader tension between them.
Cyber security issues do not belong to the realm of “international politics” between nation-states competing over traditional security issues; but they do belong in the realm of asymmetric “inter-network politics” between complex actors. Cyber security issues are evolving in the complex environment that intrinsically contains bugs and holes—i.e., “exploits”—and computer viruses and malwares are actively utilized. In this context, moving beyond the traditional framework of inter-governmental organization, various state and non-state actors are recently participating in the new global frameworks for cyber security; at some point in the future, it may be possible to reinforce these global frameworks with certain fundamental norms, but the world is at an early stage in this process.
These structural conditions in the cyber security sector are continuously evolving toward an unprecedented modality of world politics. It is critical for South Korea as a middle power to understand the structure and dynamics of the cyber security sector, to find out any cleavages of who is in which camp in the process of global Internet governance, and to recognize whether the United States and China will have a basically cooperative or antagonistic relationship over the coming several decades. Even more, South Korea has to realize that the potentially poisoning effect of cyber security is occurring at a time when there is genuine uncertainty about the future of cyberspace. The next decade is going to be filled with various clashes as those complex actors in world politics are competing for their own political needs and desires.
Under the circumstances, South Korea should figure out what kinds of specific roles are expected of its middle power diplomacy. Here, it is most important for South Korea as a middle power to have the ability of contextual and positional intelligence, which reads constantly evolving contexts and identifies its moving positions in cyber security. The discussion about network structure and position offers the directions of networking strategies that a middle power has to pursue. Applying these theoretical resources, this article identifies three elements of middle power diplomacy in the cyber security sector which South Korea should consider. This article suggests three strategic pillars of middle power diplomacy— brokerage diplomacy, collective diplomacy, and complementary diplomacy.
To summarize, South Korea should be able to manage asymmetric relationships among the world powers and global governance. South Korea would act as a broker, more than a mere connector, providing the mode of transition, switching, transforming, and translation between different actors of networks. To fulfill the brokerage roles, South Korea has to learn how to bring together like-minded countries in the sector, and to attract supportive forces in world politics. By questing for networking strategies, South Korea as a middle power could be an architect, not a whole system designer but a complementary programmer, who can provide useful patch programs for the whole system operated by world powers. In short, being equipped with the ability, it would be more likely to define middle power roles corresponding to the structural conditions of the cyber security sector.