Identity-based cryptography encrypts the message with the user’s identity including the name and e-mail address. An identity-based encryption (IBE) scheme can restrict an authority to indicate the identity of the recipient [1, 2]. Attribute-based encryption (ABE) was published by Sahai and Waters [3]. Unlike IBE, the message is encrypted with attributes, such as gender, age, and affiliation, so ABE schemes can designate the recipients by assigning common attributes of others. ABE consists of two policies. The first is the key policy ABE (KP-ABE) in which each private key is associated with an access structure [4]. The other scheme is the ciphertext policy ABE (CP-ABE), in which a ciphertext is associated with an access structure [5-7]. The attribute-based proxy re-encryption scheme (ABPRE) extends traditional proxy re-encryption to its attribute-based counterpart. Therefore, the capability of delegation is transferred to the designated users [8]. However, the previous ABPRE does not provide a constant length of message and number of pairing operations. Recently, a constant ciphertext length based CP-ABE was proposed by Emura et al. [9]. The computation cost and ciphertext length were reduced significantly compared to previous papers. However, the encryption scheme over ABPRE has not been proposed yet. For this reason, in the present paper, we propose a new constant computation-based ABPRE. The scheme utilizes the capability of delegation with constant pairing operations.
The rest of this paper is organized as follows. In section II, we describe ABPRE. In section III, preliminaries such as bilinear map and complexity assumptions are introduced to support the construction and the security proof. In section IV, our new ABPRE scheme is introduced and then we analyze security model and computation performance. Finally the conclusion is drawn in section V.
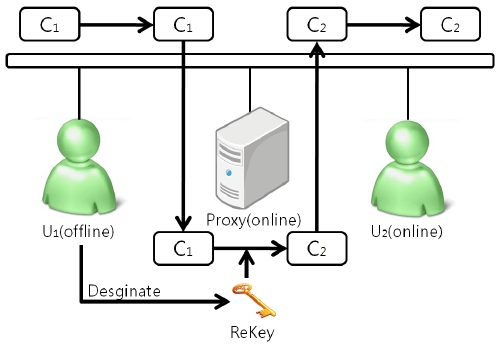
In ABPRE, a user can re-encrypt the ciphertext using a re-key. Detailed relationships are shown in Fig. 1. First
The ABPRE scheme is illustrated in [8, 10]. An ABPRE scheme is comprised of six steps including SETUP, KEYGEN, RE-GEN, ENC, RE-ENC, and DEC.
SETUP: The setup algorithm takes no input other than the implicit security parameter. It outputs the public parameters
KEYGEN (
RE-GEN (
ENC (
RE-ENC (
DEC (
In this section, some definitions which are the basis of attribute-based encryption schemes, including our scheme, are presented.
Definition 1. Bilinear groups and a bilinear map are defined as follows:
Bilinearity: For any
Non-degeneracy:
Note that
Definition 2. Complex Triple Diffie-Hellman (CTDH) problem. Let
as inputs, output
Definition 3. Augment Diffie-Hellman (ADH) problem. Let
as inputs, output
Definition 4. The CTDH assumption holds in
with non-negligible advantage, where random numbers
The CTDH problem is more difficult than the ADH problem; if given the input of the ADH problem
, we could select
The CTDH problem is the basis of the master key security in our scheme.
Definition 5. Augment decisional bilinear Diffie-Hellman (ADBDH) problem. Let
as inputs, output 1 if
Definition 6. The ADBDH assumption holds in
with non-negligible advantage, where
IV. ATTRIBUTE-BASED PROXY RE-ENCRYPTION WITH CONSTANT PAIRING OPERATION LATENCY
We adapt a constant number of pairing operations to a previous ABPRE scheme [8]. Whenever the attribute is decided in the scheme, to reflect the attributes, we need to compute the pairing operation with its designated attributes. To reduce the number of pairing operations, we reduce the pairing operation by using an exponential operation which can easily calculate the summation of the exponent. Therefore, we calculate the exponent and then compute the pairing operation just once.
>
B. Satisfying an Access Structure
In this scheme we consider the access structure consisting of AND gates between positive and negative attributes. Denote the index set of all the attributes as
If +di appears in AS , then i ∈ S ;
If ?di appears in AS , then i ? S .
SETUP (1
The master key
KGEN(
and for each
ENC(
For
RKGEN(
and let
For
It outputs
REENC(
and
This step checks whether
Otherwise,
It computes
and
Next it computes
It then computes
It outputs a re-encrypted ciphertext
Note that
where
DEC (
. It checks whether
If
, for
Otherwise,
It computes
and
Next it computes
It outputs
Otherwise, if
, then it decrypts
Otherwise, if is a multi-time re-encrypted well-formed ciphertext, then decryption is similar with the above phases.
Since our scheme is an expansion of a previous ABPRE scheme in [8], the security proof is based on previous proof in [8] and we also extend it to our scheme.
Theorem 1: When the ADBDH assumption holds in (
Proof: In this section, we show that SS-CPA-ABPRE meets the requirements in terms of the ADBDH assumption.
We suppose that an adversary wins the SS-CPA-ABPRE game with a non-negligible advantage ε . A simulator
We first suppose the challenger set the groups
Init:
i ∈ I +* , Ti = gαi ,Tn+i = Bβi ,T2n+i = Bγi ;
i ∈ I ?* , Ti = Bαi ,Tn+i = gβi ,T2n+i = Bγi ;
Otherwise , Ti = Bαi ,Tn+i = Bβi ,T2n+i = gγi.
Phase 1: An adversary
Otherwise,
from the oracle and outputs
.
It selects a random
For
, in which
According to the security game, if
.
Otherwise,
.It computes
, and
Next it computes
Finally, it computes
It outputs a re-encrypted ciphertext
Challenge:
Phase 2: Same procedure as Phase 1.
Guess: A tuple was given from
According to [3], the advantage of the simulator to output a correct
Theorem 2: If the CTDH assumption holds in
Proof: The simulator
and a challenge index set
Init:
Key generation oracle:
For every
Denote
and
For
else
For
else
For,
It outputs a secret key
Rekey generation oracle:
Select
at random for each
Implicitly set
and
for
Compute
for
If
Else if
Else if
Output
where
Re-encryption oracle:
-For
- +
where
[Table 1.] Computational time of each algorithm
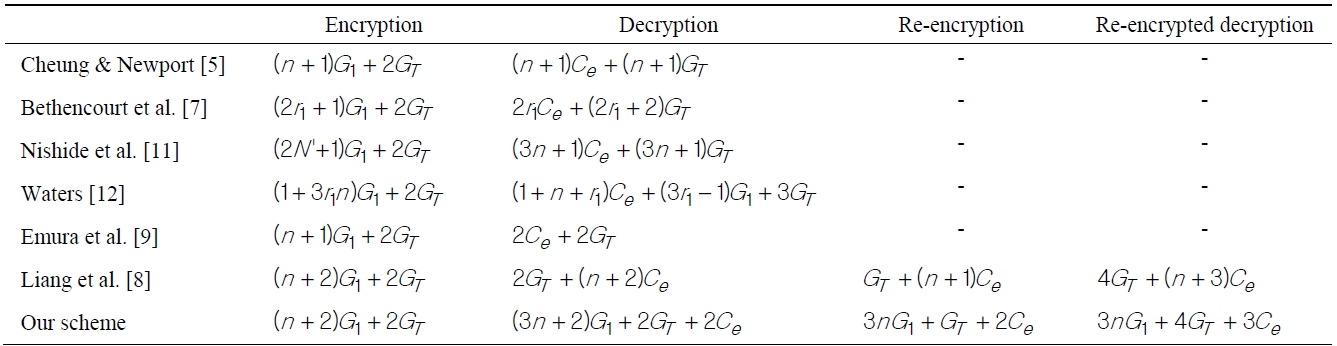
Computational time of each algorithm
- ?
where
- Otherwise,
where
It outputs a secret key
If it is a valid secret key,
The decryption oracle is straightforward, since the secret key and re-key could be correctly generated from the Key generation and Rekey generation oracle.
It outputs
and solves the CTDH problem.
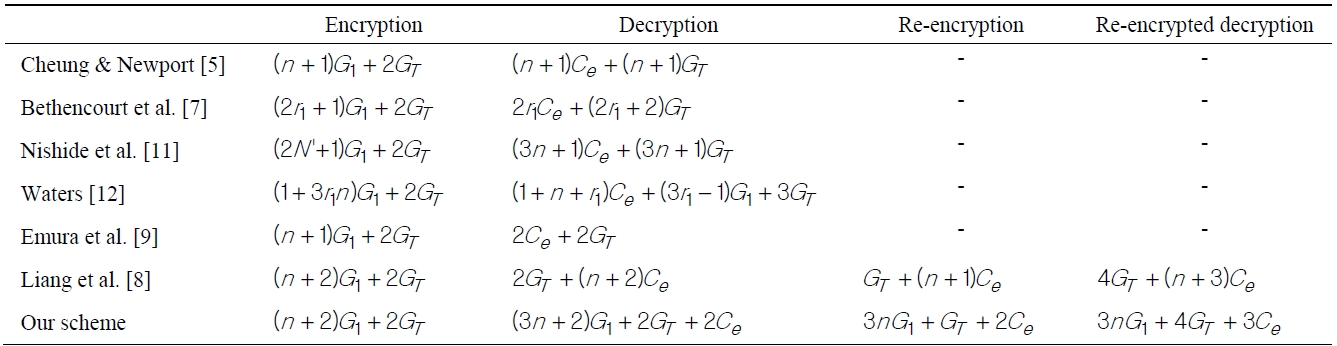
Majority of ABE or ABPRE schemes require computing a number of pairing operations to generate the ciphertext depending on unique attributes but the computational cost of a pairing operation is much higher than other operations. For this reason, a small number of pairing operations is important factor for efficient cryptography algorithms. In 2009, Emura et al. [9] presented a constant length of pairing operations in an ABE scheme. This scheme is the motivation of our algorithm. In our scheme, we propose an expansion algorithm of ABE, ABPRE maintaining a constant pairing operation. A comparison of computation complexity is illustrated in Table 1.
The notation
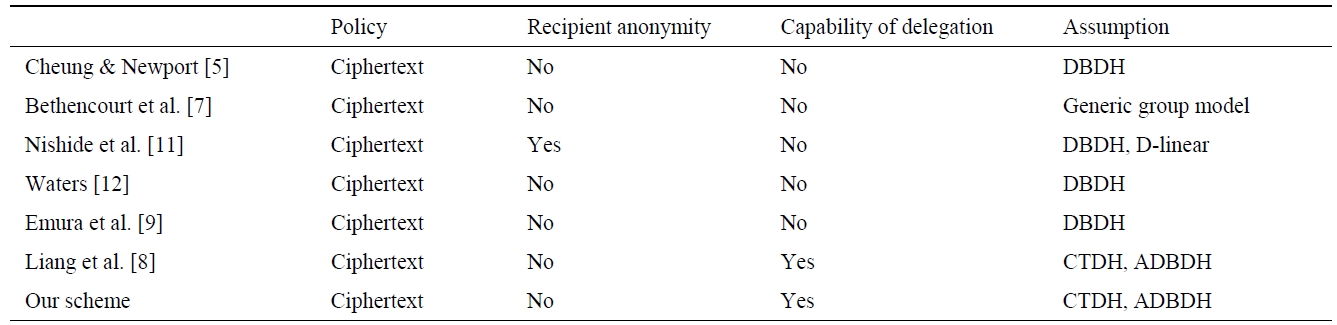
[Table 2.] Some properties of attribute-based encryption schemes

Some properties of attribute-based encryption schemes
Let
ext and a set of attributes associated with the secret key, respectively. Let
be the total number of possible statements of attributes.
Comparison of some properties including policy anonymity, capability of delegation, and security assumption is illustrated in Table 2. All schemes follow the ciphertext policy. Nishide et al. [11] scheme only provides recipient anonymity. Capability of delegation is a strong feature of ABPRE-based schemes. Therefore, we can empower designated users with the capability of decryption. Our security assumption is based on CTDH and ADBDH. This provides a selective-structure chosen to be plaintext secure and master key secure.
In the paper, we present the ABPRE with constant number of pairing operations. The scheme is motivated from previous CP-ABE by computing constant length and number of pairing operations. Compared to previous ones, our proposal has the strength of its capability of delegation. Through the feature, we can empower designated users to decrypt the ciphertext re-encrypted with a new access structure. The scheme can be adapted to various applications including e-mail forwarding and distributed file systems.
Future work includes how to implement the scheme efficiently in various environments such as traditional computing environments and embedded systems (wireless sensor network, near field communication, and radio frequency identification).