In information security technologies, encryption has been widely researched [1-17]. In particular, optical encryption techniques [5-16] are helpful to protect the transmitted information. In addition, the speed of the optical encryption is faster than non-optical encryption methods. Double random phase encryption (DRPE) which is the one of the most widely used has been proposed [5]. However, it has a weak point when the decryption keys are used many times without being updated. To solve this problem, DRPE with photon counting imaging techniques has been reported [13]. It considers a photon-limited version of the encrypted distribution such as a Poisson distribution [18-20, 27] in a perfect channel environment. In addition, for 3D objects, three-dimensional (3D) photon counting double-random-phase encryption has been studied recently [26]. In this technique, encrypted data transmission is not considered. It means that a perfect transmission channel is assumed. However, under practical conditions, the transmission channel is not perfect. There are many parameters which cause the noise of the transmitted information.
In particular, the wireless channel causes severe noise and fading effects of the transmitted information. Thus, when the encrypted data is transmitted via a wireless channel, there are a lot of factors such as channel noise, propagation fading, and so on [21-23]. To obtain the correct encrypted data at the receiver, it is necessary to digitally modulate the encrypted information at the transmitter and correctly detect the modulated signals at the receiver [21-23]. In addition, the nonlinear correlation filters may be used to recognize the primary information [24]. For 3D data encryption, computational volumetric reconstruction of integral imaging [25] may be used. Since this technique uses the superposition of all elemental images at a certain depth, the noise effect caused by the wireless channel may be remedied. Therefore, in this paper, we analyze the effects of a wireless channel for optical encryption data using digital modulation and maximum likelihood (ML) detection. Also, we reconstruct and authenticate 3D information at the receiver using computational volumetric reconstruction of integral imaging and nonlinear correlation filters. To the best of our knowledge, this is the first report on considering the wireless channel characteristics of the 3D optical encryption technique.
The paper is organized as follows. First we briefly present the 3D DRPE in Section II. Then, a wireless channel model is presented, and signal modulation and detection techniques are described in Section III. To show the effects of the wireless channel for optical encryption and the authentication of 3D information, experimental results are implemented in Section IV. Finally, we conclude the paper with a summary and future plans in Section V.
II. 3D OPTICAL ENCRYPTION: DOUBLE RANDOM PHASE ENCRYPTION USING INTEGRAL IMAGING
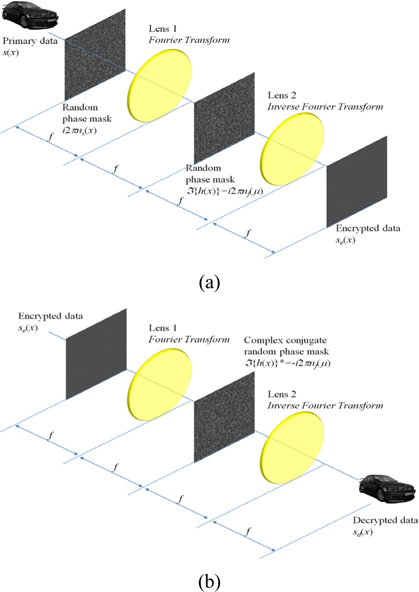
Optical encryption has many advantages such as parallel processing of optical systems, fast processing time, and data handling in various domains. One of the optical encryption methods, double random phase encryption (DRPE), uses two random phase information. Let us consider the encryption of a one-dimensional signal for simplicity. Figure 1 (a) shows the optical schematic setup of DRPE for encryption. Let
where ℑ and ℑ-1 mean Fourier transform and inverse Fourier transform, respectively. By the characteristics of the complex-valued function, encrypted data has amplitude and phase, i.e.,
Figure 1 (b) illustrates the optical schematic setup of DRPE for decryption. To decrypt the primary data, encrypted data as shown in Eq. (1) is multiplied by complex-conjugate of Fourier transform of
In integral imaging, multiple elemental images can be captured by a pickup process [25, 28] and their decrypted elemental images can be obtained by Eq. (2). Then, 3D computational reconstruction can be implemented by the following [25]:
where Δ
III. TRANSMISSION OF OPTICAL ENCRYPTED DATA THROUGH WIRELESS CHANNEL
We consider an elemental image with size
where
where
For digital modulation, each normalized value in Eq. (5) is quantized with 16 uniform levels (i.e., 0, 1, 2, …, and 15), and then the quantized values are respectively mapped into the corresponding 4-bits sequences. For instance, if
In this paper, a wireless channel is assumed to be time-varying frequency-flat Rayleigh fading that is one of the most typical wireless channels [21-23]. Then, with the symbol duration,
where
In order to detect the transmitted signal at the receiver, the maximum likelihood (ML) detection [23] is adopted as follows:
where (
where , is the estimated value for the (
For integral imaging, the amplitudes of encrypted multiple images with size
IV. OPTICAL EXPERIMENT AND SIMULATION RESULTS
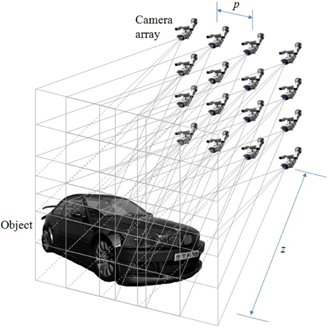
Figure 2 shows the optical setup for recording 3D objects. To record multiple 2D images optically, we used synthetic aperture integral imaging (SAII). We capture 8×8 elemental images which have 2496(H)×1664(V) pixels. The focal length of the pickup camera is 50 mm. The pitch between cameras is 2 mm.
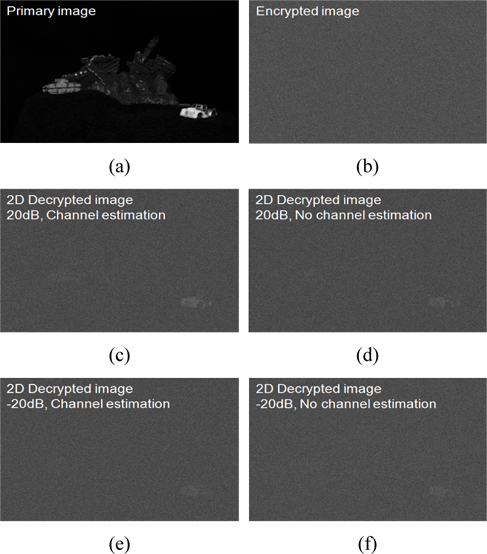
Figures 3 and 4 show the experimental results for 2D/3D optical encryption with wireless channel. In the 3D encrypted data transmission simulation, we used the wireless channel parameters as SNR is -20 dB and 20 dB, the carrier frequency is 2GHz, the receiver speed is 3km/h, the symbol duration,
To compare the performance of our method, the kth-law nonlinear correlation filter [24] and peak correlation energy (PCE) are introduced. The nonlinear correlation filter is designed by the following [24]:
where
Then, to select the optimum
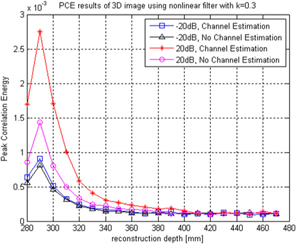
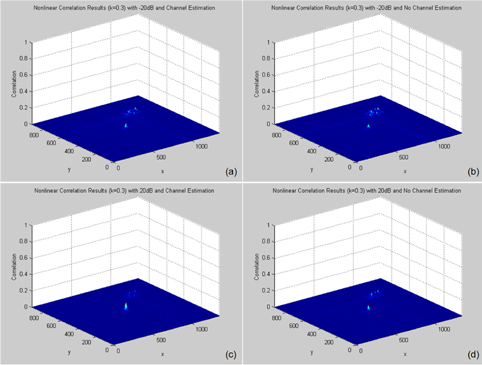
Figure 5 illustrates the correlation results of 3D reconstructed images for each wireless channel environment. The reference reconstruction depth is
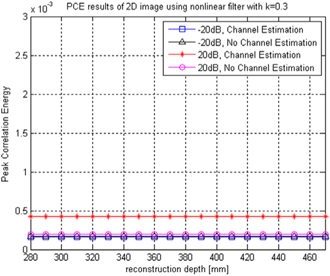
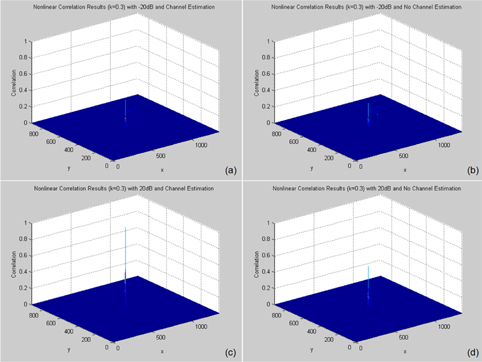
On the other hand, Fig. 6 shows the correlation results of 2D decrypted images for each wireless channel environment. The reference image is the primary image as shown in Fig. 3(a). In Fig. 6, PCE values are 0.1613×10-3 (-20 dB SNR, channel estimation), 0.1720×10-3 (-20 dB SNR, no channel estimation), 0.4243×10-3 (20 dB SNR, channel estimation), and 0.1959×10-3 (20 dB SNR, no channel estimation) at all reconstruction depths, because 2D images do not have any depth information.
Figures 7 and 8 show the nonlinear correlation results (
In this paper, we have presented the optical encryption and information authentication of 3D objects with wireless channel characteristics. The wireless channel environment has several factors such as channel noise, channel fading, and so on. Using digital modulation and ML detection, we have estimated the encrypted information transmitted over a wireless channel and then decrypted the primary image at the receiver. In addition, introducing the computational volumetric reconstruction of 3D integral imaging, 3D information of the primary image can be obtained. This reconstruction method may remedy the residual noise after ML detection. We have proven that our method can effectively mitigate wireless channel effects by using 3D optical encryption technique and carrying out the simulation of wireless transmission. Also, our method shows that the performance of information authentication for optical encryption is improved using nonlinear correlation filters. In future plans, we will consider more wireless channel parameters and study various modulation and estimation methods. In addition, we will apply our method to various three-dimensional imaging or photon counting encryption techniques.