Currently, biometric technology based on mobile devices is increasingly used in various areas that require a high level of reliability, such as banking and procurement services. It is necessary to make efforts to develop a security system that can preemptively manage potential security threats and manage mobile biometric data security. In addition, because biometry manages sensitive personally identifiable information (PII), certain privacy issues for biometry in mobile devices should be considered [1].
In the early 2000s, a major telecommunications company in Korea demonstrated a shortdistance purchasing service based on radio-frequency identification (RFID). However, because of high investment costs, a lack of dongle reader inventory, and the absence of an average standard, the service ceased. Recently, as smartphones with near field communication (NFC) technology have become popular, the mobile purchasing environment and short-distance purchasing services have been reorganized.
Secure element (SE), a core platform of mobile purchases, stores confidential information such as account numbers and biometrics information. Depending on realizations of the SE, there are four categorizations for short-distance mobile purchases. The first category is the universal subscriber identity module (USIM), which is preferred by telecommunication companies. The second category is the microSD method that financial institutions and service providers can provide independently. The third category is the embedded SE method that preloads SE into a given device for an operating system (OS) platform or for a mobile company. Finally, the fourth category is a cloud-based service that converts online and offline. providers can provide independently. The third category is the embedded SE method that preloads SE into a given device for an operating system (OS) platform or for a mobile company. Finally, the fourth category is a cloud-based service that converts online and offline.
Moreover, depending on the communication method between point of sale (POS) and a given device, the short-distance mobile purchase differs between NFC techniques and non-NFC techniques. The introduction of a non-USIM method intended to modify the current mobile purchasing environment that is based on USIM. In the mobile purchasing environment, telecommunication companies and businesses have various ideas, such as the expansion of infra and the development of a platform that overlaps other platforms. This makes high competition inevitable. Proponents of non-USIM and USIM will each attempt to develop various services. Initially, purchasing services based on NFC were featured prominently because of an expectation to use a variety of additional services. However, because of the pressure for POS infra-construction and the opposition from several different parties, the development of such services has been delayed longer than expected.
For the revitalization of purchasing services based on NFC, a franchise infra-construction and a prominent additional service available only for NFC are necessary. Meanwhile, services based on non-NFC are rapidly dominating the purchasing environment because of their advantage of an increasing number of customers and franchises. With governmental support for the revitalization of debit card usage for a healthy consumption life, short-distance mobile purchases introduced a barcode account to transfer payment gateway services.
Mobile debit purchasing services allow users to confirm their identity online, and to complete purchases through their smartphones without NFC technology. Issuing an account for a particular user is easy and simple; a special intra is not required; and the commission rate is low. Considering all these characteristics, it is predicted that mobile debit purchasing services will dominate the purchasing environment.
Generally, SE represents a security area that cautiously stores a variety of data, such as financial, confidential, identification, and account numbers with cash, debit, and credit card information. SE also acts as a core platform that personalizes, manages, and installs applications that allow the users to directly create necessary information for mobile purchasing services. In order to personalize biometric template information such as fingerprints, face, iris, and speech recognition, the use of SE is crucial.
This paper is designed to provide a framework to ensure the security and reliability of the flow of biometric information for telebiometric applications using mobile devices. Furthermore, we define twelve telebiometrics authentication models depending on the configurations of the biometric sensor, the mobile device, and the server. The paper also specifies threats in operating telebiometric systems based on the mobile device, and proposes a mobile telebiometrics application system that is applied in real operating environments in order to establish a safe mobile environment for the use of telebiometric systems. The rest of this paper is composed as follows. Section 2 describes related works. Section 3 describes threats and the environment for telebiometric applications using mobile devices. Section 4 analyzes the Authentication Model and Protocol. Section 5 explains the proposed implementation based on the specific model. In Section 6, conclusions will be given.
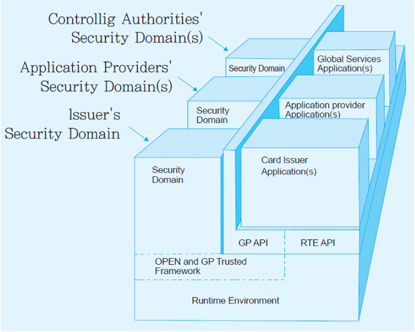
As Figure 1 shows, SE consists of a security domain that stores important data, an Issuer security domain that manages said domain, and other elements that allow communication between the access material and the application stored in such a domain [2].
The security domain is responsible for downloading, installing, deleting, and personalizing a given application. Such a domain has the keys necessary for security and provides security services such as encryption, decryption using a certain key, and digital authentication. In addition, the security domain provides a security channel protocol that allows secure data communication with an external environment using excluded keys in order to prevent any interference from other security domains. The issuer security domain, instead of the card issuer, holds the master key and manages the security domain provided by the security domain issuer. Using the master key, the issuer security domain creates and deletes the security domain and the application within the domain. The application is an applied program developed by the SE provider or by the service provider. The application includes the card issuer application provided by the SE issuer, an application provider that delivers cash, traffic, and credit card functions, a global services application that provides a cardholder verification method, and a global service that identifies a given cardholder with different applications installed in the card. The runtime environment represents the card operation system (CardOS or COS) that is similar to the general computer operating system. The runtime environment is the chip operating system that manages the overall physical resources of the interior card, such as communication between the card and the device, reading and writing data within the internal memory, access control of files, user authentication, and application use. Some typical card operation systems are Java Card, MULTOS, and Windows Card. The global platform application programming interface (API) provides card management services such as user authentication, personalization, security service, card locking, and update to the application lifecycle [3].
USIM, which is a module that is recognized by its wide use, is involved in authentication and the management of subscribed members. USIM consists of the CPU, EEPROM, ROM that includes the programs necessary for the operating system, RAM that is the working space of the CPU, and input/output circuits. In other words, USIM can be seen as an integrated circuit (IC) chip that has communication techniques and a user interface. Through these characteristics, USIM allows applications that require an intense security to process actions only through internal colocation without exposing data. USIM allows continuous storage of necessary information, and it provides convenient transportability. Furthermore, using over the air (OTA) technology that can download personal information and other applications into the USIM internal memory, it is possible to add credit, transportation, and membership card functions without creating other chips. Currently, most mobile payments use the USIM method as an SE because of an earlier concern where USIM fulfilled subscriber authentication functions with the 3G network of telecommunication companies and with the current characteristic of mobile payment services; it is not easy to provide services that exclude telecommunication companies. When installing USIM as an SE into a smartphone with NFC functions, the data connection between the NFC chip and USIM is performed through Single Wire Protocol (SWP). Because USIM has been developed around the IC chip technology to emphasize the security characteristics of USIM, approaches from external devices to USIM contents are very restricted. These restrictions complicate the use of USIM-based services and additional service realizations. As a result, telecommunication companies control the storage of USIM into SE. For example, if the telecommunication companies assign to service providers, such as banks and credit card companies, certain USIM domains that were given to a user, the service providers can utilize USIM to provide mobile banking and mobile credit card services to the user. These circumstances can lead to a misinterpretation among businesses that the service providers form a subordinate model to the telecommunication companies. The early USIM was introduced as Contact USIM for contact communication that maintained user information, basic network information, and data necessary for user authentication. Later, Combi USIM, which provides additional services such as transportation and financial functions, was introduced by adding radio frequency (RF) functions to Contact USIM. Recently, NFC USIM, a USIM that applies the global NFC communication interface, was developed. As a result, a combination of Combi USIM and NFC USIM is widely used. A future prediction of USIM is that HD USIM, a new generation of USIM that combines a high quality processor and massive storage, will be developed.
MicroSD is a small flash memory card that is one-fourth the size of a secure digital card and has a height of 0.7 mm, a width of 15 mm, and length of 11 mm. A microSD card is detachable and it is generally used with portable devices such as smartphones, game consoles, and digital cameras. Recently, within the financial environment, there have been efforts to interrupt the influence of telecommunication companies. Financial companies have been installing SEs into microSDs and attaching the microSDs to existing smartphones in order to provide mobile payment services. By attaching microSDs to mobile devices, financial companies seek to provide mobile payment services through a contactless communication interface. In 2009, NXP and Typhone jointly researched a solution to combine microSDs and multiple functions based on global platforms such as antennas, flash memory, and card controllers. In 2010, Visa and Device Fidelity jointly announced a solution for payment services using microSDs. Early microSDs demonstrated limited functionality because of small size restrictions and interfering limitations, colliding with other metal elements in the smartphones. However, because of technological developments, most of these limitations have been resolved. One of advantages of microSDs is their flexibility in regards to function domains. This advantage increases the types of smartphones that can use microSDs.
Embedded SE (eSE) is a form of installing the SE domain that is independent of the NFC chip or the internal memory during the source-making process. The recent mobile environment has been reorganized based on smartphones, and this environment is greatly influenced by the OS platform business and cellphone manufacturers. Because of these changes, an interest in installing SEs into NFC chips during the process of creating such chips has been prominent. Compared to the USIM and microSD methods described in the previous sections, the eSE method allows OS platform developers and cellphone manufactures gain service leadership. However, this method has difficulties detaching SE, which causes the reutilization of devices to be impossible. In addition, the role of telecommunication companies is reduced to become merely providers for voice services, while data usage providers and cellphone manufactures gain a large amount of authority on user control. These circumstances might cause conflict between the telecommunication companies and the cellphone manufacturers.
2.4 Cloud-based Service Authentication
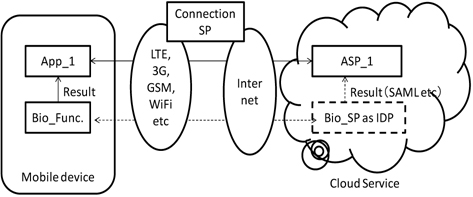
A server purchasing service method is a form of service that allows users to enter their payment information, such as an account number, before making a purchase, and to pay at the moment of purchase by inserting a particular key, such as a password. This method can be performed online or offline and is often called a cloud-based purchasing service. This service allows users to download an application to their smartphones and enter their payment information. However, because of the wireless data connection between a smartphone and a particular website, this service has the potential risk of data exposure to hackers who can decrypt the data. Therefore, cloud-based purchasing services should intensify different security methods, such as user authentication, before accessing account information, saving real credit card and other banking information on the website of a financial institution and saving simulated card information on the service provider website. The ITU-T SG17 Q.9 X.tam model includes cases such as saving biometric template information on the cloud. In this case, the model is predicted to be prepared for security flaws of wireless communication.
3. Threats and Environment for Telebiometric Applications Using Mobile Devices
Key logging (more often called keylogging or keyloggers) is the action of recording (or logging) the keys struck on a keyboard, typically in a covert manner such that the person using the keyboard is unaware that their actions are being monitored and recoded. Such an attack is sometimes implemented in software that executes on mobile devices.
3.2 Lost or Stolen Mobile Device
Mobile devices are increasingly targeted for theft because they store credential information that might lead to financial gains. A malicious attacker could steal a cellphone and attempt to log on to various user accounts.
Shoulder surfing indicates an attackers ability to obtain all or part of a user’s credentials by briefly observing the information provided by the user during authentication.
3.4 Phishing/Active/Passive Man-in-the-Middle Attack
Man-in-the-middle attack is a special type of social engineering in which the attacker resides between the user and the intended service provider, and attempts to emulate the behavior of the original service provider in order to deceive the user into revealing the required credentials.
3.5 Session Hijacking and Parallel Session Hijacking
During a session hijacking attack, malware or an attacker can assume control of a session initiated by a user, and utilize the information stored in the session to perform other transactions or alter the transactions already conducted.
Depending on the method of communication between a mobile device and a personal computer, a DoS attack might be executed. To prevent such types of threats to telebiometric applications using mobile devices, we provide a telebiometric security reference model for operating telebiometric systems using mobile devices, including cloud computing services [4, 5]. In addition, we provide a general guideline for related threats, and countermeasures to ensure the security and reliability of telebiometric applications using mobile devices, as shown in Figure 2 [6, 7].
4. Authentication Model and Protocol
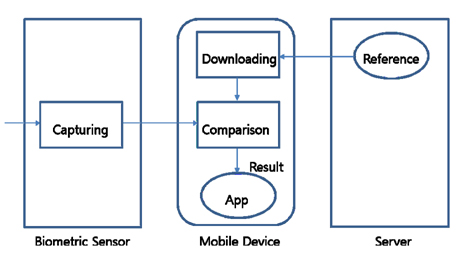
To define the framework for the telebiometric system using mobile devices, basic components are required, such as capture of a biometric sample, storage of a biometric reference, and comparison of a biometric sample with a biometric reference. For the respective three components, we categorize twelve telebiometric authentication models depending on the configuration of the biometric sensor, the mobile device, and the server. In the case of Model 2, the application requires server side verification. The server sends the registered users template. It compares the acquired sample data with the received template, sending the result to the application. Model 2 follows the same sequence as Model 1, with the exception of the transfer template from the server. Template identification (ID) information is required and forms the comparison result. Under this structure, it is practical to use many terminals that are suitable for a web-verification model, as users can connect to the server from an approved mobile device. Model 2 requires a registration of the biometric reference template from the server and requires the server to trust the mobile device processing procedure [8].
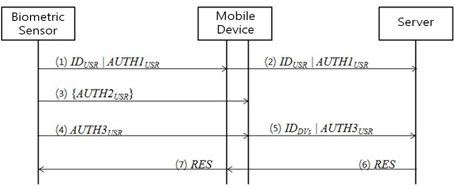
(1) The biometric sensor transports its own ID and knowledge base authentication information or bio-base authentication information (AUTH1USR) to the mobile device(2) The device transmits the transported authentication information (AUTH1USR) to the server.(3) The biometric sensor enters the authentication information (AUTH2USR), which could be fingerprint information, passwords, or other that is used to control access to the device, into the mobile device.(4) The biometric sensor enters authentication information (AUTH3USR), which could be passwords, or fingerprint information, into the mobile device.(5) The mobile device uses channel 1 to process the authentication information and other channels to transmit the device ID and the authentication information (AUTH3USR) to the server.(6) The server compares each user authentication information (AUTH1USR, AUTH1USR) from separate channels with the user ID and the relevant device ID in order to verify the authentication information. The results are transmitted to the mobile device.(7) The mobile device transmits the verification results from the authentication information that are received from the server to the biometric sensor
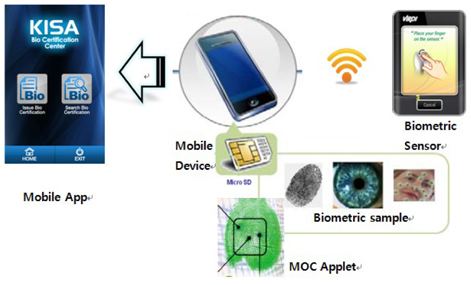
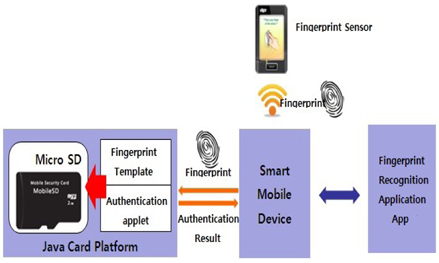
As described in the previous section, with Model 2 of the telebiometric application that uses mobile devices, the mobile device obtains a request from a given application, the device then acquires sample data, compares it with the registered users template, and transfers the result to the requesting application [9]. Model 2 was applied to a sample application, as shown in Figure 5. A type of one-way Model 2 that improves security vulnerabilities to compare and store information in a microSD match on card (MOC) built into the applet was commissioned. Developments in mobile telebiometrics systems made in the process are as follows:
(1) The biometric sensor captures a user’s biometric sample.(2) The biometric sample is converted to a biometric template form, and direct WiFi wireless communication is delivered to the mobile device.(3) The biometric template that is equipped with a fingerprint authentication applet in the SE region of the microSD fingerprint authentication is passed to the applet.(4) The fingerprints template transmitted to the applet is registered with the microSD SE server in order to compare with a biometric reference.(5) User authentication via the mobile app is performed to verify the results.
The process of comparing and storing the biometric mobile device mounted on the microSD SE in the applet to block information leakage by performing a security threat can be fundamentally blocked. The use case illustrates how the concepts discussed throughout this paper can be applied, and such concepts have the following characteristics: - The fingerprint authentication algorithm and the fingerprint information are stored in the microSD SE (in a smartcard). - Moving and mounting services that are free for smartphones. - To ensure the independence of the fingerprint authentication applet, such an applet is independent of the OS and smartphone mode. - In order to store and match fingerprint information in a microSD, the flow of information should basically be removed from all external access, in many cases, such that the information is safe from external security threats. - The fingerprint applet is executed under the control of Java cards, and the real-time environment is verified. - Supports such encryption of biometric information
With microSD SEs that are sufficiently secure to be equivalent to the level of hardware security modules, it is possible to save biometric information in order to provide convenience and high level security. In such a case, these microSDs can be used to perform personal authentication and store biometric information for mobile devices. This is a method suitable for applications to implement a solution for deployment.
This paper is designed to implement a mobile telebiometrics application system that provides a framework for ensuring the security and reliability of the flow of biometric information for telebiometric applications using mobile devices. In addition, we defined twelve telebiometric authentication models and protocols that depend on the configuration of the biometric sensor, the mobile device, and the server.
This paper also specified threats in operating telebiometric systems based on mobile devices and proposed a mobile telebiometric application system that was applied in a real operating environment in order to establish a safe mobile environment for the use of telebiometric systems. In our implementation, we compared and stored the processing of a biometrics mobile device mounted on a microSD SE in an applet to block information leakage by performing a security threat that can be blocked fundamentally. Future work will specify more detailed protocols for cooperation with public-key infrastructures, and a biometric authentication. Moreover, we plan to standardize this topic in ITU-T SG17 Q.9.
No potential conflict of interest relevant to this article was reported.