ZigBee is an enabling technology for various applications including home automation and surveillance systems. ZigBee has the advantages of high availability, low power consumption, and low cost, which is ideal for distributed sensor network environments.
However, security management in ZigBee networking is not at a suitable level for applications because the ZigBee standard security requires a huge capacity for storing master keys, network keys, and link keys between each entity. When the size of the network increases, the number of keys exponentially increases. It also does not offer the flexibility to select the destination nodes, for example.
In this paper, we apply attribute-based proxy re-encryption (ABPRE) [1], which re-encrypts a ciphertext with attributes of the new recipients to delegate the capability of decryption and reduce the number of keys, providing a more practical method. To further reduce the computational complexity, we use a constant pairing operation based on ABPRE [2].
In this work, we present a novel method for ZigBee security. Following are the main contributions of the paper. We present an efficient ZigBee security model and the proposed ABPRE provides a security model that distributes overhead. Finally we show a routing security model using ABPRE.
The paper consists of five sections. In Section II, we introduce related works including ZigBee and ABPRE. In the Section III, we propose the ABPRE model as a ZigBee standard. Section IV includes an evaluation report. Finally, we conclude the paper in Section V.
>
A. ZigBee, Sensor Network Standard
ZigBee is designed to be a low cost, power efficient device and provides effective communication within mesh networks. Therefore, it offers reliable and trustworthy network services to users.
ZigBee is based on the IEEE 802.15.4 specification and ZigBee standard. IEEE 802.15.4 defines the physical and medium access control layers of the protocol. The higher layers including the network, application support sub-layer, and ZigBee device objects are described by the ZigBee standard.
One of the most interesting features of ZigBee is the possibility of mesh networking. This extends the network range and provides higher network reliability by creation of new paths in case of network configuration changes. If an end device loses its transmission path to the coordinator, it searches for a new path to the coordinator. Therefore, the ZigBee network maintains an appropriate data transmission rate.
>
B. Security Specification in ZigBee Networks
The ZigBee standard provides data confidentiality by encrypting packets with secret keys using Advanced Encryption Standard (AES) symmetric cryptography.
Three key types are used in ZigBee networks. A master key, which is a long-term security key between two devices, is used for delivery of network and link keys. The second key is a link key, which provides security on the specific link between the two devices. The third key type is a network key used when nodes transmit the information to a member of the network.
Even though ZigBee provides a strong method for protection of information from attackers with symmetric cryptography, ZigBee has restrictions that involve a large number of keys and network keys. In a full mesh network, each node shares each pair of keys with
>
C. ABPRE with Constant Pairing Operations
ABPRE with constant pairing operations is an enhanced version of [1]. To reduce the number of pairing operations, exponentiation is conducted instead of the operation. Therefore, the pairing operation is computed at once at the end.
>
D. Satisfying an Access Structure
In this scheme we consider the access structure consisting of AND gates between positive and negative attributes. Denote the index set of all the attributes as τ. The access structure is represented as ?(+
If +di appears in AS, then i ∈ S;
If -di appears in AS, then i ? S;
SETUP(1
The master key
KGEN (
and for each
ENC (
appears as
otherwise,
It outputs
RKGEN (
and let
For
is the ciphertext of ? under the access structure
REENC (
and
This step checks whether
Next, it computes =
It outputs a re-encrypted ciphertext
Note that
where
DEC (
It checks whether
If
for
Next, it computes
Otherwise, if
then it decrypts
Then it outputs
Otherwise, if it is a multi-time re-encrypted wellformed ciphertext, and then decryption is similar to the above phases.
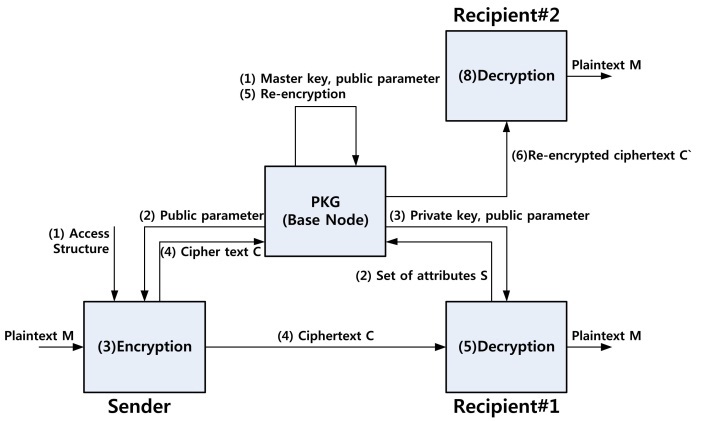
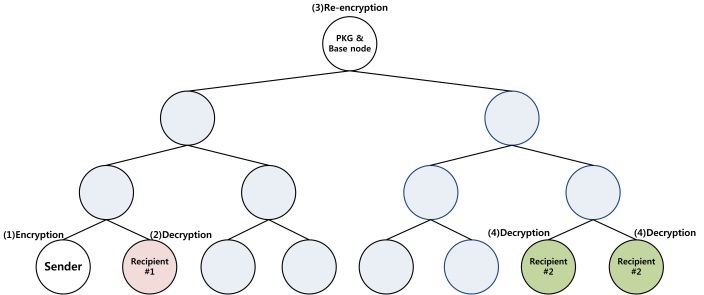
The method is based on the [6] process, which proposes the first form of ZigBee security using ABPRE. In the process, firstly, the sender receives the access structure and public parameters from private key generator (PKG). When the sender needs to transmit the plaintext by executing the encryption process, the data is encrypted with the user's attributes and secret keys. If the recipient is located in the same sub-network or the sender has his attributes, the sender directly transmits the packet to the recipient and then the recipient decrypts the packet with his attributes and public parameters. When the recipient is located in the other network or has attributes which are not in the sender, the sender transmits the packet to the base node. The packet is reencrypted and then is transmitted to the node in the distance. The recipient decrypts the packet with his secret values. If the packet is encrypted several times, the decryption process is also conducted by an equal number of them. The method needs to pass the base node when the recipient is in the other network. Passing the base node, the packet is reencrypted, which ensures that the packet is transmitted using the right path. The detailed process is depicted in Fig. 1.
In Fig. 2, an example of the scenario is described. When the sender wants to send a message to recipient #1, it directly transmits the ciphertextto the destination after encryption. In the case of recipient #2, the sender transmits the packet to the base node. The base node then re-encrypts the packet using recipient #2's attributes. The re-encrypted data is transmitted to recipient #2 and then the data is decrypted with the attributes of recipient #2.
The detailed process of the algorithm is described in Table 2.
The attribute-based proxy re-encryption scheme has the capability of attribute encryption with specific attributes and re-encrypting the message for delegating the capability of decryption to selected users, which enables various features such as the simplicity of group key management and delegation of decryption capability. Comparing the number of keys with other schemes, ABPRE has
A detailed report is presented in Table 2. For practical application, a proposal is required to reduce the computation cost because the scheme claims high overhead including pairing operations. Currently pairing operations over sensor networks take about 1 second (Table 3). Therefore, it is not practical if many pairing operations are needed. In traditional ABPRE, the pairing operation is conducted by a number of attributes. Therefore, it is infeasible to enable the technology over a sensor network.
To solve this drawback, we use a constant pairing operation based on ABPRE [2]. In this method, we must compute two or three pairing operations by conducting decryption. The re-encryption is conducted by a full function node, a base node. Therefore, overhead is reduced in the leaf nodes. Table 4 illustrates the computational complexity of ABPRE. The leaf node needs to conduct the encryption process per each transmission. In the previous method, we had to conduct re-encryption whenever we needed to transmit data to users that were not included in first access structure of the ciphertext by the leaf node. However, in the case of the proposed method, the reencryption process imposes the overhead on the base node, a much more powerful device. Therefore, the computational costs on the leaf nodes are reduced.
Even though the method provides a small number of pairing operations, it is still not a practical method for ATmega128L and MSP430 devices. The pairing operation over sensor nodes should be improved to perform the proposed method.
[Table 1.] Process of encryption and decryption over a sensor network

Process of encryption and decryption over a sensor network
The security strength of the proposed model is based on the user's secret key and attributes. First, if the sender's secret key is not revealed to others, the encryption and decryption process are secure, depending on the CTDH and ADBDH assumption. Secondly, the re-encryption process also demands the user's secret key to allow it to proceed. Even though malicious users might obtain the user's encrypted text, they cannot generate a re-encrypted text because the encryption key is not available for malicious users.
[Table 2.] Performance evaluation of cryptography for ZigBee security [3-6]
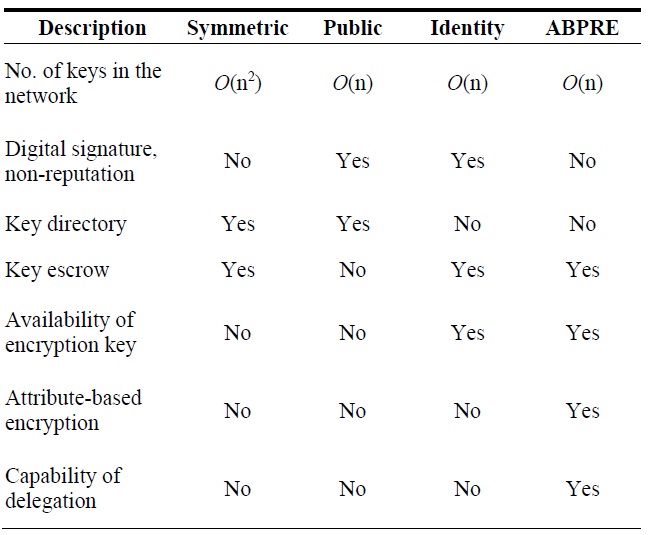
Performance evaluation of cryptography for ZigBee security [3-6]
[Table 3.] Timing table for pairing operations over sensor platform [7]
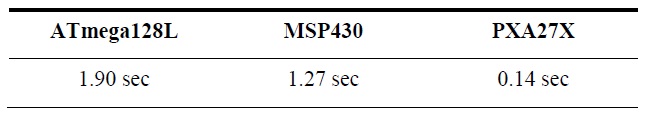
Timing table for pairing operations over sensor platform [7]
[Table 4.] Computational complexity of ABPRE

Computational complexity of ABPRE
In this paper, we propose the novel ABPRE based the ZigBee security model. The method solves the key management problem, provides an attribute-based encryption model, and ensures routing path security. It also has strong features in low cost computation by replacing exponentiation operations for pairing operations and provides a constant number of pairing operations. As a result, the proposed model can be a more practical security model in resource-constrained embedded systems than previous models. However, the method does not show reasonable performance. Future work in faster implementation of the model over various sensor nodes and locating a method for speeding up the model is needed because the current sensor nodes do not show high performance, as described in Table 3.
>
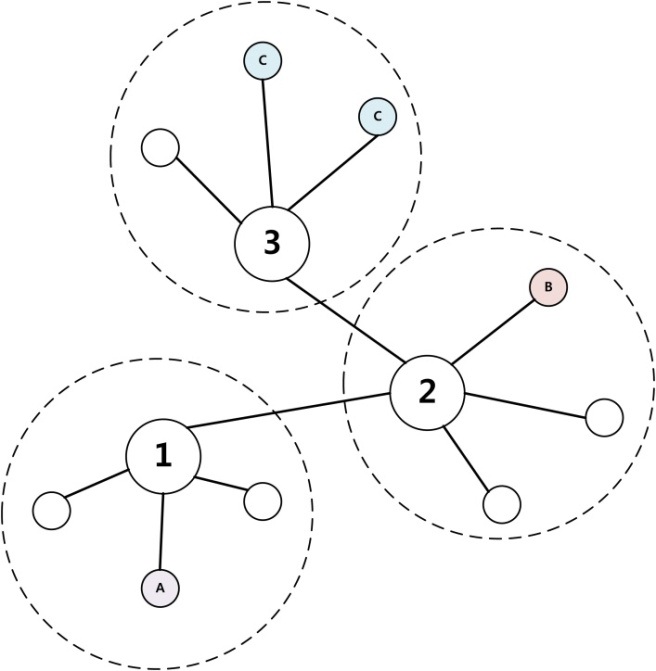
Example: Multi-Hop Encryption Model
If sender ‘A’ wants to transmit data to ‘B’ and ‘C’, ‘A’ encrypts the data with attributes of base node ‘1’ and then sends it to ‘1’. Base node ‘1’ sends a ciphertext to ‘2’. First ‘2’ sends the received data to ‘3’ and ‘2’ re-encrypts the data with attributes of ‘B’ and then sends attributes. After receiving the data, ‘3’ also conducts the same procedure, which is computed in base node ‘2’.

![Performance evaluation of cryptography for ZigBee security [3-6]](http://oak.go.kr/repository/journal/11847/E1ICAW_2012_v10n4_343_t002.jpg)
![Timing table for pairing operations over sensor platform [7]](http://oak.go.kr/repository/journal/11847/E1ICAW_2012_v10n4_343_t003.jpg)